Some of the words
All cases are authorized legal compliance projects. Do not carry out any penetration attacks without authorization. Please abide by the network security law
Last year dug a mall a number of vulnerabilities, time has passed more than a year, take out to share some basic operations.
I'm just going to put in some interesting logic holes here, sensitive information is desensitized.
Logic can be found mainly in the familiar with the target function of the vulnerability of the cases, observation data packets, careful observation and bold attempt to change package, finally in fact there is a problem or can be found, this mainly by the recent discovery of logical loopholes case to make a review, this article related the packet has thick code processing, if the bosses read causing inconvenience locations.
The target is a shopping mall, commodity selection, ordering, payment, the whole process function is very perfect, basically is also complete, the website also has WAF, therefore, at that time, the final discovery of the loophole mainly logic loophole.Actual Found
Specific store appearance would say not to put, more sensitive, thank the teacher understanding (don't try to search what is this mall, thinking of general, only the mall has logged off) since it is market, since have to buy things, most early ideas can may be thinking about for the price or quantity changes, such as a low price to buy other goods, For example, the quantity of goods is changed from 1 to 99 pieces and the price of 1 piece is successfully purchasedModify the purchase quantity
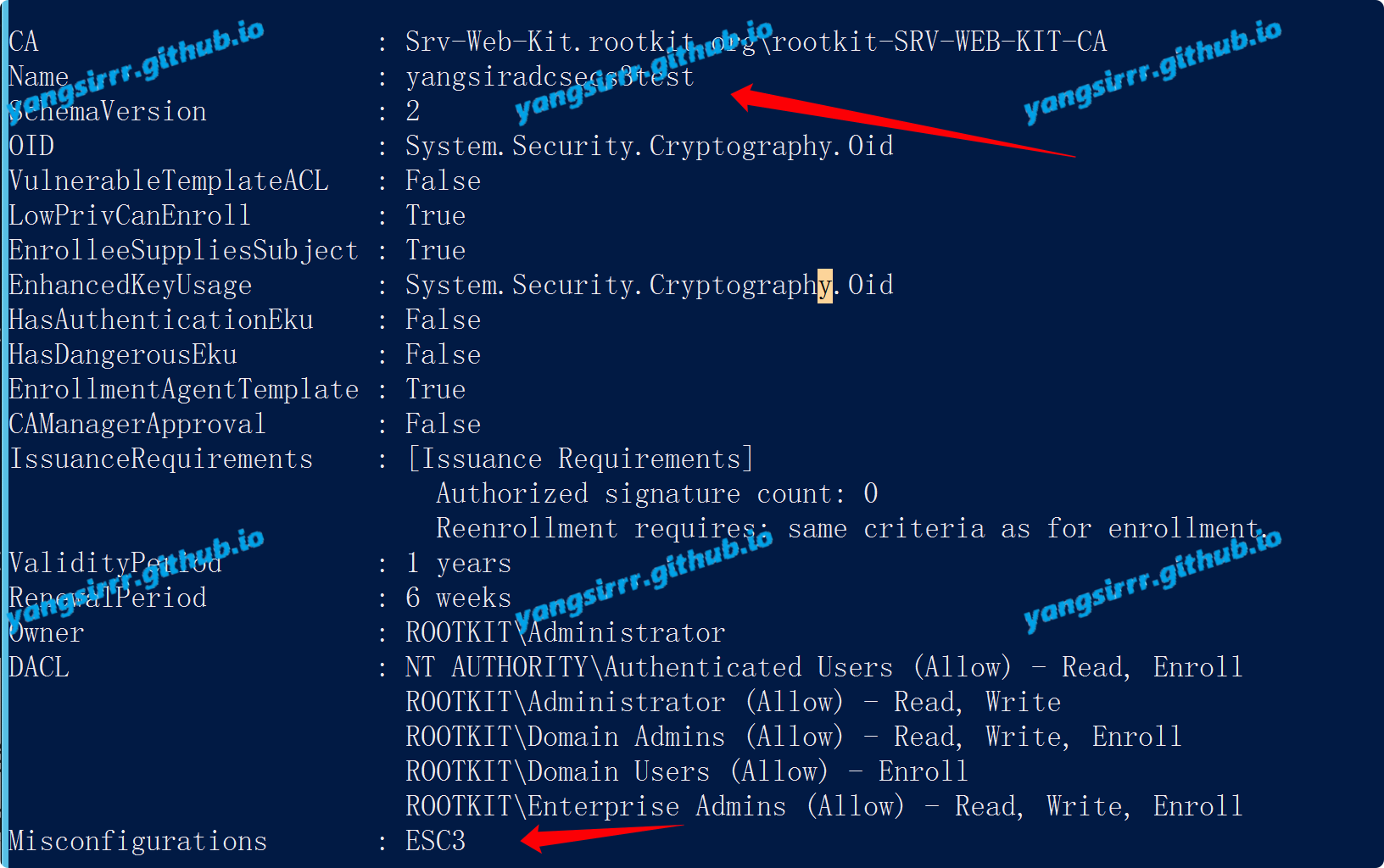
A product page (red is my code, afraid of someone recognize), can be found to be a wholesale, the number of people is limited to 50-2000, and the normal order is from 50 to start, limit the number is not less than 50: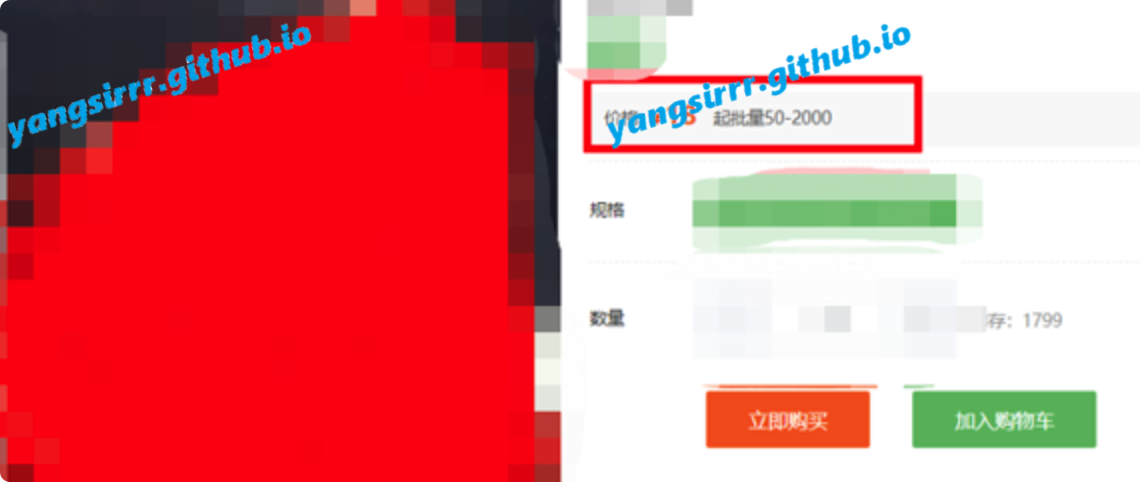
From the point of view of finding a problem, is there a problem if the purchase is successful in quantities below 50?
After capturing the order submission packet, the whole shopping mall packet is not encrypted, which is convenient for us to further observe and modify the packet. Here we can find that the goods_num parameter is used to pass the parameter:
Release after directly changing to 1:
It is found that the quantity on the order check page is also 1, and the price is also the price of 1 piece:
There is actually a settlement button in the order check office (screenshot not taken, will be mentioned later). After clicking the settlement button, the packet is truncated, and it is found that the goods_num is 50 again, so there should be layer check
Here, I still change the quantity to 1 and place the order, jump to the cashier, and the price is the price of 1 commodity + freight:
Enter the payment module of a payment function, which is also 25.5. There is a qr code of payment below, and I don't have a screenshot here:
Some people might say it's not very useful to make it smaller, but I also want to make it bigger, but if I look at the goods in the mall, let's say the inventory is 100, the maximum number of goods is also 100, and it's almost always the same, but let's say there's an event where each person is limited to 5 items and the inventory is 100, Can we modify the actual purchase quantity to collect wool according to the product quantity bypass??Get any user order
After placing the order, there must be a place to check our order, so I went to the background, looked at the order and started to hate each other, randomly looking for an order in the test process:
Direct package change:
Easily found a million order data, it must be high risk, here go through, other orders can be obtained in the same way: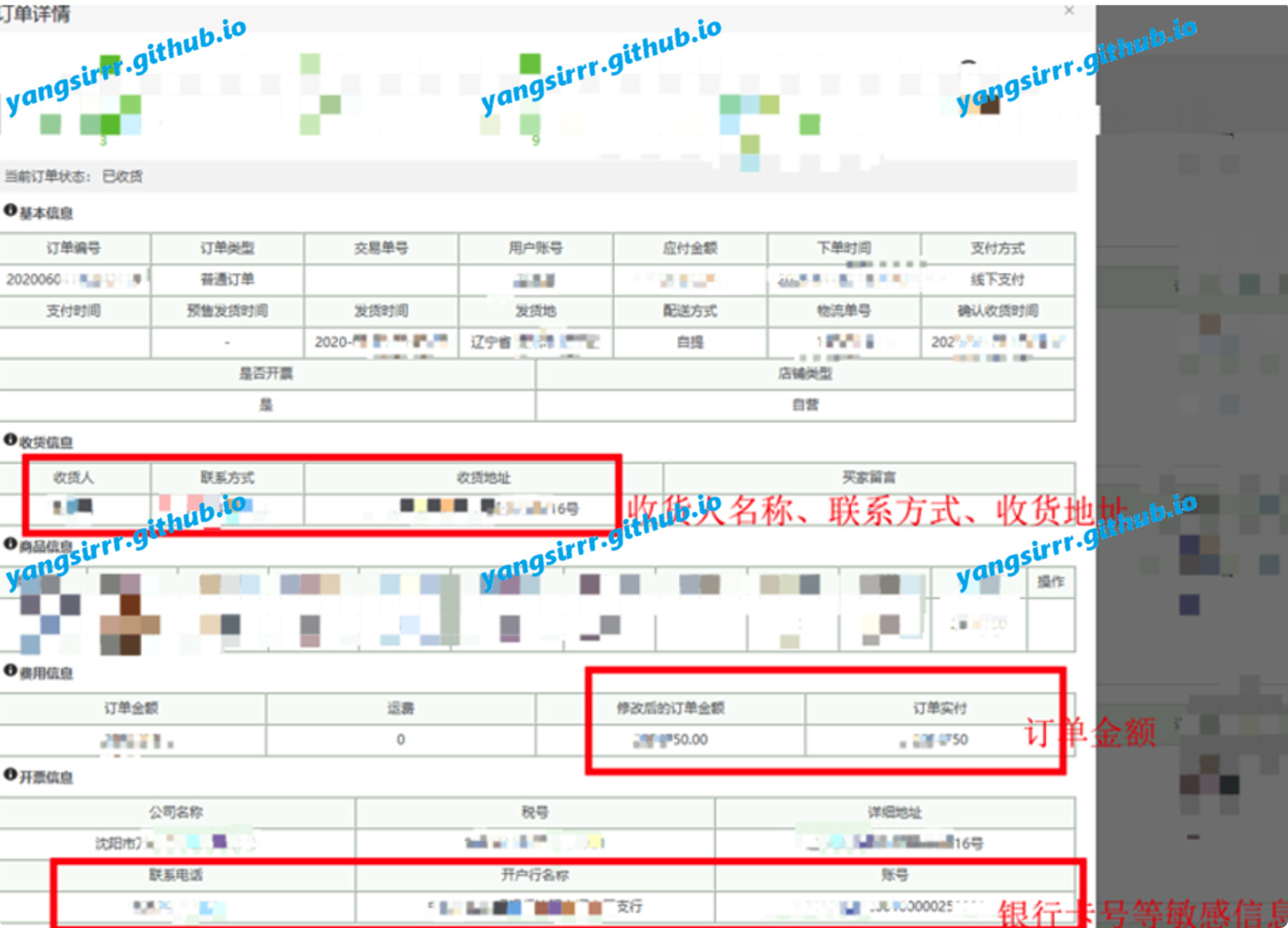
The above found the order, in fact, there is a lot of data, such as consignee information, name, phone number, address, order amount, company information, name, tax number, address, card number, opening bank and so on......Get the receiving information of any user
I will not put the specific page of the individual center, more sensitive, first of all confirm the current user receiving address is as follows, you can fill in at will: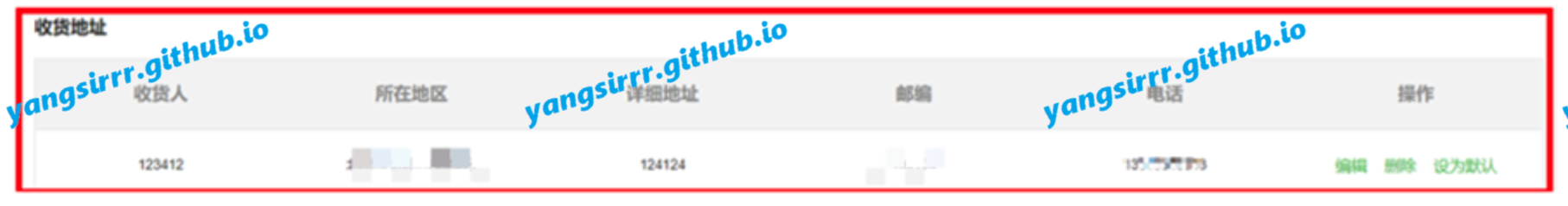
Look for a product in the merchandise department:
The delivery address of the order can be found to be my personal test address:
Then enter the settlement function and truncate the packet:
The above id is directly changed to any other value:
According to the vulnerability explained previously, after placing the order, we actually enter the settlement page. We don't need to immediately settle on the settlement page, but open another page to enter the personal center. In fact, it can be found that the consignee has become the consignee corresponding to the addressid I modified -- XX Jie: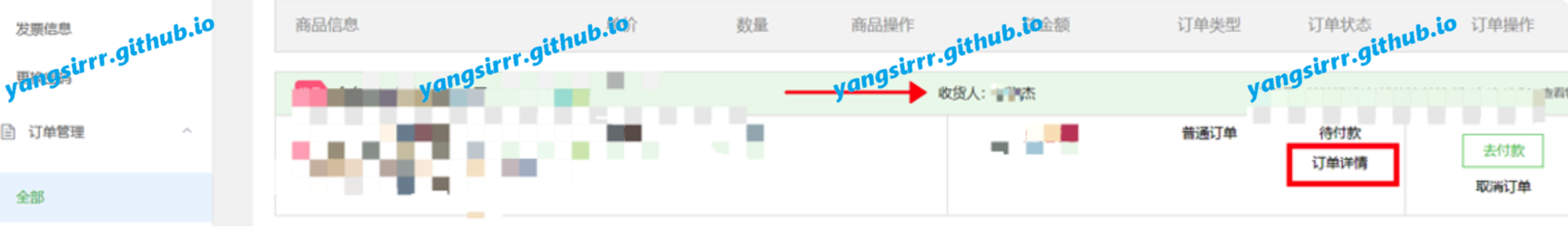
Order details can obtain other people's detailed harvest data, consignee, contact information, harvest address and so on:
Cancel any user order
This is the real deal, with burpSuite traversing the order number to enable the user to cancel the order. Just imagine, the shopping promotion held by the mall is targeted by malicious people, and normal users place orders. As a result, malicious users keep using the interface of order cancellation to iterate over parameters, and normal users may purchase goods before entering the payment page, the relevant order has been canceled... Will there be a tragic scene of consumer abuse?
A User's personal page, order (ending with 123) Click to cancel the order:
Also use the order_id:
Given the parameter 995 of the order, click the order cancellation button to replace user B, and change the parameter order_id to 995 of user A: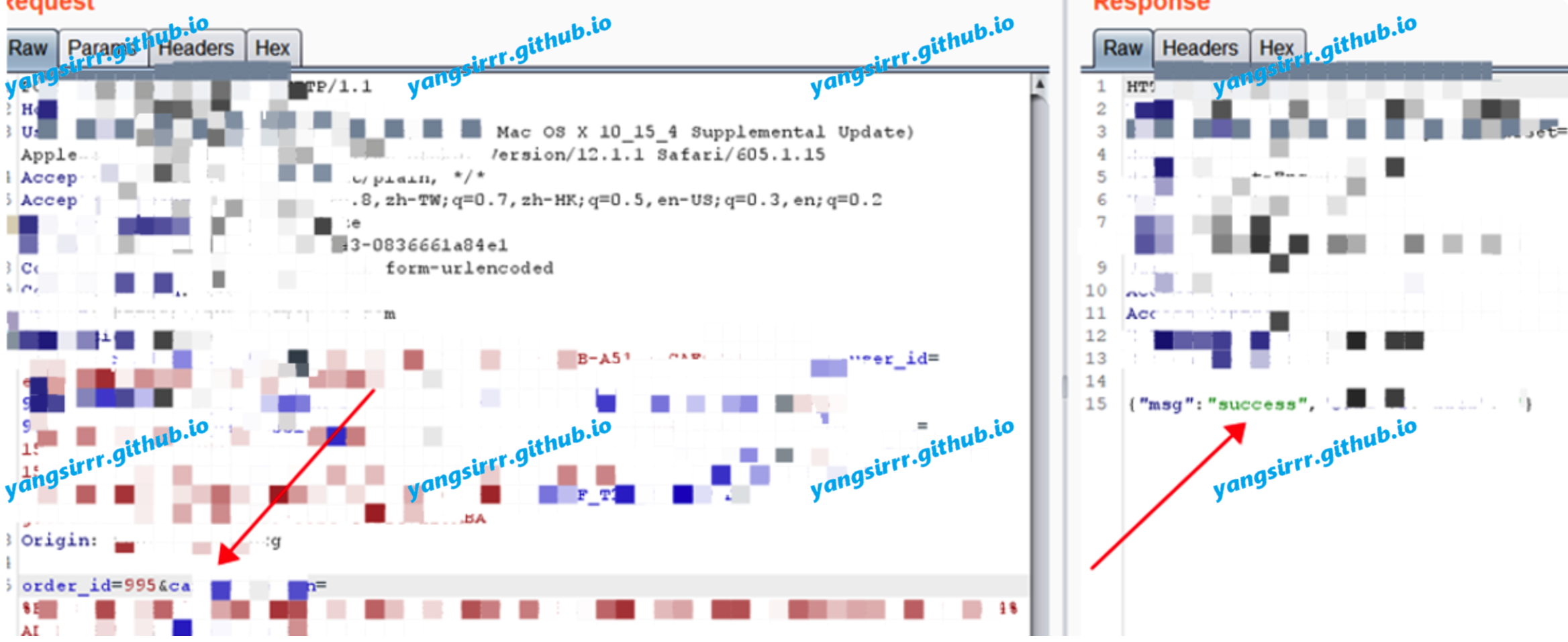
After the data package is released, it returns to user A and confirms that the order (ending with 123) has been cancelled. The following shows that the transaction has been cancelled:
Get logistics data
As for the order_id parameter, I found that the same parameter was used when I checked the logistics on my personal page, and there was unauthorized access, so I could directly obtain the logistics details of any user's order, and some order information was intercepted: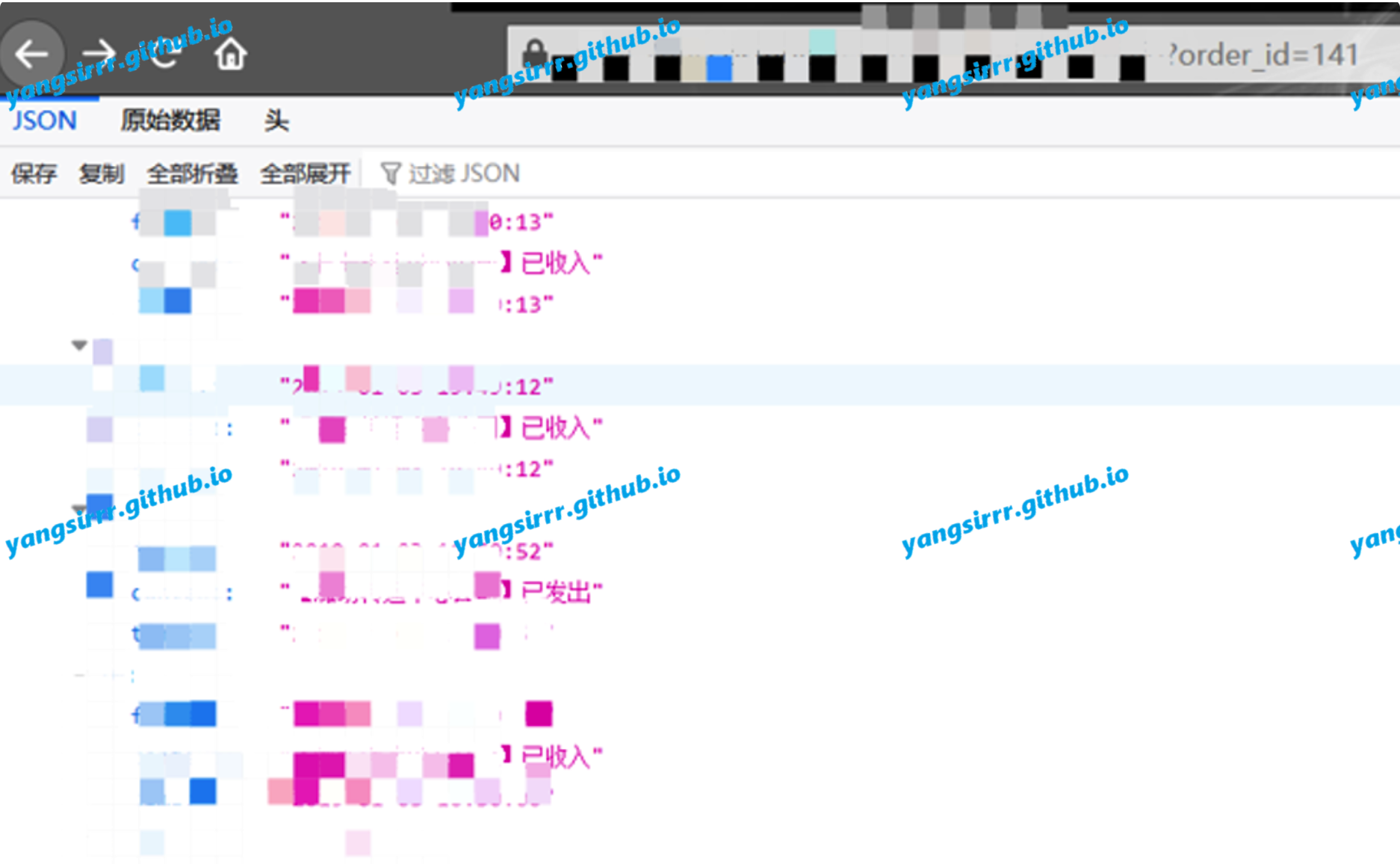 ```
```
Use the id to get more information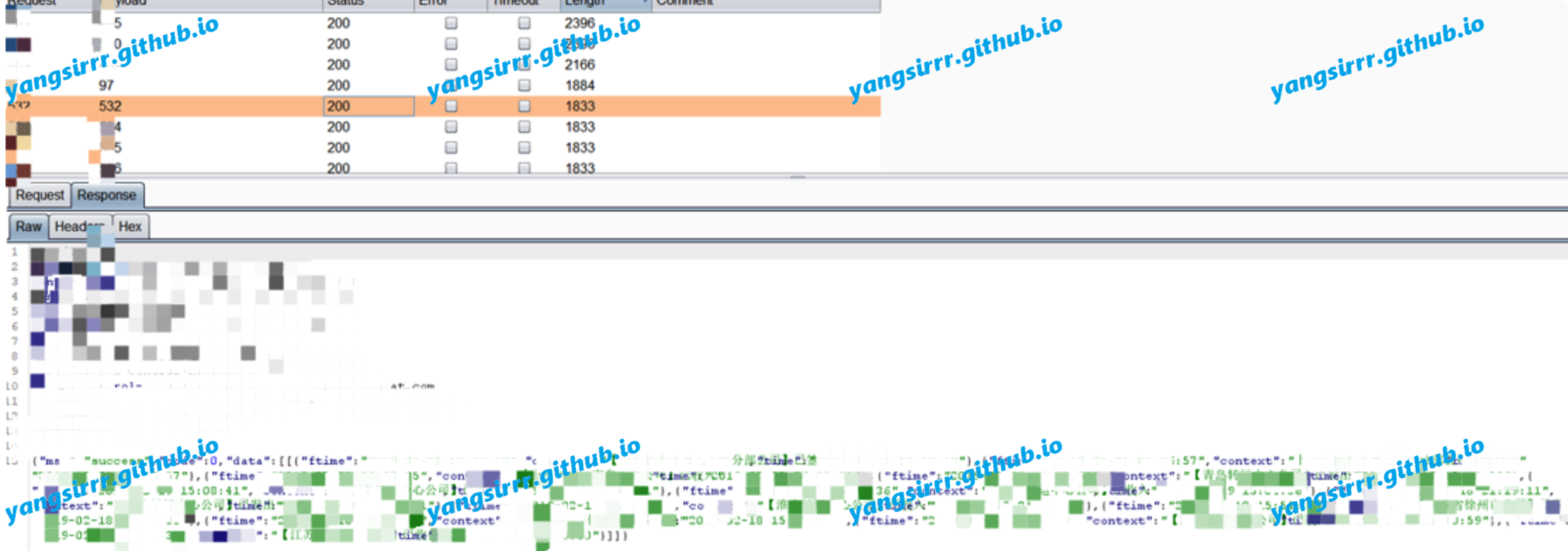
Product malicious brush praise
There is also a "like" function for shopping goods, currently 41:
Normally, a single user can only like it once, but I was able to give it a thumbs-up:
After clicking the "Like" button, the packet is truncated and the batch replay is successful in a short time: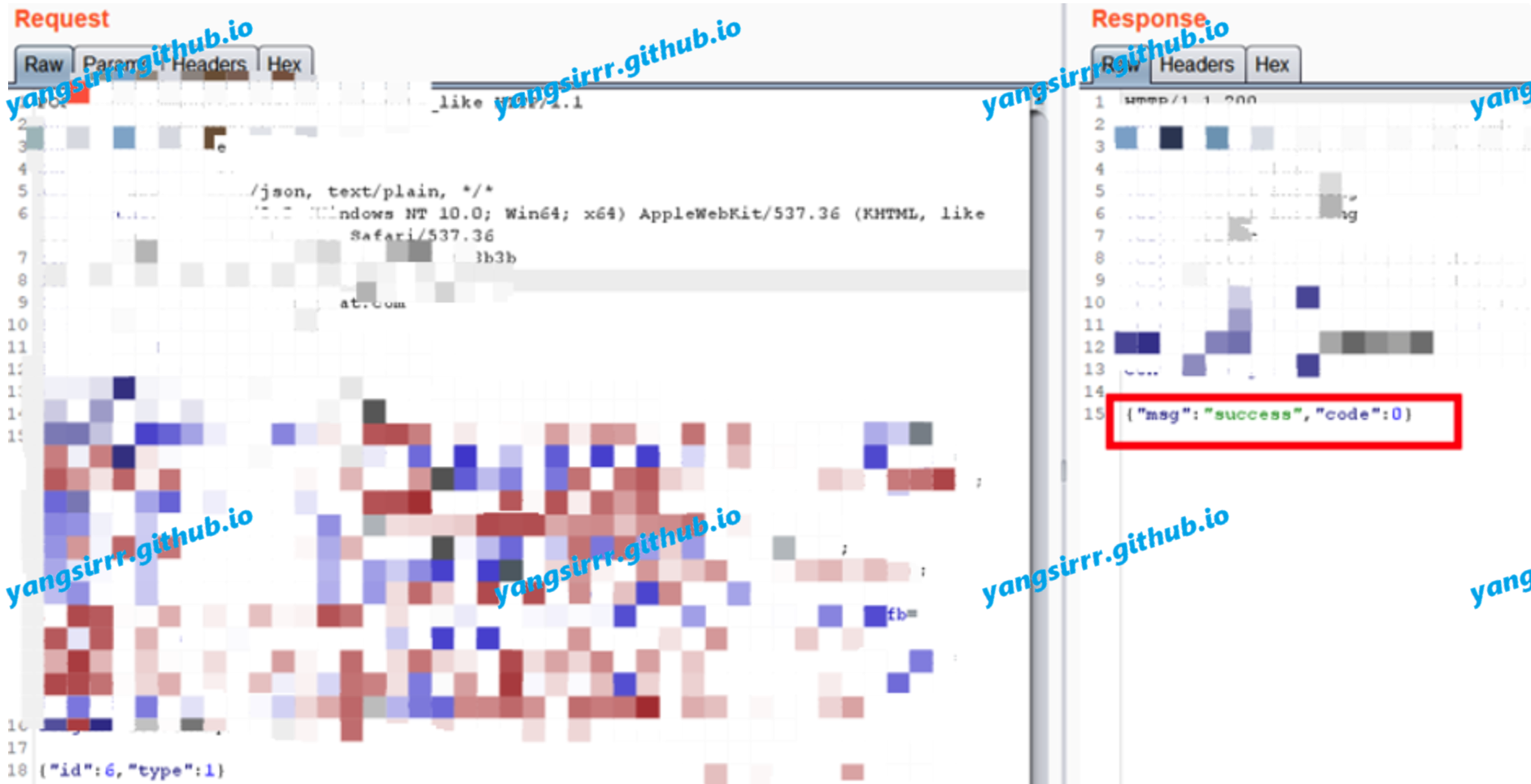
View the product again already 53 likes:
When a customer buys a product, if the customer chooses to push the product according to the number of likes, will the malicious merchant be able to take the top spot? !