Some of the words
We all know that there is a PostSQL database under MSF for actual use, which stores host and vulnerability information, as well as a way to store all kinds of account passwords, namely CREDS
Creds contains the target host, account, password and other credentials information, if you like me have been open database, blasting out a lot of results, each time it is not convenient to find, then this time will record some simple filtering, so as to improve efficiency and save time
Actual use
Basic use, start the database
msfdb init
Viewing credentials
creds
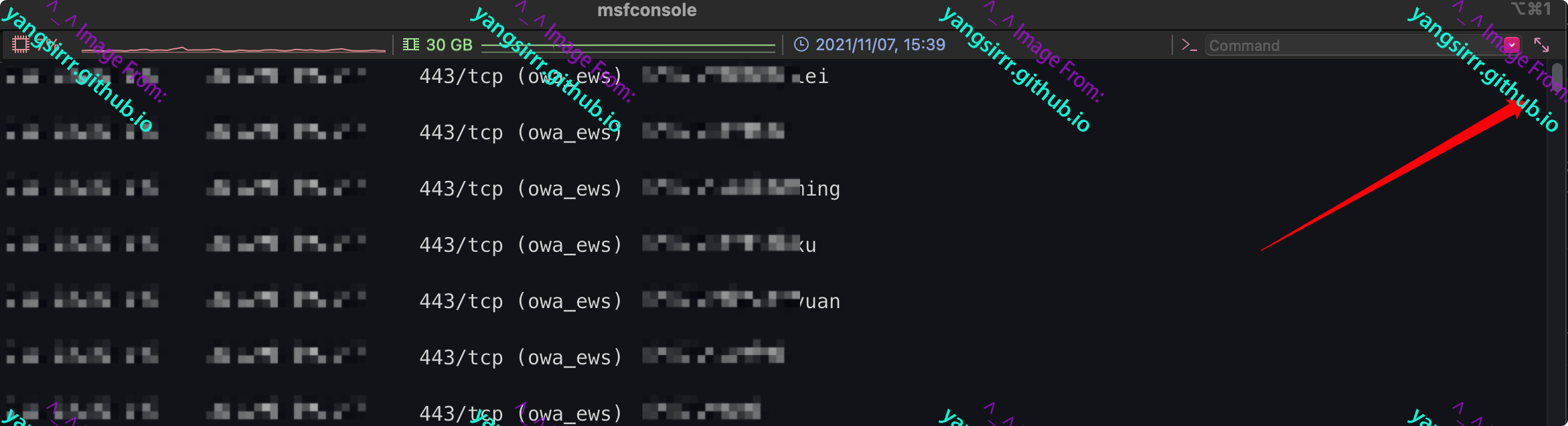
It will be much more difficult to identify and search a single target through a large amount of data information generated after blasting. Here creDS is used for relevant sorting, so as to quickly search our target users
Some ways like this
Username
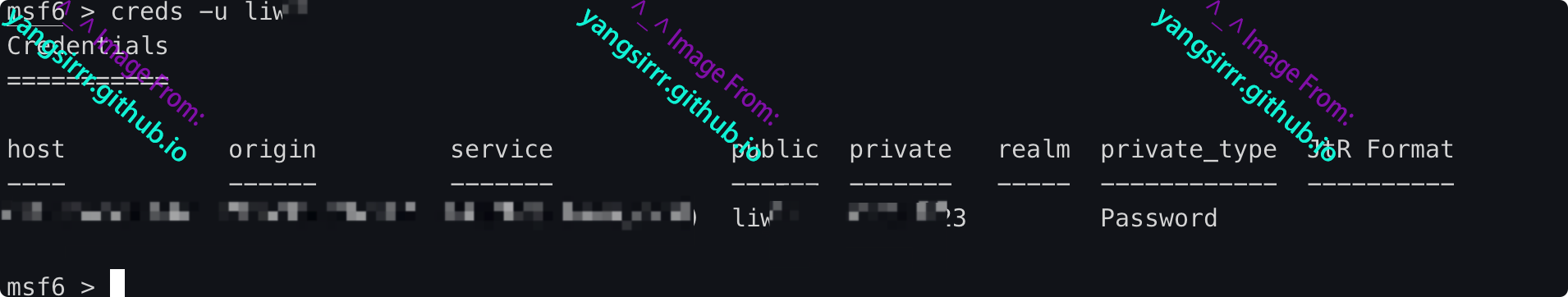
Filter by user name
msf6 > creds -u liXXXX
Credentials
===========
host origin service public private realm private_type JtR Format
---- ------ ------- ------ ------- ----- ------------ ----------
X.X.X.X X.X.X.X 443/tcp (owa_ews) liXXXX XXXXXXXXXXXX3 Password
Type
Filter by type
msf6 > creds -t *
[-] Unrecognized credential type * -- must be one of password,ntlm,hash,afs,bf,bf-opencl,bfegg,bsdi,crc32,des,django,dmd5,dominosec,dragonfly3-32,dragonfly3-64,dragonfly4-32,dragonfly4-64,drupal7,dummy,dynamic_n,epi,episerver,gost,hdaa,hmac-md5,hmac-sha1,hmac-sha224,hmac-sha256,hmac-sha384,hmac-sha512,hmailserver,ipb2,keepass,keychain,krb4,krb5,lm,lotus5,md4-gen,md5,md5crypt-opencl,md5ns,mediawiki,mscash,mscash2,mscash2-opencl,mschapv2,mskrb5,mssql,mssql05,mysql,mysql-sha1,mysql-sha1-opencl,nethalflm,netlm,netlmv2,netntlm,netntlmv2,nsldap,nt,nt-opencl,nt2,odf,office,oracle,oracle11,osc,pdf,phpass,phpass-opencl,phps,pix-md5,pkzip,po,pwsafe,pwsafe-opencl,racf,rar,raw-md4,raw-md4-opencl,raw-md5,raw-md5-opencl,raw-md5u,raw-sha,raw-sha1,raw-sha1-linkedin,raw-sha1-ng,raw-sha1-opencl,raw-sha224,raw-sha256,raw-sha384,raw-sha512,raw-sha512-opencl,salted-sha1,sapb,sapg,sha1-gen,sha256crypt,sha512crypt,sha512crypt-opencl,sip,ssh,ssha-opencl,sybasease,trip,vnc,wbb3,wpapsk,wpapsk-opencl,xsha,xsha512,xsha512-opencl,zip
msf6 > creds -t ssh
Credentials
===========
host origin service public private realm private_type JtR Format
---- ------ ------- ------ ------- ----- ------------ ----------
msf6 >
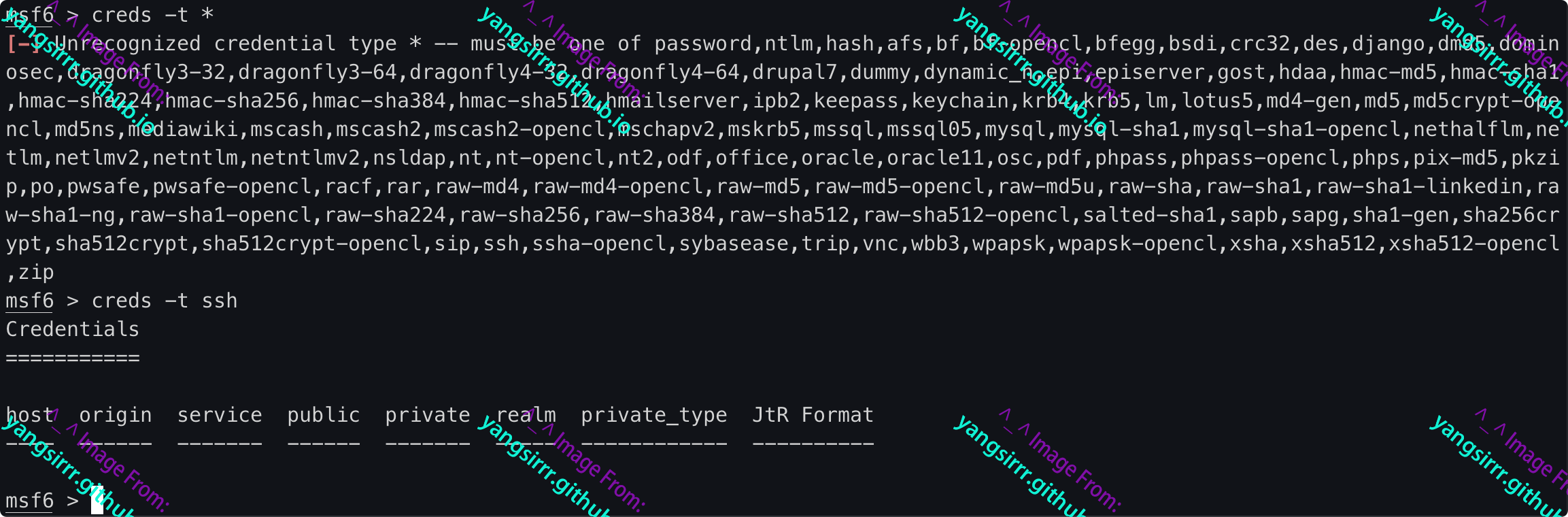
msf6 > creds -t ntlm
Port
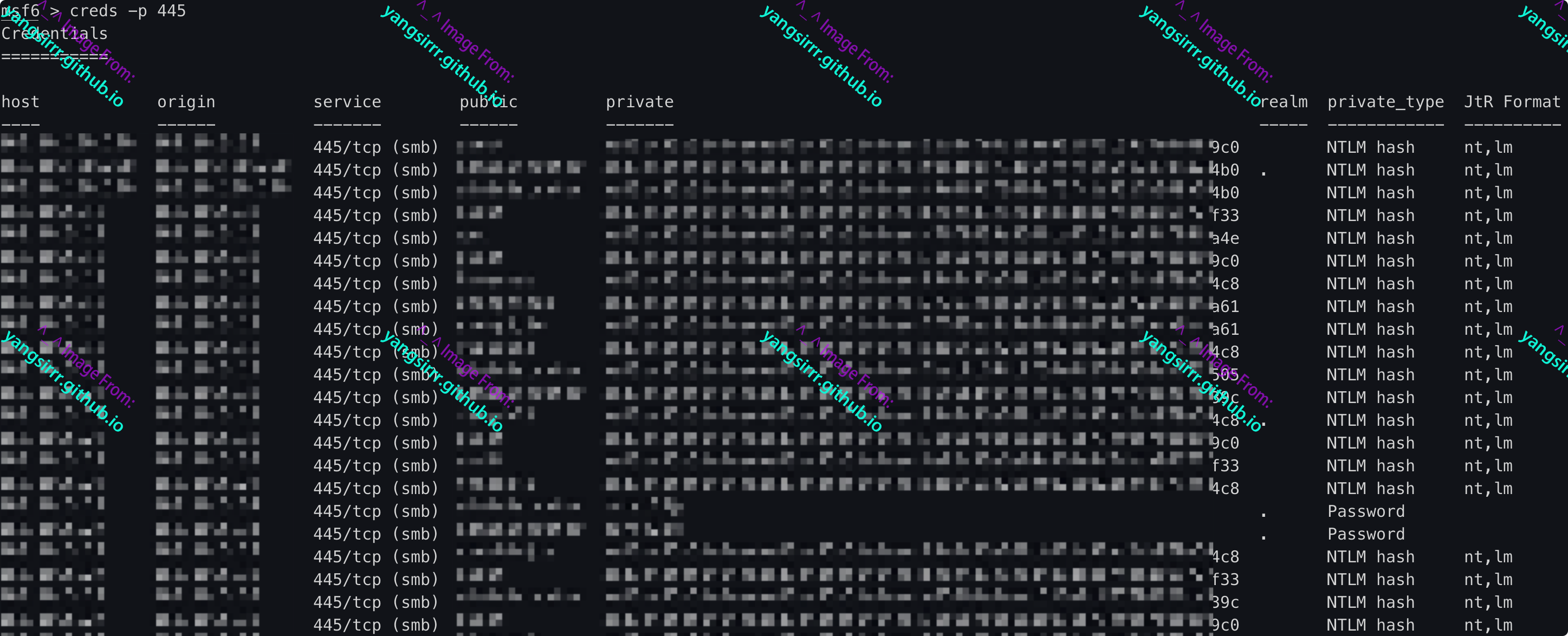
Filter by port
msf6 > creds -p 445
IP
Filter by ip
There are two ways to do this in the help information
creds 1.2.3.4/24 # Return credentials with logins in this range
creds -O 1.2.3.4/24 # Return credentials with origins in this range
Here's an example
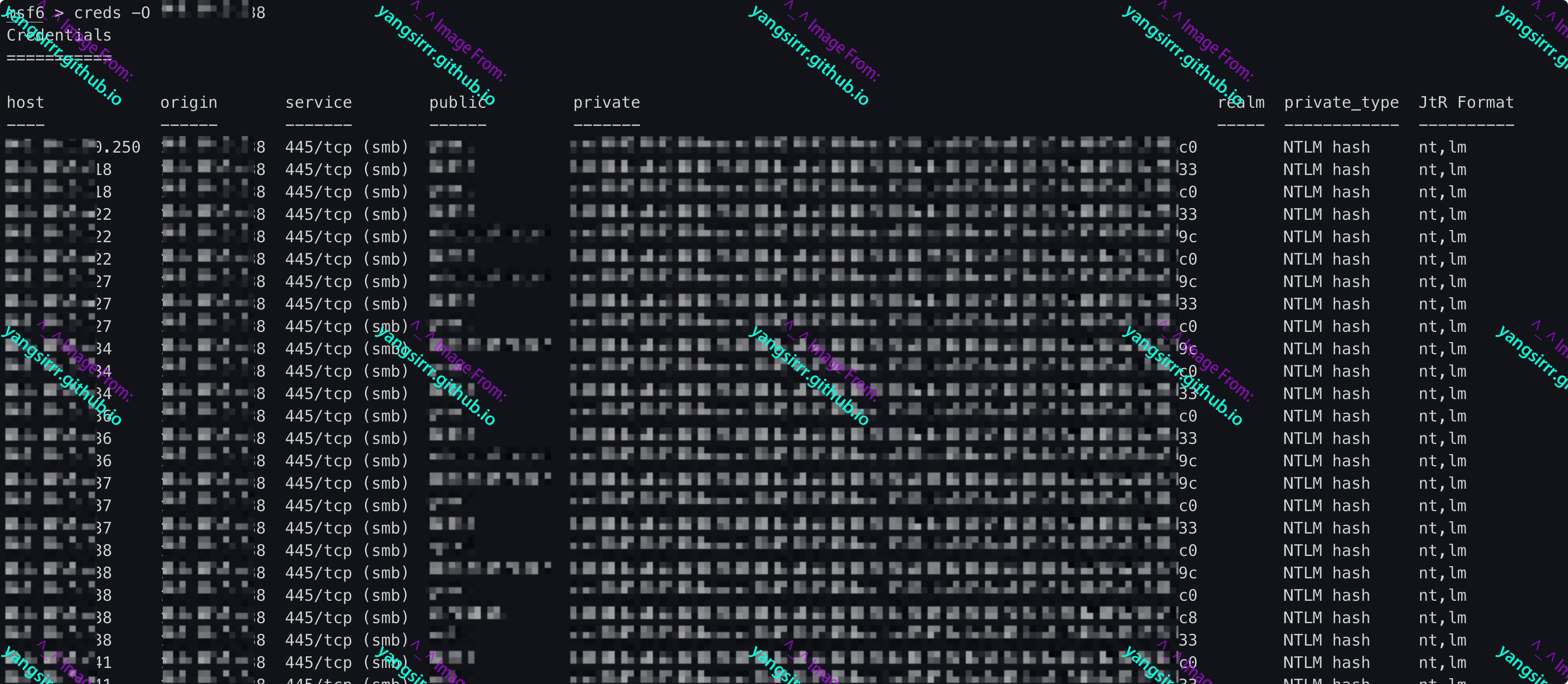
msf6 > creds -O X.X.X.X
Service
Filter by service
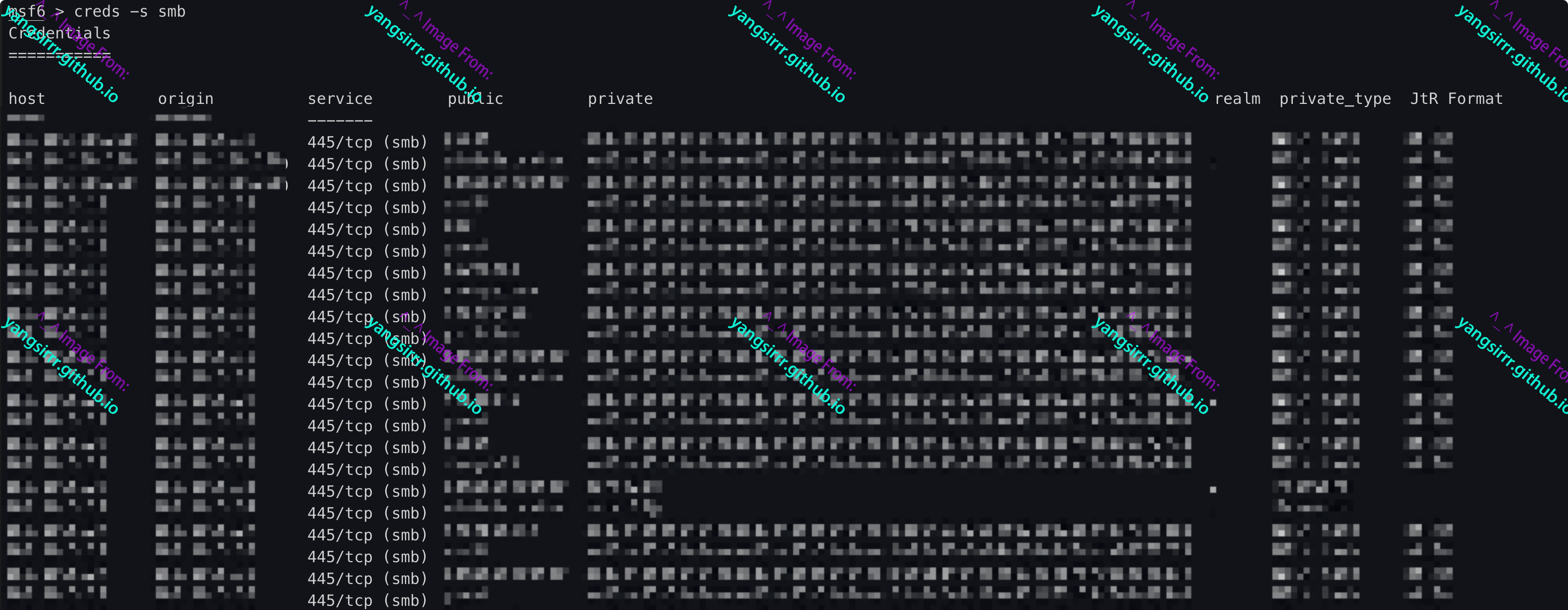
msf6 > creds -s smb
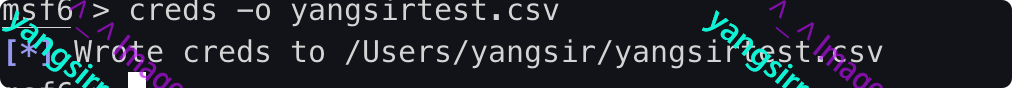
Export
msf6 > creds -o yangsirtest.csv