Some of the words
Most of the time domain set branch of CA and AD authentication system, using the CA certificate issued by the root certificate of the new private key to sign, if an attacker can get the private key, so long to do fake certificates, thus as anyone (without smart card) to the AD for authentication, which is the source of the gold certificate
To use CERTificates for authentication, the CA must issue an EKUOID certificate containing a certificate that allows domain authentication to the target account. When an account uses CERTificates for authentication, AD authenticates the CA certificate specified by the certificate chain object at the root CA and NT AUTH CERTificates

Actual use
Certificates are stored on the CA server. If TPM/HSM is not domain-based hardware protected, its private key is protected by machineDPAPI. If the key is not hardware protected, MimiKatz and SharPDpapi can extract CA certificates and private keys from the CA
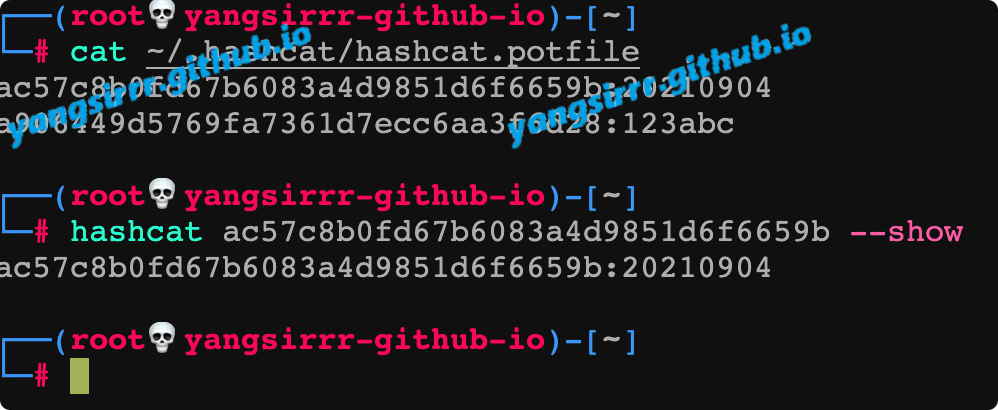
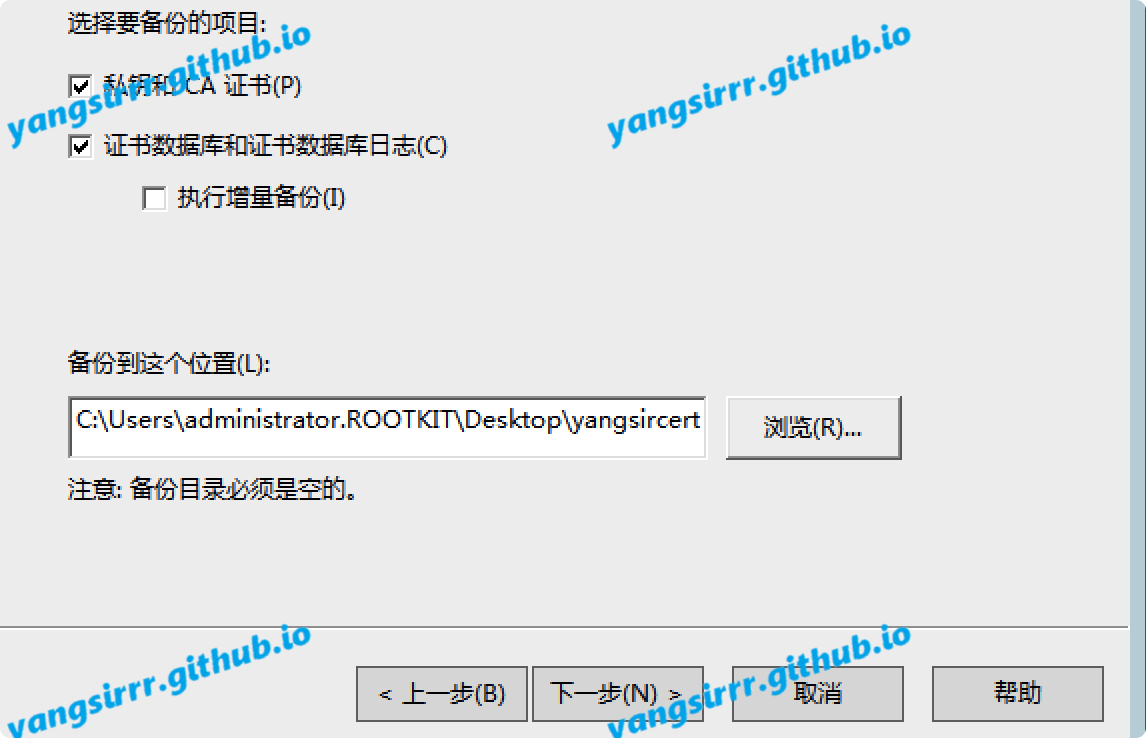
You can export the target certificate and key as follows
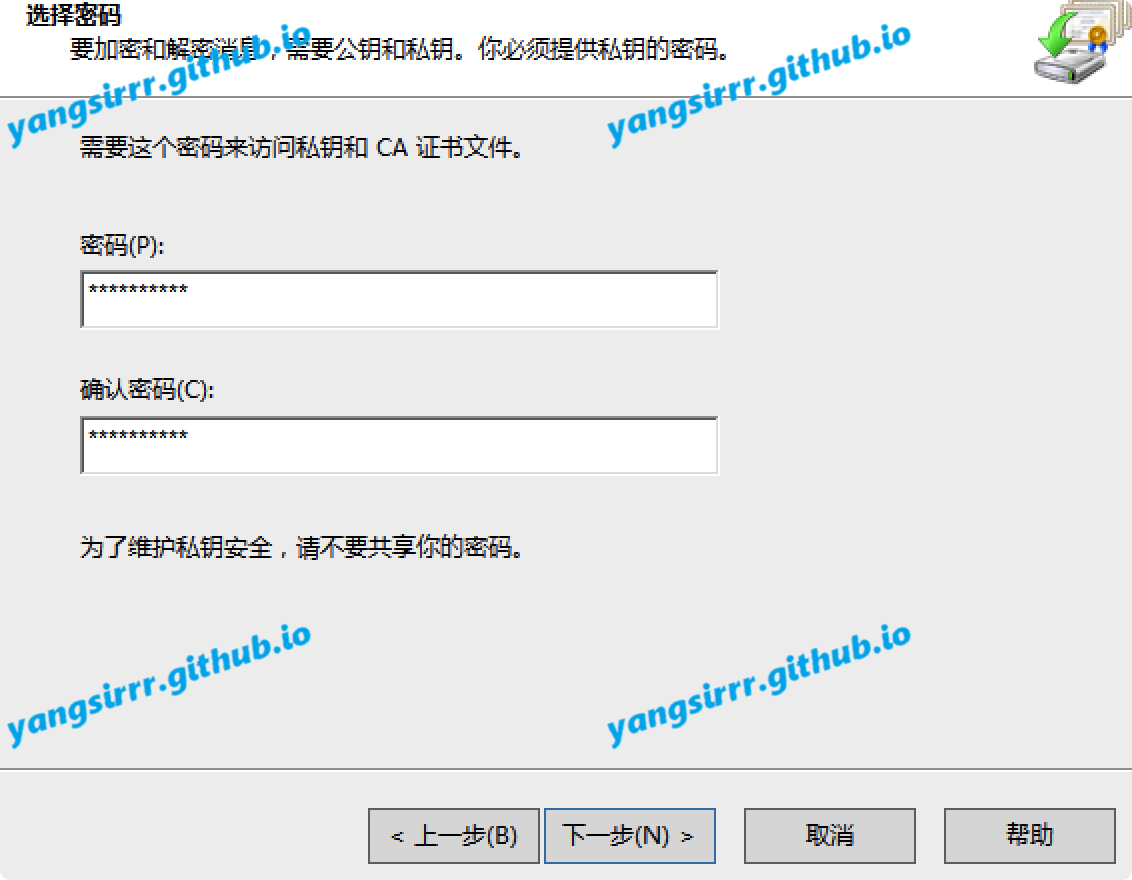
Set your pass like this
You will get your cert like this
Also you can use the mimikatz to get the cert
Use the common domain machine to inputh the cert
Confirm your cert
Now you can fake anyone's cert to use the forgecert

Input the fake cert like this
I think you must be know how to attack again
Such as use the rubeus to askTGT , in addition, because there is no normal issuance process, so it is said that the forged certificate can not be revoked, and the CA server will not find the forged certificate
Note
The process of forging a certificate can be forged on a controlled host
The target user specified when forging the certificate needs to be active/enabled in the AD and able to authenticate, as the authentication exchange will still take place as that user. For example, trying to forge KRBTGT's certificate will not do
This forged certificate will remain valid until the specified end date (in this case, a year) and as long as the root CA certificate is valid (certificates typically start at 5 years, but are often extended to more than 10 years). This abuse is not limited to ordinary user accounts but also applies to machine accounts.
Some supplement
Progress to obtain certificates that have been issued
Get-CertRequest | Export-CSV -NoTypeInformation r.csv

The excel like this
Progress revokes issued certificates
Get-CertificationAuthority <CAName> | Get-IssuedRequest -RequestID <X> | Revoke-Certificate -Reason "KeyCompromise"