Introduction
The project encountered a pit point, some complement, the method of obtaining information to complement, in order to better bypass AV
csvde
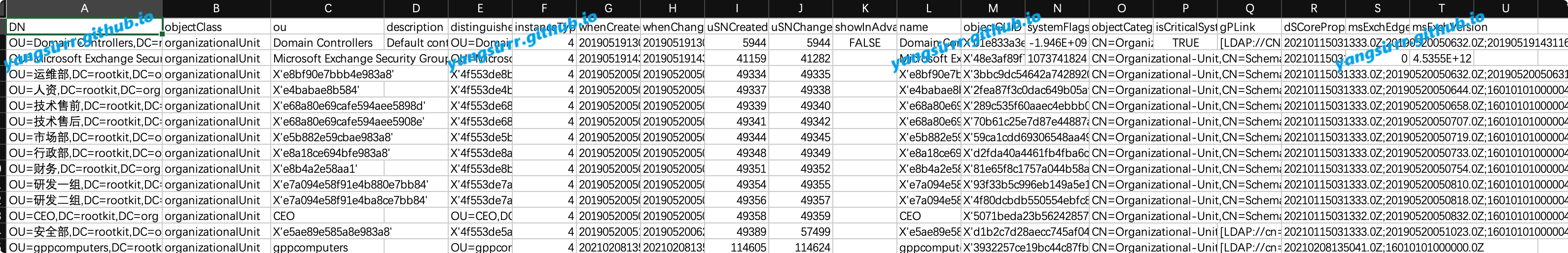
The target information is exported, and the output product is in CSV format. The actual Chinese exported will have garbled characters
Main applicable versions:
Windows Server 2003, Windows Server 2008, Windows Server 2003 R2, Windows Server 2008 R2, Windows Server 2012, Windows Server 2003 with SP1, Windows 8
Operation Manual:
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-r2-and-2012/cc732101(v=ws.11)
Actual use
All information in the domain:
csvde -f 1.csv
Information about all users in the domain:
csvde -f 1.csv -r "(&(objectCategory=person))"
Information about all machines in the domain:
csvde -f 1.csv -r "(&(objectCategory=computer))"
Information about all groups in the domain:
csvde -f 1.csv -r "(&(objectCategory=group))"
Information about all administrator groups in the domain:
csvde -f 1.csv -r "(&(objectCategory=group)(name=Domain Admins))"
All OU information in the domain:
csvde -f 1.csv -r "(&(objectCategory=organizationalUnit))"
All domain user names in the domain:
csvde -f 1.csv -r "(&(objectCategory=person))" -l SamAccountName
All computer names in the domain:
csvde -f 1.csv -r "(&(objectCategory=computer))" -l name
Remote export:
Csvde -s 192.168.3.144 -a rootkit.org\sqladmin Admin12345 -f all.csv
ldifde
Main applicable versions:
Windows Server 2003, Windows Server 2008, Windows Server 2008 R2, Windows Server 2012, Windows Server 2003 with SP1, Windows 8
Operation Manual:
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-r2-and-2012/cc731033(v=ws.11)
Actual use
All information in the domain:
ldifde -f 2.txt
Information about all users in the domain:
ldifde -r "(&(objectCategory=person))" -f 2.txt
Information about all machines in the domain:
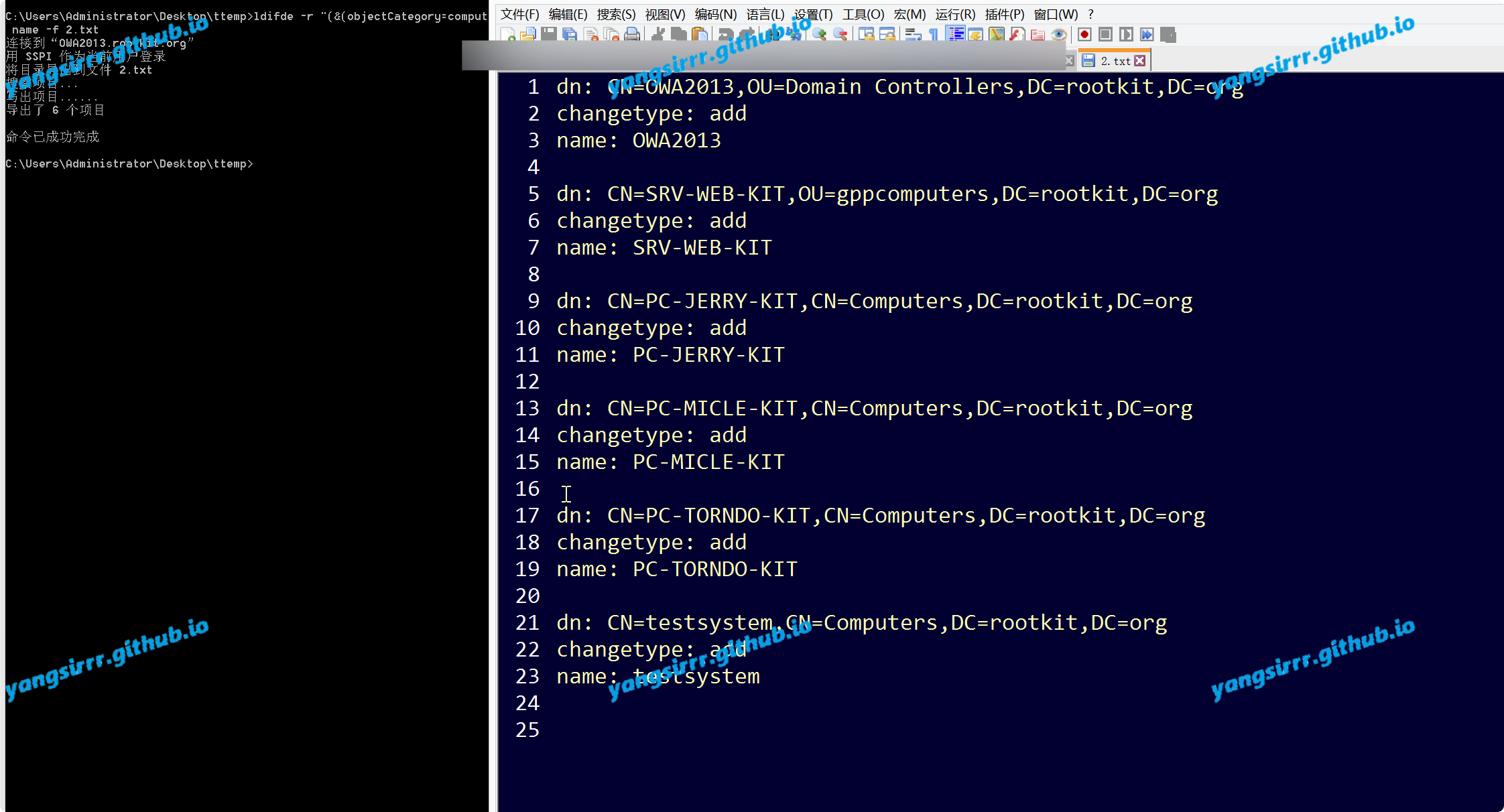
ldifde -r "(&(objectCategory=computer))" -f 2.txt
Information about all groups in the domain:
ldifde -r "(&(objectCategory=group))" -f 2.txt
Information about all administrator groups in the domain:
ldifde -r "(&(objectCategory=group)(name=Domain Admins))" -f 2.txt
All OU information in the domain:
ldifde -r "(&(objectCategory=organizationalUnit))" -f 2.txt
All domain user names in the domain:
ldifde -r "(&(objectCategory=person))" -l SamAccountName -f 2.txt
All computer names in the domain:
ldifde -r "(&(objectCategory=computer))" -l name -f 2.txt
Remote export:
Ldifde -s 192.168.3.144 -a rootkit.org\sqladmin Admin12345 -f 2.txt