Some of the words
All cases are authorized legal compliance projects. Do not carry out any penetration attacks without authorization. Please abide by the network security law
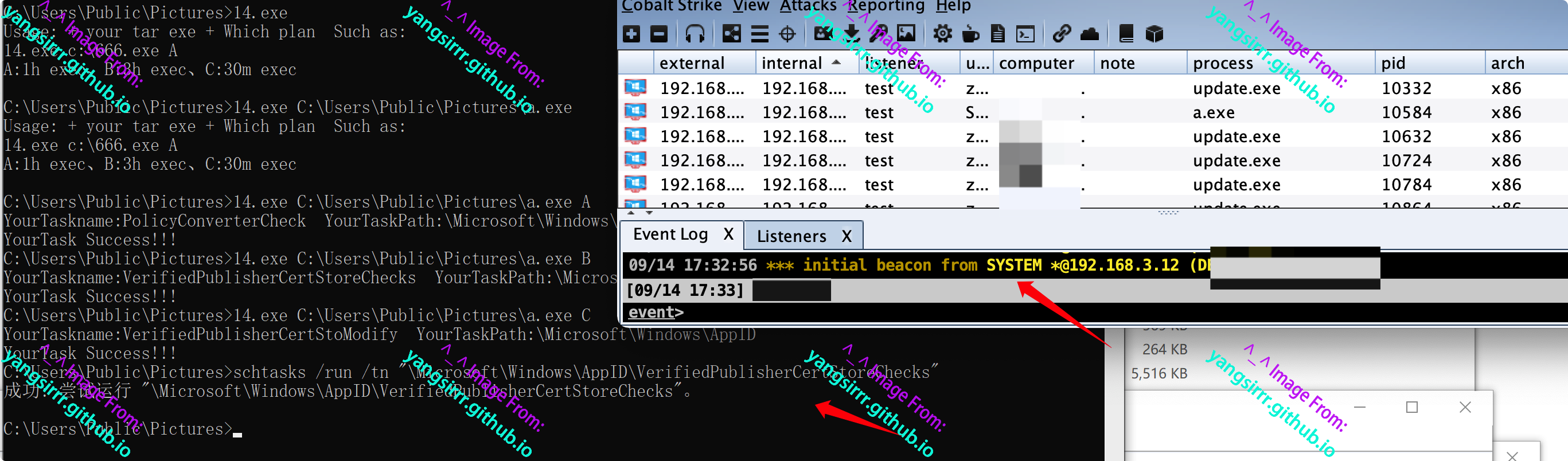
Long time in the past, an authorization, in the process of the red team hit a school infrastructure systems, to improve access to sensitive information to gain more scores, thus progress conveniently find some loopholes, web vulnerability is very regular, mainly based on some logical loopholes to make a case to share, sure, of course, this is not all logical loopholes can add cent
Buy electricity at a low price
Through the student account obtained, I successfully logged in to the infrastructure system and found that I could buy electricity bills. I tried to find logical loopholes
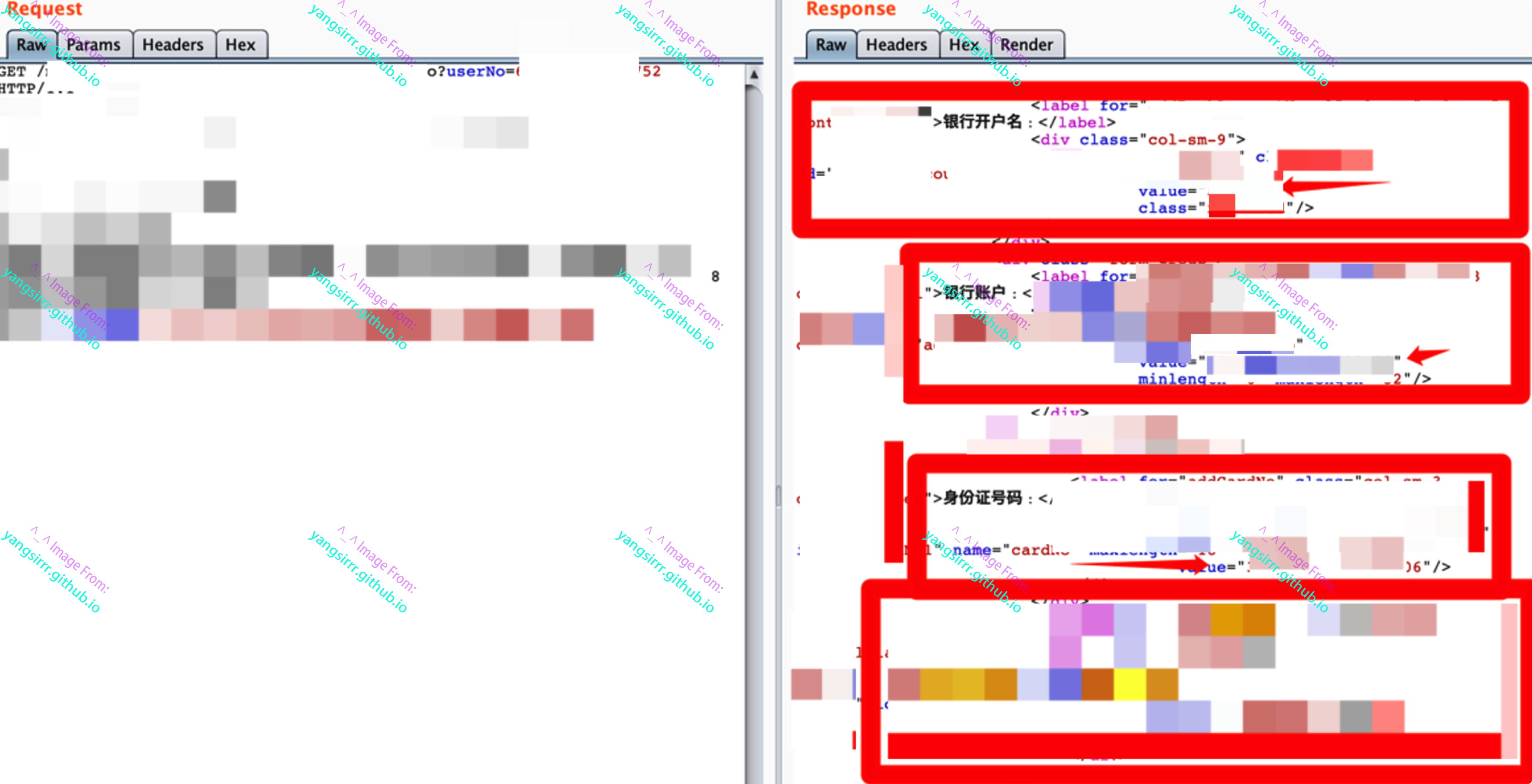
After a few minutes of basic testing, it was confirmed that the place where the order was placed did not verify the order data, but directly received the data submitted by users, so as to realize the purchase of more water and electricity at a low price
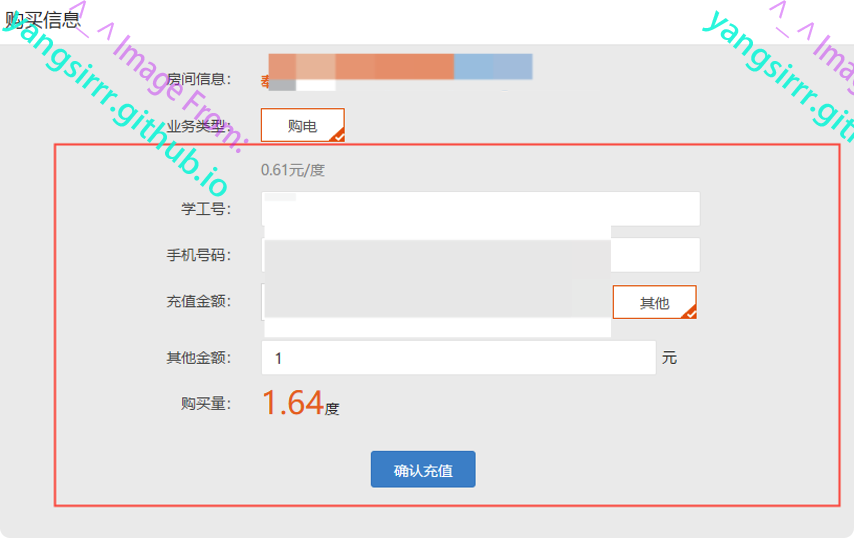
By default, 1 yuan buys 1.64 degrees,like this
After confirming the recharge, catch the data packet
I was just trying to guess, to see if I could find any holes in the logic, because the system was already working through the Web getshell, So change the count parameter to the amount you want to top up, which is also very small to avoid detection

After releasing the modified data package and making automatic payment through the subsequent campus card, you will get the payment voucher and confirm that you can purchase 16.4 amount of electricity with 1 yuan

CSRF added by administrator
After trying, I found that the administrator's account password is also a weak password. When I added the administrator's account, I found that there is also a CSRF vulnerability that can be successfully played
Add administrator functions as follows
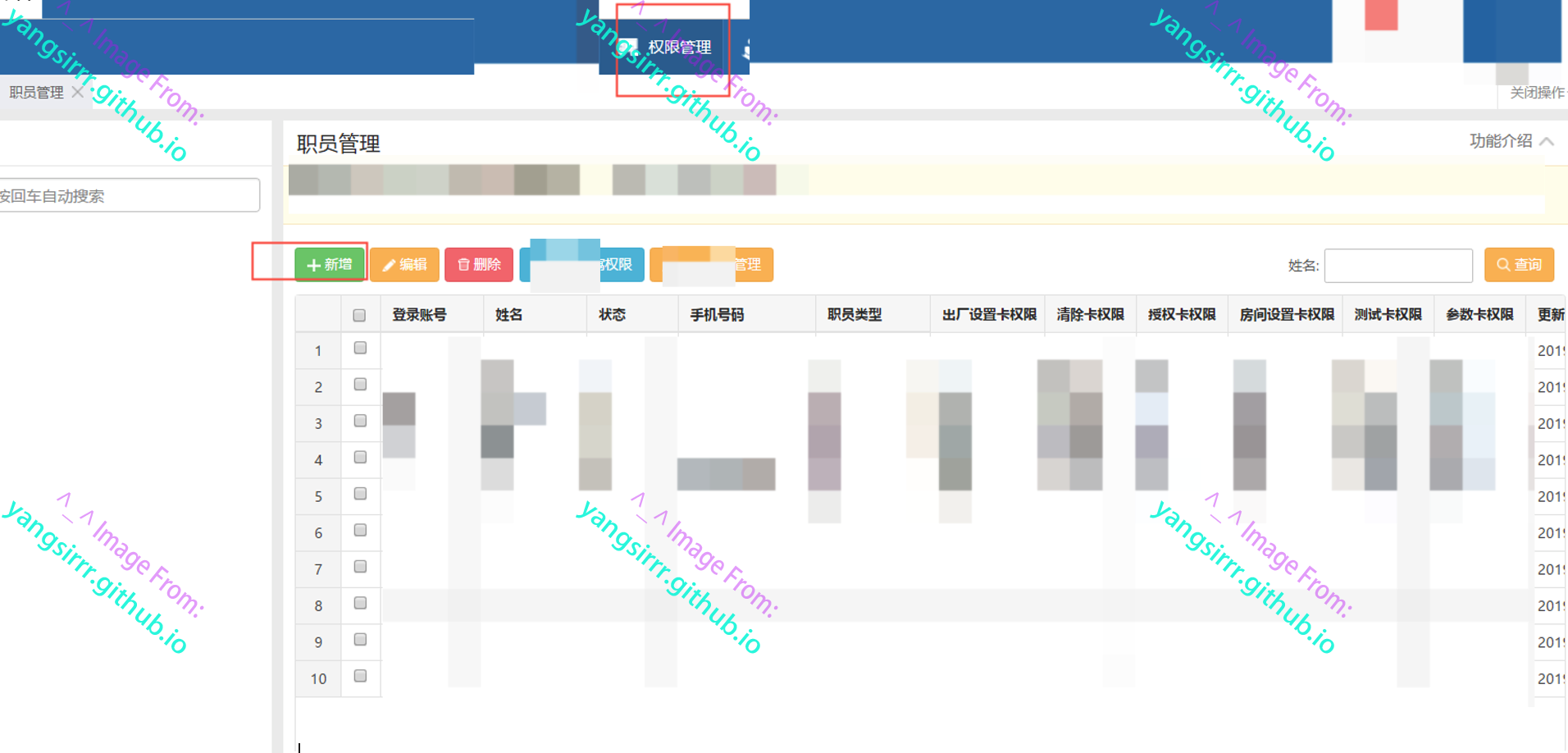
Just fill in the form
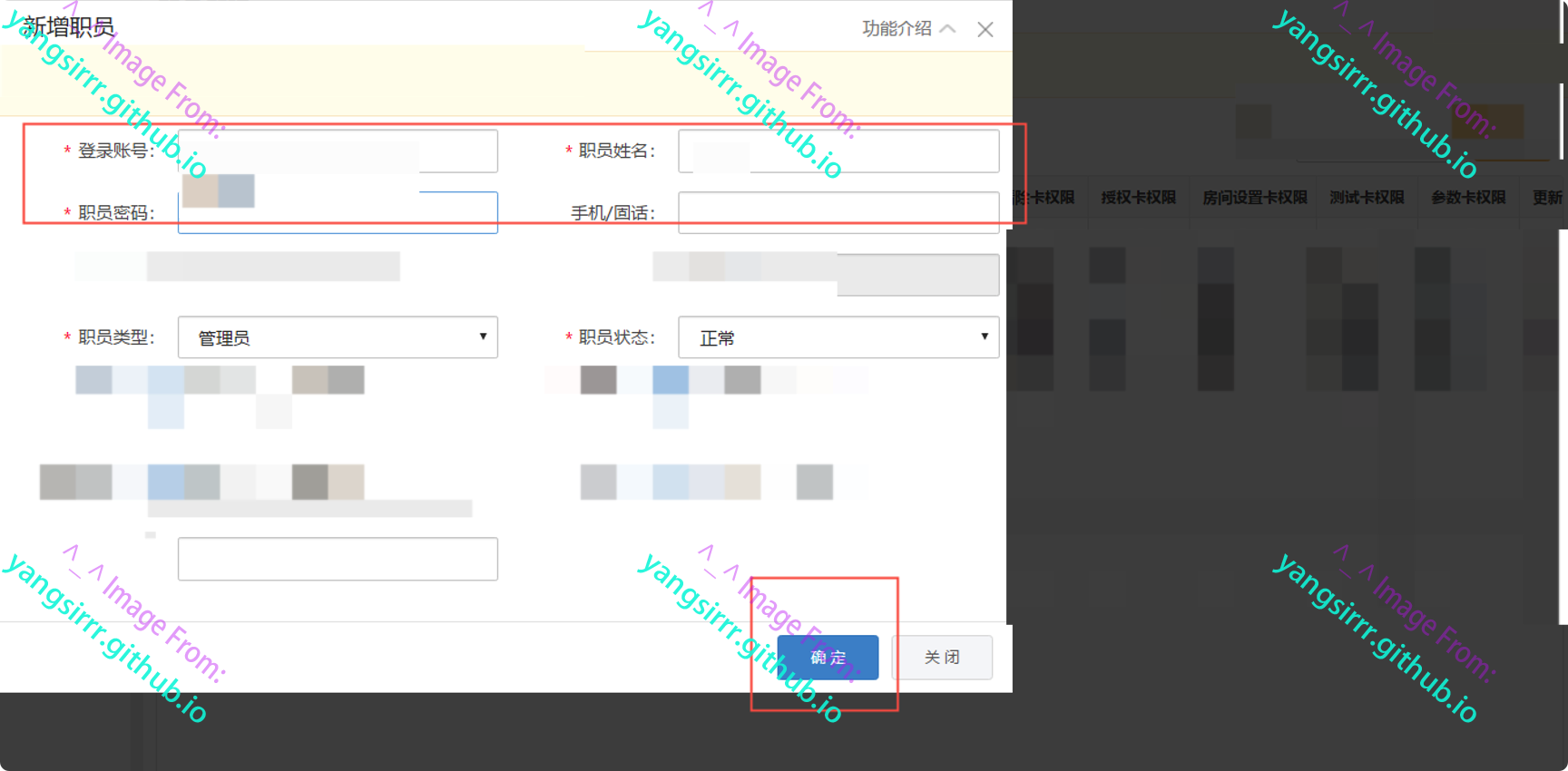
Get data packet
It can be seen here that there is no token, no referer field, and all are transmitted in clear text. The user's account password is controllable and changeable
Don't forget to delete this account when testing again later, or you can change the account name

Very simple, you can use burp to produce CSRF payload directly
The successful confirmation after browser access is as follows

Confirm that the administrator account is successfully created in the background
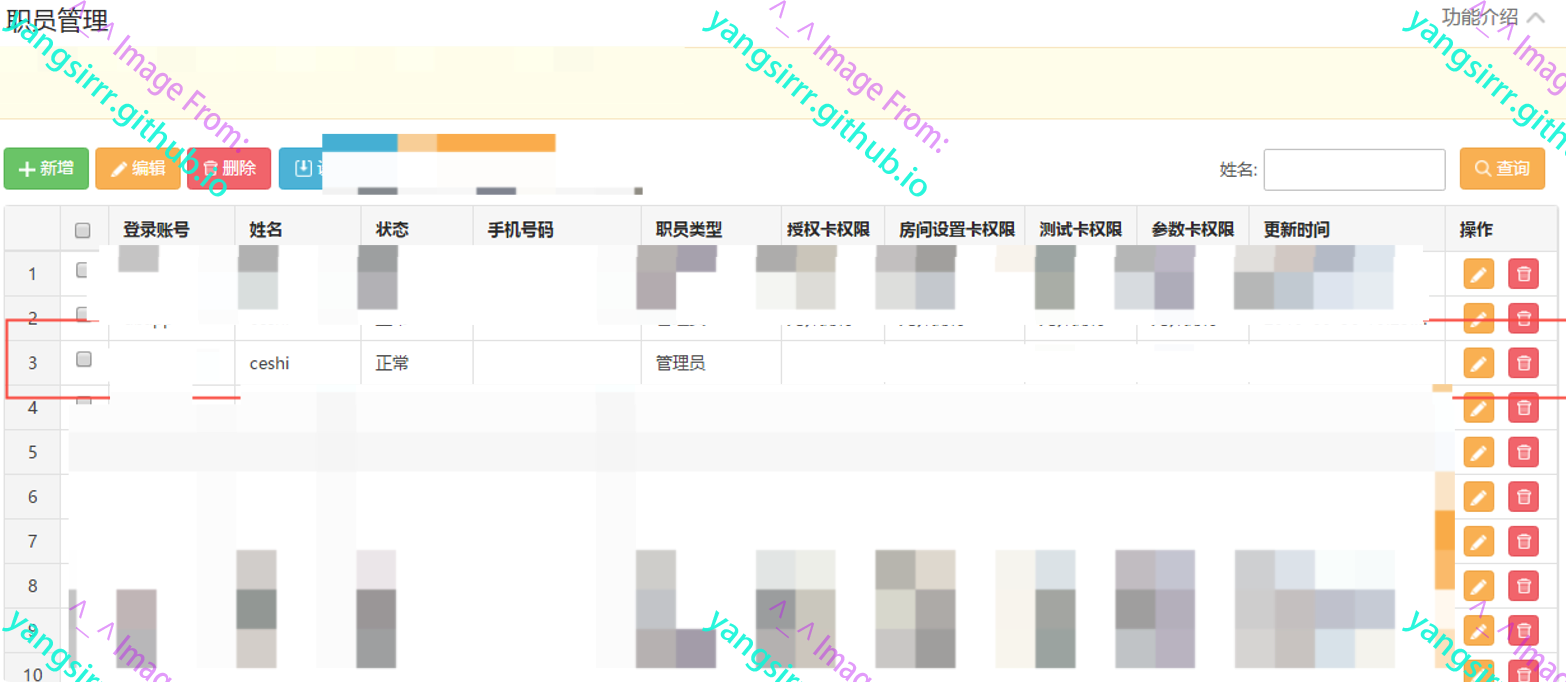
Through a fuzzy query function point in the system, you only need to enter the last name to obtain the staff information of the school. Basically, through this function point, you can obtain the organizational structure of the target, which provides great help for the directional penetration of progress
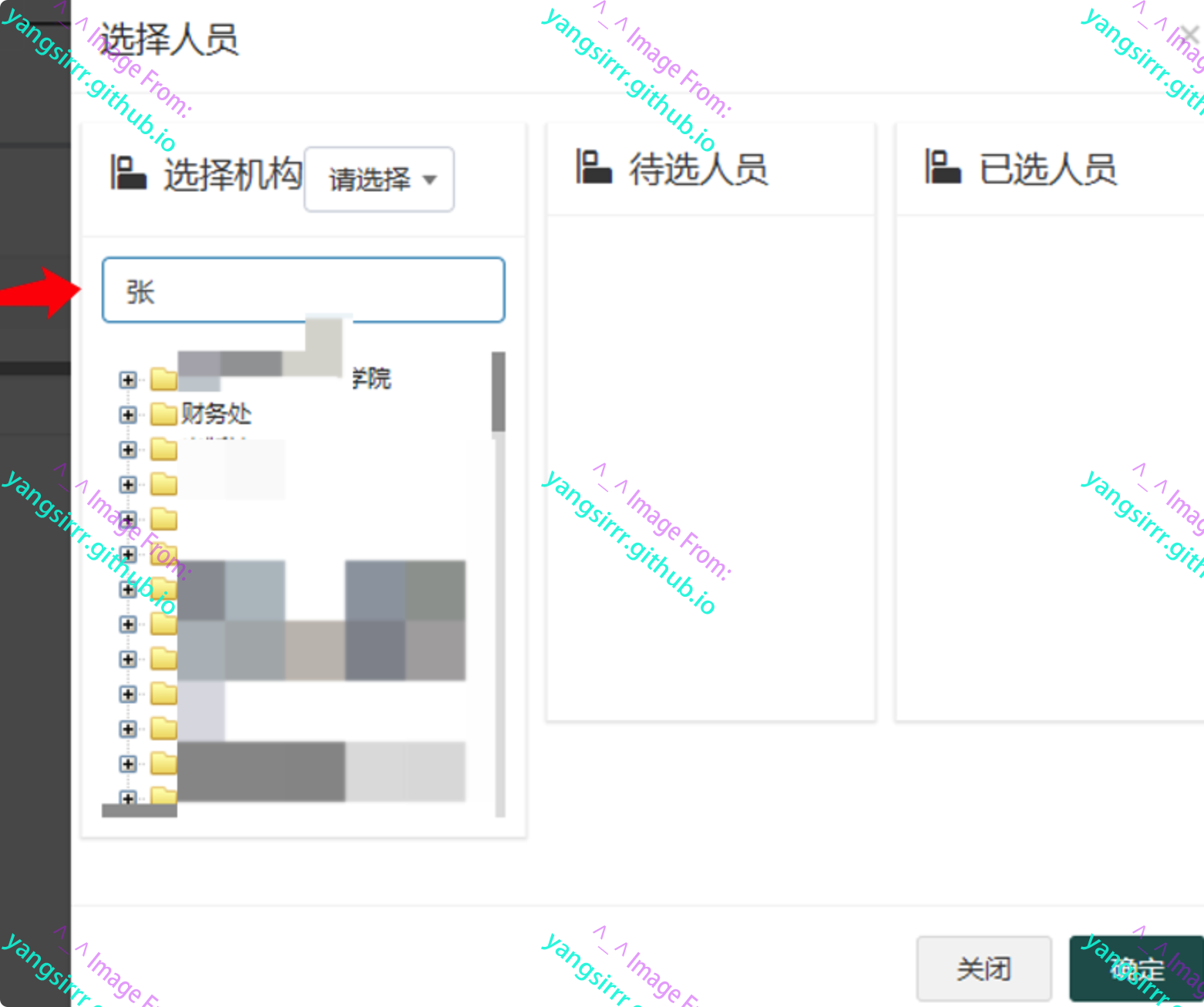
Get data packet, after some testing, it must be passed by post. The get method cannot succeed, but it does not affect the final effect. Just traverse the last name directly

There are a lot of sensitive information, such as name, Department, Email, ID card and mobile phone number. It is basically clear that the target personnel can be located. Here is only a case for explanation
If the Intranet in the shell of this system doesn't move horizontally, I think you must know how to use this information to improve targeted social worker fishing

Later words
In my opinion, in the red team operation, it is important to obtain system permissions, but it is also very important to try to improve and obtain more sensitive information through such infrastructure systems. After all, there must be a lot of people using infrastructure systems. If you can find some logical vulnerabilities involving personal sensitive information, it will provide effective support for progress directed attacks